Building an Active Defense with Honeypots, Part 1
The cloud environment is brimming with misconfigured systems, and attackers are highly adept when it comes to finding and exploiting these vulnerabilities as they actively seek newly deployed systems to compromise. And once they identify a vulnerable system, they waste no time in launching an attack. To demonstrate how to use honeypots to understand your attack surface, as well as to highlight the danger of misconfigured and publicly exposed assets, the zvelo Threat Team deployed honeypots on the AWS infrastructure, showing just how quickly attackers will find an unsecured system and attempt to compromise it.
Honeypot Basics
Honeypots are a key Active Defense technique because they allow defenders to quickly identify when they are under attack without having to sift through high amounts of noise and false positives. Honeypot systems are intentionally set up to appear vulnerable so that when an attacker conducts reconnaissance on your network, they’re easily lured into interacting with the system. By design, honeypots should have no normal activity, so anything detected on the system has a high probability of being malicious activity.
Defenders use honeypots to monitor the actions of an attacker before they attempt to compromise actual company systems. Honeypots give defenders a proactive approach to identify what an attacker may be looking for, and what they may do if or when they obtain access to a system. This enables defenders to proactively identify both the attack methods of an attacker, along with the malware they are looking to deliver. Armed with this type of actionable threat intelligence, defenders can import this custom intel into the Passive Defense tools (firewalls, network intrusion detection, endpoint security, etc.) used to defend against malicious actor IOCs by creating rules that will identify attack methods the attacker may use before they can attack a live system.
The Honeypot Set Up
There are many open-source honeypot and honeypot frameworks available. Many of these can be configured and customized to meet specific needs relative to a particular organization. There are also several types of honeypots that can be used depending on what an organization is looking to achieve. The honeypots used for this example are a mix of the high and low interaction. High interaction honeypots are more interactive and include things like a file system to entice the attackers to engage further, allowing defenders to collect more detailed information about an attacker. Low interaction honeypots may just emulate an SSH service to gather login information.
What the Honeypot Attack Looks Like
In this instance, the Threat Team began observing activity almost immediately and within the first 24 hours, the honeypot was attacked more than 150k times.
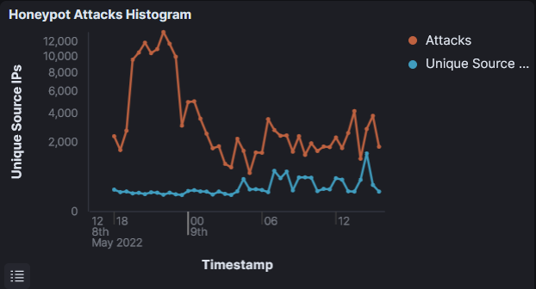
The graph shown above shows the number of attacks and the malicious attacker IPs that were attempting to attack the ‘vulnerable’ system. These attacks may be generated from automated scripts, or they could be manual attacks. In either case, monitoring these honeypot data provides new and actionable threat intelligence that can be leveraged by a variety of different security tools to proactively secure the network.
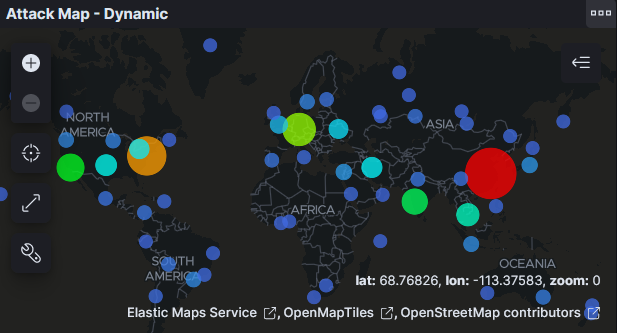
Monitoring tools that mine honeypot logs can provide many different insights into the attacker ecosystem. The graph below shows the countries from which the attacks are being launched which can be used to identify interesting trends. While the country of the attacking IP doesn’t necessarily guarantee the location of the attackers, it does provide insights into where attackers may be setting up their infrastructure or the locations through which they may be proxying their traffic.
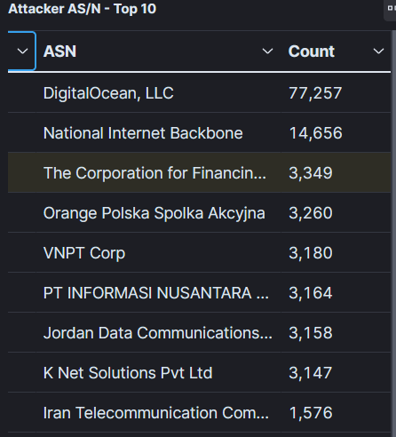
By analyzing the attacking IP data, you can identify the networks from which this attack traffic is originating. The chart below summarizes this information for the period of time in question. These are the most commonly used ASNs that attackers are using to attack this system. This information is useful for identifying patterns and commonly used locations that attackers use to obfuscate their true locations.
Many honeypots will collect attributes that indicate what the attackers are actually doing. The chart below shows the attempted brute force logins on the honeypots zvelo’s threat team used for this post. From this, common usernames that were used to attempt to login to the system were extracted. This information is a useful reminder for defenders to make sure that their systems are not using default usernames — especially those likely to be used by attackers.

Summary
Honeypots are an important tool to help monitor external facing attack surfaces, and provide actionable intelligence to secure an organization’s networks and systems. They also allow defenders to characterize attacker behaviors, patterns and trends, as well as to generate specific threat intelligence that can be loaded into various malicious detection or monitoring systems to proactively secure a company’s network.
In the case of the honeypots used as an example for this blog post, zvelo’s threat team demonstrates how quickly attackers identify newly deployed infrastructure. Additionally, the team identified certain ASNs that attackers are using and the specific IP connections to those ASNs. Depending on a company’s unique business requirements, defenders may be able to configure IP blocks or geo-blocks if there is not a reasonable business need to accept traffic from these IPs, ASNs, or countries. This information can provide cybersecurity professionals a great way to highlight the danger of misconfigured and publicly exposed assets to their organization’s leadership.
Honeypots: Baiting Attackers to Identify Malicious Payloads Like CoinMiners





