The Circle of Trust: A Multi-Tiered Approach to Cybersecurity
In today’s complex information landscape, one of biggest underlying challenges for information technology (IT) and cybersecurity professionals, is how to establish a trusted environment in the age of hypermobility with everything living somewhere in the cloud. From an ever expanding perimeter driven by the need for ‘anytime-anywhere’ access to network resources, to the evolving attack vectors, to increasingly encrypted traffic, it is particularly crucial to adopt a Circle of Trust model in order to maintain compatibility with the ways in which the world accesses, stores, and ultimately, secures data.
Security is predicated on trust. Trust requires the ability to confirm, without a shadow of a doubt, the identity of any individual who may have access to shared network resources. This seems it would be a simple enough challenge to overcome by implementing a Zero-Trust model — trust nothing until such time that it can be verified. While great in theory, applying a Zero-Trust model to real world situations becomes a challenge because there has to be some basic level of implicit trust to install any sort of tool to protect the network.
This is where the multi-tiered Circle of Trust Model comes into play and is the focal point of this article.
What is the Circle of Trust
A Circle of Trust is essentially a user-defined perimeter to draw the lines around which data may be shared, and with whom it may be shared. Implementing a multi-tiered approach within the Circle of Trust, allows for maximum flexibility with varying degrees of trust for accessibility to shared network resources. Regardless of a tool’s particular function, or where that tool sits within the Circle of Trust, it is increasingly imperative for organizations to implement a comprehensive, multi-tiered approach to secure their IT environments.
It is also important to note that one of the other, primary purposes of the Circle of Trust is to also create this multi-tiered approach to fortifying your lines of defenses. For example, if you implement only one, and if that gets penetrated, then obviously everything is at risk and vulnerable to a cyber attack. Many Cybersecurity experts have called for at least a two-tiered approach, but even this is not enough as skilled Malicious Cyber Actors (MCAs) can easily penetrate those tiers, depending on how motivated they are to reach whatever lies behind those lines of defense.
Therefore, the cardinal rule now is to implement defense in depth which requires at least three — and preferably even more — defensive layers. The thinking here is that if the MCA can break through the first layer, the statistical odds of them breaking through each subsequent layer is greatly lowered. Keep in mind that there is no such thing as being 100% immune to a cyber attack.
Businesses, Governments, Educational Institutions, Hospitals – Any and every type of organization is a potential victim; therefore, the only thing that can be done is to mitigate that risk as much as possible through a layered approach addressed by implementing a multi-tiered Circle of Trust.
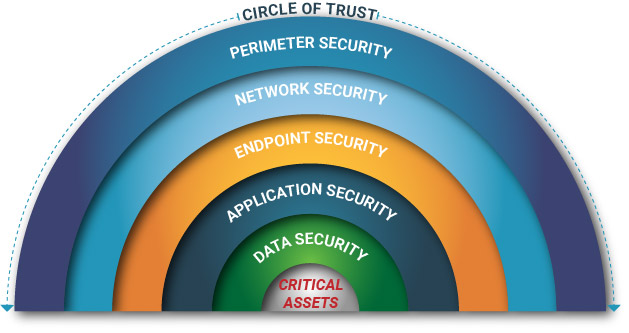
As the the diagram up above shows, within the Circle of Trust, there are five layers of trust (or if you will, lines of defense), and they are as follows:
Perimeter Security:
This is very often considered to be the first line of defense, as it encompasses the entire boundary of the network. For example, this is considered to be a “wall” between the private and locally managed side of the network, and the public side of the Internet. The former is typically referred to as the “Intranet”, and the latter is known as the “Internet”. At this point, you will typically see software applications, such as those of antimalware, and antivirus packages being deployed across end user workstations and internal servers. The main idea here is to filter out malicious data packets which could penetrate deeper into the IT infrastructure. An example of this would be Phishing Emails carrying dangerous malware payloads through file attachments (such as those of .DOC, .XLS, or .PPT) or spoofed links.
