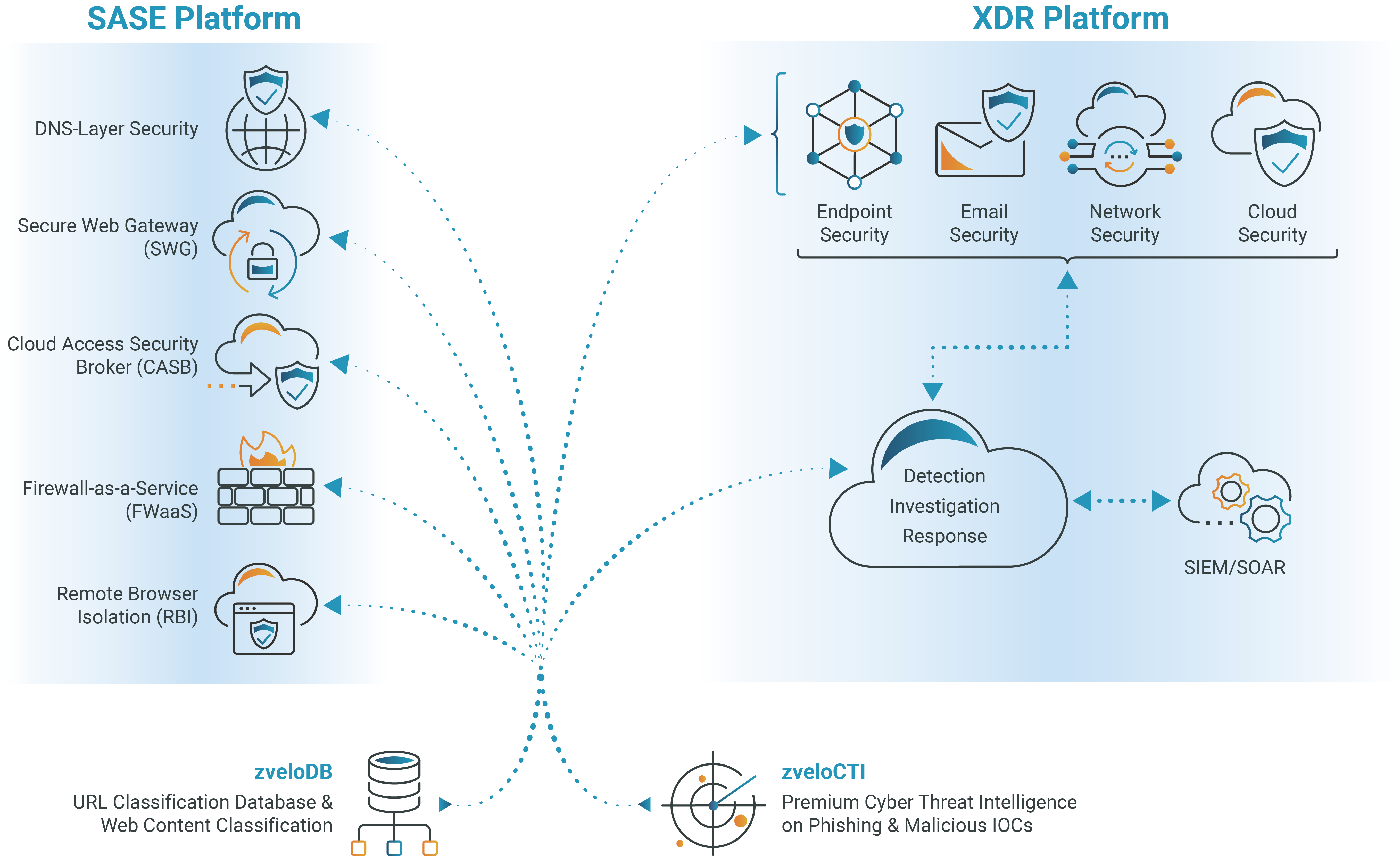
Powering Secure Access Service Edge (SASE) Solutions
Premier Cyber Threat Intelligence, Content and Web Classification Data for Powering Your Entire SASE Solutions Suite
zvelo is the leading provider of data powering the entire SASE solutions suite with premium cyber threat intelligence data, domain database, and web classification services. The zvelo data services provide a single data source, enabling maximum user protection against cyber threats and inappropriate content at significantly lower costs than trying to manage the complexities of ingesting and curating data from dozens of feeds.