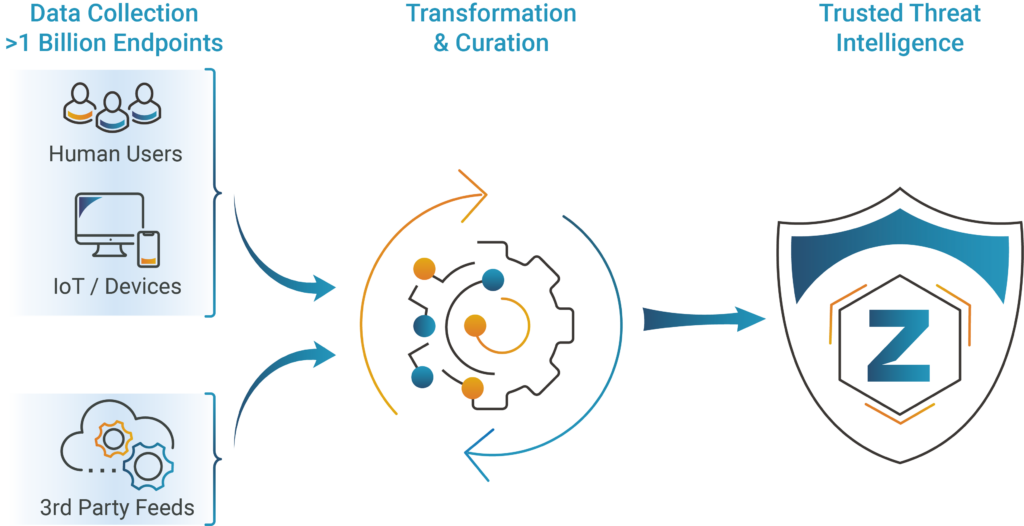
PhishBlocklist™ | Premium Phishing Threat Intelligence Feed
Maximum Phishing Protection That Virtually Eliminates False Positives
PhishBlocklist is a comprehensive phishing threat data feed designed to bolster the precision and effectiveness of your security solutions, enabling security teams to focus their efforts on active phishing threats, and fortify their cybersecurity posture with precision and foresight.