Network Security:
Once the perimeter has been secured, the next level of defense, or layer inside the Circle of Trust, is the Network Infrastructure. This can be viewed as a subset of the IT infrastructure, which contains all of the digital assets in an organization. The main goal is here to help protect the shared resources and sensitive data, accessible only to users within the organization who are granted the appropriate permissions. This can also include network-based resources that are used in both the internal and external environments of the organization. For example, you may have remote users outside of the network conducting virtual meetings through Zoom, or any number of other video conferencing tools, and engaging other users working from an office that is inside the network. Given the threats that abound here, it is necessary to make sure that all lines of communication are secured and fortified with the highest levels of encryption. In this scenario, this is where VoIP and Instant Messaging security become critical.
Endpoint Security:
Once the network lines of communications have been secured from the external and internal environments (and even vice versa, as well as those which reside locally in the Network Infrastructure), the next objective in a multi-tiered Circle of Trust security model is to protect the endpoints which reside at the points of destination as well as the points of origination. These include the servers, desktops, laptops, smartphones, and other wireless devices. For example, if an Email message is being transmitted from a remote employee to one that is at the office, the devices used to transmit that message must also be made secure as well. This is actually a part that is often overlooked by many organizations today. As a result, the MCA can easily penetrate backdoors that are left open here, and quite easily deploy malware which can even make its way covertly through the secured lines of communications, and into your Network infrastructure. One of the best ways to secure these endpoints is to make sure that you maintain a well-defined and regular process in terms of deploying and installing the required software patches and upgrades, and even the needed firmware upgrades to them as well. You can even install software-based firewalls onto these endpoints, for even added measure of protection.
Application Security:
Once the Network and Endpoints have been secured, the next layer of defense in the Circle of Trust that needs to be considered is Application security. These are typically the software packages installed to protect users as they conduct their daily job functions (this includes both off the shelf and company created apps). Included in this layer are those applications created by an organization for use by its customers. Because these are usually Web based, and can be accessed from anywhere in the world, securing these applications should be one of the highest priorities for IT Security teams. Some typical Web application security risks include the following:
- Cross Site Scripting
- Denial of Service (DoS) attacks
- SQL Injection
- Cross Site Request Forgery
- Memory Corruption
- Buffer Overflows
One of the primary reasons these applications are at grave risk is because the source code used to create and develop the application(s) has not been thoroughly tested for any vulnerabilities, weaknesses, or gaps. Software developers are frequently under pressure to deliver projects under budget and on time to the client. In order to meet both of these objectives, APIs originating from open source platforms are frequently used. Unfortunately, in many cases these APIs are not adequately tested for security. The end result may be countless undetected backdoors left behind creating an easy opportunity for MCAs to break in. That is why it is crucial to have source code reviews from both the Static and Dynamic perspectives. Even after a Web application is deemed to be reasonably secure, it is still especially important to protect it through the use of other mechanisms, such as Database scanning and Secure Web Gateways.
Data Security:
Data Security can be considered as the ultimate layer of defense within the Circle of Trust and, as such, deserves the most attention on a 24 x 7 x 365 basis. This inner realm of the Circle of Trust typically contains an organization’s most sensitive data and Personal Identifiable Information (PII) records. The types of data can fall under three broad categories:
- High Sensitivity Data. This not only includes PII, but also financial records, intellectual property, and other mission critical data, such as research intelligence gathered about competitors or adversaries.
- Medium Sensitivity Data. These are the type of datasets that can be accessed by most users within the organization to some degree or another. However, if it happens to fall into the hands of a malicious third party, it could still cause subsequent, catastrophic damage.
- Low Sensitivity Data. These are the kinds of datasets which can be accessed by customers or users outside of an organization, through a special login portal which sits behind the main, externally facing website.
Regardless of whatever the sensitivity level may be, it is critical for organizations to safeguard all their data to the maximum extent possible. One of the common tools used to meet this objective is Identity Access Management (IAM). This is where multiple layers of authentication are used, such as using password/PIN combination, an RSA token, and even a Biometric modality (such as Fingerprint and/or Iris Recognition). Organizations should also make use of Data Wiping in case a wireless device issued to a user by the organization happens to get lost or stolen. In this instance, a remote command can be used to wipe out all of the data on the device before it falls into the hands of an MCA.
Conclusions
Overall, this article has examined in closer detail the multi-tiered trust model of cybersecurity we refer to as the ‘circle of trust’, and the most common security technologies layered within. Exactly where each of the tools or applications reside within the Circle of Trust, and how many layers are necessary, is wholly dependent upon each organization’s unique security requirements.





