Security Tools for Building the Circle of Trust: Recommendations for a Well Balanced Defense
In our last post, we presented the concept of a multi-tiered Circle of Trust approach to cybersecurity. As a follow up, this article covers an array of tools which can be deployed to create a trusted, and secure IT environment. There are numerous tools available, but this post will focus on a selection of core tools which can be implemented for balanced security measures throughout the different layers in the Circle of Trust.
- Firewalls
- Routers
- Virtual Private Networks (VPNs)
- Security Information and Event Management
- Intrusion Detection Systems (IDS)
- Intrusion Prevention Systems (IPS)
- Endpoint Detection and Response (EDR)
- Data Loss Prevention (DLP)
The Firewall:
Firewall technology has advanced to the point where there are multiple types, each serving a very specific purpose. These include:
- Proxy Firewalls
- Stateful Inspection Firewalls
- Unified Threat Management (UTM) Firewalls
- Next Generation Firewalls (NGWs)
On a fundamental level, the Firewall carefully examines all data packets that are both inbound and outbound to/from the IT Infrastructure. Its primary goal is to track down and intercept data packets deemed to be malicious in nature and block them at the very first layer inside the Circle of Trust. This is typically accomplished by using a set of pre-established rules set forth by the network administrator. Firewalls have been a trusted means of defense for quite a long time, going back as far as 25 years. The most common notion of a Firewall is that they are simply hardware devices, but they can also be software based as well.
Routers:
A router serves the same basic function as a firewall, but also ensures that data packets are forwarded in the most efficient manner possible so they reach their final destination in the shortest amount of time, without congesting the network. In the real world, a data packet does not just simply arrive at its final destination in one fell swoop. Depending upon how the network topology is configured, data packets typically go from one router to another. The specific route the data packets follow is primarily dependent upon the Access Control Lists set forth by the network administrator.
Virtual Private Networks (VPNs):
VPNs are typically used when connecting from a remote location to the IT Infrastructure to establish a private (as well as secure) network communications flow through an unsecured or public Internet connection. The VPN masks your IP Address so that it cannot be easily intercepted by a malicious third party. Also, as a further layer of protection, the data packet payload is encapsulated and wrapped into another data packet.
Security Information and Event Management (SIEM):
A SIEM is essentially a software-based application that offers the IT Security team a macro view of what exactly is going on in real time, with regards to the network infrastructure of the business. The biggest advantage of using a SIEM is that it enables Cybersecurity professionals to establish a proactive mindset as well as to give them the ability to fight threats on a more timely basis. It also acts as a central repository where everything can be accessed and viewed from one location. There are two primary components to the SIEM:
- The reporting and forensics functionality about security breaches as they happen.
- Provide alerts and warning messages based upon certain thresholds that have been set forth.
The diagram below shows how the SIEM actually works:
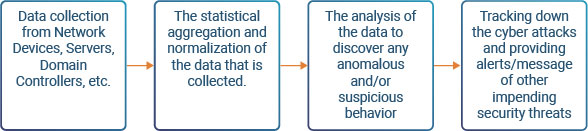
It should be noted that a SIEM is actually a combination of Security Event Management (SEM) as well as Security Information Management (SIM). The former analyzes the log data and other information about network events that take place, and the latter then analyzes all of this information/data and prepares a detailed report for the IT Security team.
Intrusion Detection Systems (IDS):
Intrusion Detection Systems (IDSs) are a type of security tool with two main offerings:
- The Network Intrusion Devices (NIDs)
- The Host based Intrusion Detection System (HIDs)
NIDs are used to analyze the flow of network traffic to and from the IT Infrastructure. HIDs are used to inspect the critical files of a server-based operating system. Regardless of the type of IDS used, the primary advantage is that it can easily be connected to a Security Information and Event Management system (SIEM).
