Word of Caution: Whitelisted Sites are Being Used to Deliver Malware
zvelo’s cybersecurity team is issuing a strong word of caution to organizations which simply rely on using whitelists or blacklists to block malicious sites. This word of caution comes on the heels of an article published by TechRepublic on March 9, based on research from Menlo Security, about how Malicious Cyber Actors (MCAs) are using links from whitelisted sites to deliver malware.
It is All About Trust
In today’s increasingly complex cyber-enabled technology environment it is all about trust. Unfortunately, MCAs are increasingly exploiting that trust utilizing seemingly legitimate resources to prey on their victims. The reason we are seeing MCAs shifting to this tactic is cyber defenses are improving and they know the weak link is the human-in-the-loop. Effectively, MCAs are living-off-the-land in the wild — similar to what might happen in an internal network, utilizing our own tools and trust against us.
How it Works
Cyber actors are using legitimate SaaS sites like OneDrive, Google Drive, Dropbox or iCloud to host malicious documents which are then shared via email. Once a user clicks on the link or opens the “shared” document, they open the door for the MCA. Now on a system, the MCA can deliver ransomware, steal personal information or intellectual property, establish persistence, move laterally, or worse.
Why Whitelisting and Blacklisting Don’t Work
Security measures that work by using whitelists or blacklists to block malware or suspicious sites are ineffective at best and easily subverted by cyber actors. They don’t work because a site is classified as ‘good’ or ‘bad’ based on the base domain. When solutions like Dropbox, Google Drive, iCloud, etc., are generally approved for business use and whitelisted, enterprises have no way to defend against this type of attack because the malicious or suspicious links cannot be identified as problematic.
What DOES Work?
Protection against malicious attacks coming from whitelisted sites requires a solution that provides full-path URL categorization. Full-path categorization enables organizations to obtain URL classifications that are granular enough to detect malicious and suspicious links that are embedded more deeply into a legitimate website’s page structure.
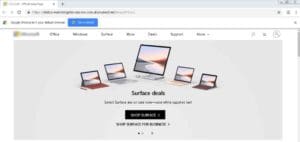
As this issue continues to escalate, zvelo’s malicious detection researchers have been able to identify and isolate numerous malicious URLs that appear within whitelisted sites and which utilize content from popular brands to hook potential victims demonstrating the need for full-path categorization. For example, the screenshot below shows where an MCA scraped and then cloned a website in an attempt to masquerade as a popular name brand. In addition to cloning the website, the MCA is counting on the base domain name to be whitelisted allowing the content to get through to the victim. For realism, some links do work redirecting you to the actual brand webpage.
Bottom Line
If you want to protect your organization from malicious attacks, you need to do more than whitelisting or blacklisting sites for security. The only true defense is a solution which classifies full-path URLs at the page, post or article level.





