DEF CON is one of the largest, (if not the largest), hacker conferences in the world. Held over four days every August in Las Vegas, DEF CON is now in its 24th year and is bigger, better — and scarier — than ever. Our Senior Malicious Detection Researcher, Eric Watkins, participated again this year and provided a great multi-blog brief; giving us a glimpse into the very real, and scary, threat vectors coming out of the hacker world today.
DEF CON 24 – Day 3 & 4: HackFortress or “All Your Base Are Belong To Us” Day
Day 3 Saturday
Saturday I took part in the HackFortress event with the DC719 crew. We had been preparing for this off and on throughout the previous year, so we were pretty excited to attend this event. The event itself is a combination of hacking and gaming, and the basic rules are as follows:
Teams of 10 (4 Hackers + 6 TF2 players) will compete to score more points than their opponents during each 30-minute match. The goal is simple: score more points than your competitors. How you do that is where the challenge comes in. The six TF2 players will be frantically trying to kill, capture and win rounds against the opposing TF2 players. At the same time, the four hackers will be attempting to solve a variety of hacking challenges. As tasks are completed, credits in our ‘hackconomy’ are gained. These can be used to purchase effects to help your team or hinder your opponents in both hacking and TF2.
DC719 playing HackFortress:
The previous year at DEFCON 23, we sat down and played this event without any exposure at all to the event  format, and we got eliminated in the first round. This year, our team worked hard to get familiar with the levels and the very different from stock TF2 gameplay and as a result, we were able to make it to the semi-finals this year! In the semi finals our gamer team won 5-0 but in the last seconds of the game, the opposing hacker team completed a 200 point hack which we didn’t have enough time to recover from. We ended up only three points short of a win overall, even though the gamers dominated all 5 rounds of their portion of the event. Next year we will be focusing on getting those 200 point hacks! Everyone on the DC719 team was pleased to have made it as far as we did and we’re looking forward to next year.
format, and we got eliminated in the first round. This year, our team worked hard to get familiar with the levels and the very different from stock TF2 gameplay and as a result, we were able to make it to the semi-finals this year! In the semi finals our gamer team won 5-0 but in the last seconds of the game, the opposing hacker team completed a 200 point hack which we didn’t have enough time to recover from. We ended up only three points short of a win overall, even though the gamers dominated all 5 rounds of their portion of the event. Next year we will be focusing on getting those 200 point hacks! Everyone on the DC719 team was pleased to have made it as far as we did and we’re looking forward to next year.
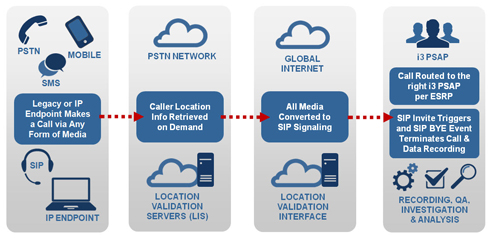
 The Ng911 emergency system talk was given by one of my friends Alex Kreilein from SecureSet, which is located here in Denver. Ng911 is essentially the existing 911 system ported over to VOIP. As a result, there are quite a few vulnerabilities in the system related to VOIP/SIP and tied to the inherent trust issues the 911 system has built into the core of it’s design. Because nobody wants to turn away a call from “little Billy who fell down the well” just because the certificate that’s attached to the call is bad, it’s very hard to authenticate and/or validate a call. Calls to 911 simply must go through to an operator. This makes the entire system vulnerable to denial of service attacks.
The Ng911 emergency system talk was given by one of my friends Alex Kreilein from SecureSet, which is located here in Denver. Ng911 is essentially the existing 911 system ported over to VOIP. As a result, there are quite a few vulnerabilities in the system related to VOIP/SIP and tied to the inherent trust issues the 911 system has built into the core of it’s design. Because nobody wants to turn away a call from “little Billy who fell down the well” just because the certificate that’s attached to the call is bad, it’s very hard to authenticate and/or validate a call. Calls to 911 simply must go through to an operator. This makes the entire system vulnerable to denial of service attacks.
Saturday’s Big Take-away:
The NG911 talk was eye-opening as this wasn’t an area I’d had much exposure to. I’d like to say that this sort of thing is shocking, but after the IoT “return to the 90s” trend, it shouldn’t be surprising that the industry is falling back on some very legacy standards as they transition to the next generation. I’m glad that people like Alex and his research partner are diving into this area, but without their continued vigilance, we could be moving forward into a strange model of implied trust bundled with broken standards. More research and cooperation between the industry standards bodies and the hacker community will be required going forward to ensure we implement something that’s both accessible and secure.
Day 4: Sunday

Sunday morning I attended a talk on discovering and triangulating rogue cell towers. The previous year I’d attended a great talk on the Stingray devices that law enforcement uses to capture and track all cellular devices in a given area and this was a perfect follow up to that talk. Additionally, the author used a Raspberry Pi and a SDR radio identical to the gear I own to implement his detection scheme. While this talk was full of good theory, I found it slightly weak on implementation details, leading me to wonder how much of this theory was actually implemented. Still, the theory was sound and I’m interested in seeing what develops in this sector as a countermeasure to stingrays and IMSI-catcher devices.

The next talk I attended was about physical attacks vs. IoT locks. The speaker spent a good portion of his talk fighting with the video infrastructure which detracted from the content, but once he got going, it was clear he is an SME in this area. He was able to use network attacks to bypass the door locks in an enterprise environment and sent fake video to the video monitoring system to cover his tracks as he did it. While I’ve seen this sort of thing in a piecemeal fashion before, this was the most integrated demonstration I’ve seen combining several attacks into a single unauthorized entry.

The “Backdooring the Front-door” talk was about a vendor named “August” lock. While their lock is quite expensive, the speaker was able to prove that none of the basics had been taken care of in regards to the security of their customer’s data. The speaker was able to bypass almost every single one of the vendors stated security measures. The PDF on this talk is well worth viewing and in light of what I learned here I’ll be avoiding this vendor. The one thing I learned here is to test all surfaces of the attack vector. The speaker attacked the cloud, Bluetooth and basic firmware of the device itself allowing him to completely own the entire product.

The Toxic Proxies talk sounded like it was about proxies but ended up being more about the WPAD protocol itself and how poorly implemented that entire scheme is. Multiple vendors have already patched this, but WPAD should generally be disabled in an enterprise environment as a result of this vulnerability. The worst part about this attack is how easy it make it exfiltrate data from a firewalled environment and even defeat a VPN by leaking hostname and session tokens via DNS to a 3rd party server.
Next week: DEF CON 24 Wrap up.
About the Author
Eric Watkins is our Senior Malicious Detection Researcher and he brings 20+ years of combined information security and IT experience to zvelo. When not haunting DEF CON, Eric leverages his deep knowledge in Information Security by utilizing an extensive background in research, engineering and IT security architecture. Additionally, his unique perspective in penetration testing and IT security audit experience to validate website threat vectors will further enhance zvelo’s malicious detection services.