Intrusion Prevention Systems (IPS):
While the Intrusion Detection System can filter out and provide alerts for any looming security threats, the Intrusion Prevention System can actually help to prevent them entering the first layer of defense in the Circle of Trust. What is unique about the latter is that it can be situated directly in between the network line of communications from the point of origin to the point of destination, and vice versa. This is illustrated in the diagram below:
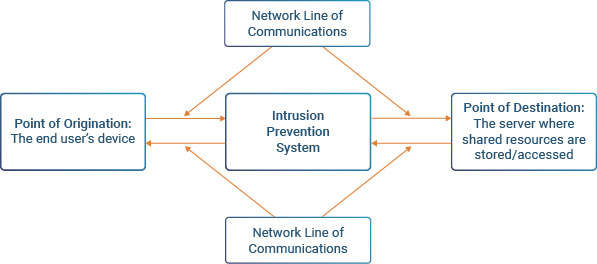
There are actually four types of Intrusion Prevention Systems, which are as follows:
- Network based Intrusion Prevention Systems (NIPS): This kind of device can examine all sorts of network traffic, and pick up and discard any malicious data packets, as can be seen in the illustration up above.
- Wireless based Intrusion Prevention Systems (WIPS): These devices serve as the same function of the NIPS, but instead, they are used strictly for wireless based networks.
- Host based Intrusion Prevention System (HIPS): This is actually a software package that is focused strictly upon the examination and analysis for any kind of malicious behavior for just one host.
- Network Behavior Analysis: This type of tool is strictly used for examining those data packets that stem from network communication flows that are deemed to be abnormal, and are thus indicative a large scale Cyber attack, including Distributed Denial of Service (DDoS), Malware, and/or the abuse of corporate security policies.
Intrusion Prevention Systems offer two types of detections:
- Signature based Recognition: The data packets are monitored in the network flow of communications, compared with known attack patterns that have been discovered previously, which are known as “signatures”.
- Statistical based Anomaly Recognition: In this instance, the data packets are compared with expected traffic patterns, which are often generated by an Artificial Intelligence (AI) system.
Endpoint Detection and Response (EDR):
In many cases, organizations only protect the main network lines of communication, foregoing the necessary steps to fortify the points of origination and destination, referred to as the ‘Endpoints’. For example, this could include the device of the end user and the resources that they are trying to access on the server (this is also demonstrated in the last illustration). If any sort of defense mechanism is deployed at the Endpoint, it’s typically the traditional antimalware/antivirus software package. But the Malicious Cyber Actors (MCAs) can still break through this, and very often, go undetected. This is where the role of the EDR comes into play. With this, sophisticated monitoring of the network activities that take place at the “Endpoint” are collected, analyzed, and stored. A software agent is also installed so that reports can be generated quickly for the IT Security team. Other functionalities of an EDR include the following:
- Filtering: Only real alerts and messages are transmitted, thus further eliminating the chances of any sort of false positives from filtering through. The advantage of this is that it greatly diminishes what is known as “alert fatigue”.
- Advanced Threat Blocking: For the most part, a good EDR system will also prevent the chances of a Cyber attack from precipitating into a much larger one the moment that they are detected.
- Incident Response: EDRs can also be used in tandem with both Threat Hunting and Incident Response activities.
- Multiple Detection of Threats: A good EDR system will be able to simultaneously track down threats of varying degrees, such as Ransomware, Malware, Trojan Horses, etc.
Data Loss Prevention (DLP):
As its name implies, the role of the DLP is to primarily prevent the malicious or unintentional access and hijacking of Personal Identifiable Information (PII), especially when it comes to your clients. Other uses for the DLP also include the following:
- The protection of Intellectual Property.
- Create an environment for data visibility in order to see how information/data is accessed and being used.
- Secure those data records which may reside on the personal smartphones of your employees and in a Cloud based infrastructure.
- Help the organization come into compliance with data privacy laws, most notably those of the GDPR, CCPA, HIPAA, SOX, PCI & DSS.
A good DLP solution will also provide protection for the following types of data classes:
- Data In Motion: This is the flow of information/data that is in transit from one point to another.
- Data At Rest: This is the information/data that is not being used and is archived somewhere in a database.
- Data In Use: These are the information/data records that are being viewed, accessed, updated, or amended.
Overall, there is no shortage of tools or methodologies available to choose from when it comes to securing your IT environment. And, depending on each organization’s risk posture and unique requirements, the list of necessary tools may be more or less extensive than the recommendations provided in this post. The bottom line is that cybersecurity is absolutely necessary. The more tools you have layered into your environment, the more difficult it becomes for MCAs to compromise the system.





