Resources For Making the Internet Safer and More Secure
Building a Safer Internet Through Best-In-Class Threat Intelligence and URL Classification Data Services
Thank for visiting the zvelo resource library. From here you may freely access numerous case studies, blog posts, threat reports, datasheets, white papers, videos, and more. We invite you to browse, read, share and download the useful assets and information we have produced and assembled for our markets, covering topics like cyber threat intelligence, phishing detection, malicious detection, network security, brand safety, contextual targeting, web content classification, and more.
Tech Blog
Get zvelo’s perspective on cyber threat intelligence and other cybersecurity related technologies. Topics include network security, threat intelligence, phishing detection, malicious detection, web filtering, web content categorization, and more.
Partner Case Studies
100% partner-focused, zvelo works with OEMs, MSPs/MSSPs, SaaS security providers, ISPs, TELCOs, network security providers, and more. Read how we’ve helped our partners improve their products for sustainable revenue growth.
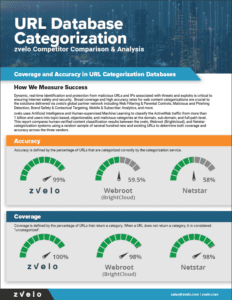
Datasheets, White Papers, & More
Explore These Additional Materials and Resources…
Looking for more information? We also have a number of white papers, briefs, and videos. Here are some examples:
Videos & Webinars
Understanding the CTI Process
Presentation from RMISC Virtual Event, June 8-10, 2021
During this 40 minute presentation, Brad Rhodes, Head of Cybersecurity at zvelo, discusses the Cyber Threat Intelligence (CTI) Process, explaining what it is, who uses it, how it’s used, use case scenarios and why it’s important to organizations both large and small.
Mobile Forensic Investigations
#Forensic #HappyHour with @MarioSamolis is all about #salty #cybersecurity and of course #beer #malware #threathunting.
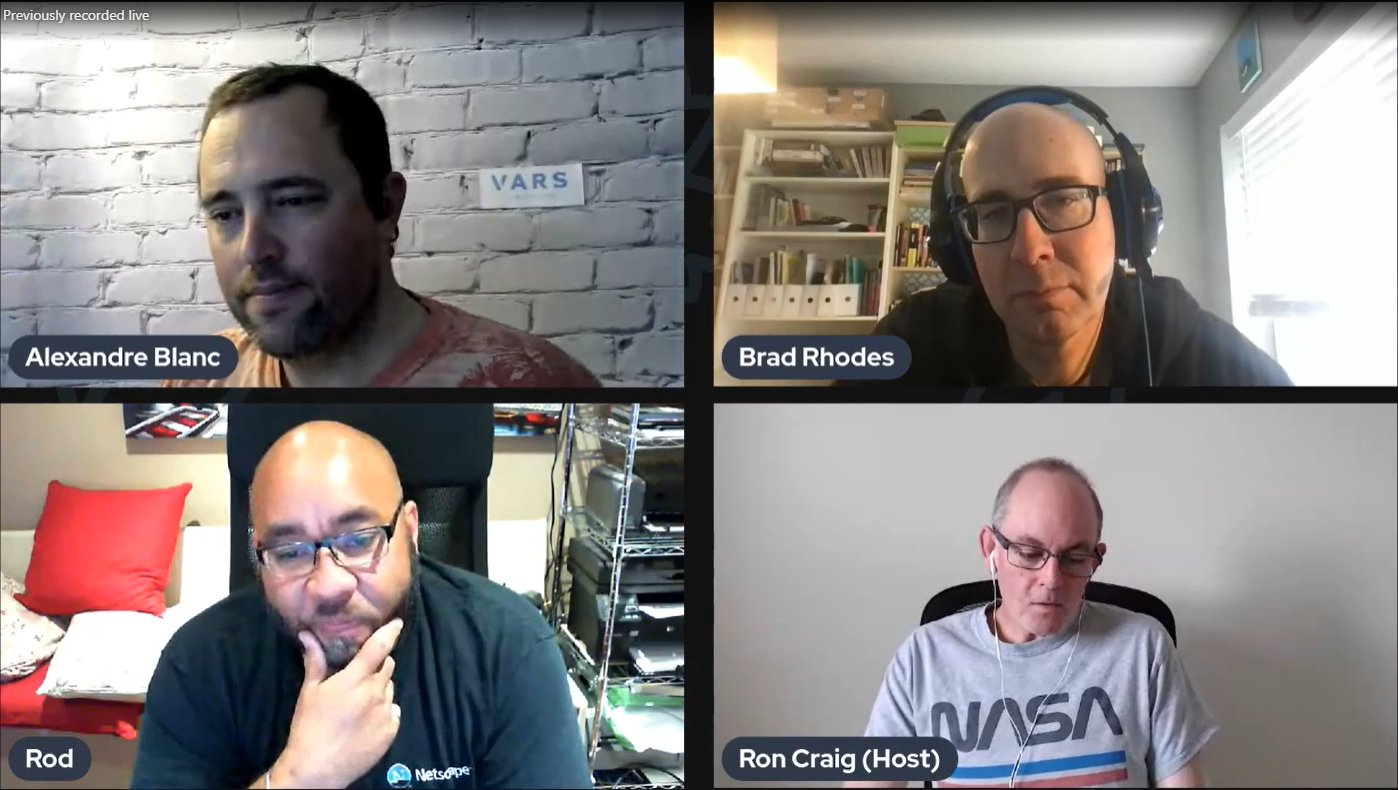
A Dash of Cyber…
Hosted by Ron Craig, and featuring Alexandre BLANC, Rod Lewis and zvelo’s own Brad Rhodes. This 30 minute session is a discussion on how to close the gaps on visibility so you can make better informed decisions to lower risk. Watch the video.
Current Cyber Threats & Impact of Solar Winds
From tools of the trade, to attack surfaces & vectors, to current cyber threats, to the impact of Solar Winds — this presentation is packed with valuable insights for defenders. Watch Now.
Combating Online Influence and Manipulation
This video presentation from the Cybersecurity and Infrastructure Security Agency (CISA) offers valuable insight around combating online influence and manipulation from malicious threat actors.
Emotet: An In-Depth Document Analysis
The video provides a practical defender’s perspective of Emotet’s initial infection mechanisms and how understanding them can better protect your organization.
zvelo and Coronavirus: ProActive Research and Trends
This video presentation from zvelo’s cybersecurity team shares data insights and emerging trends in observed potentially malicious online behavior around the Coronavirus pandemic — geographical naming, redirection to potentially malicious content, domain ages, and malicious traffic via third parties.
Netgear Vulnerability Exploit Demonstration Video
Once you see this vulnerability in action you can easily see how this exploit can be used to create havoc. If someone does take control of your router, they can easily infect or target other IoT devices.
Adventures in Buying Internet Traffic
Mark Ryan Talabis, Chief Security Scientist at zvelo, dives into processes and implications of buying internet traffic, along with ways the industry can combat this problem.

The Battle for Brand Safety
The critical need for brand safety in advertising is not new. To protect their brands, advertisers must avoid inappropriate juxtaposition of ads with competitors, and inappropriate or objectionable content.

Definitions of the Malicious Web
It’s a dangerous world out there in the World Wide Web. Here’s a quick glossary of some of the common security threats you may come across while browsing, web-surfing, and otherwise exploring the vast digital world…