In the previous honeypot blog we discussed the benefit of using honeypots as part of an active defense strategy to understand your adversaries and your attack surface. The unique data that can be gathered allows defenders to collect intel that can be ingested into their security tools to proactively defeat attackers before they can compromise production systems. The first post focused on how defenders can use attacking IP data to highlight the danger of misconfigured and publicly exposed assets. This post will continue the theme of using honeypots to understand your adversaries, and focus on how defenders can use honeypots to gather threat intelligence to identify attacking IPs that are attempting to get code execution and deliver malicious payloads like CoinMiners.
Deploying a honeypot on your organization’s network can help increase visibility into what attackers are doing on your perimeter systems that trigger alerts. Additionally, you can identify unique custom payloads that are targeting your network on a system designed to gather that intelligence in a high fidelity manner to quickly import into your malicious detection or security tools such as Network Intrusion Detection Systems (NIDS), Firewalls, and Endpoint Detection and Response (EDR) tools to more efficiently prioritize threats, reduce remediation and response times, and improve your threat posture.
The example below demonstrates a commodity CoinMiner malware attempting to execute onto a honeypot system. In this case, the log file reveals 3 pieces of intelligence on attackers — the attacking IP addresses, the malware delivery sites, and the malicious payload associated with the malware delivery site.
Attacking IP Addresses. These may be either unique or VPN/TOR exit nodes or the true attacker IP address if they did not care to obfuscate it. Although the IP addresses can be easily changed by attackers, blocking them can limit the amount of reconnaissance attackers can perform without using a unique IP address.
Malware Delivery Sites. Unlike the attacking IPs, malware delivery sites are less likely to change which makes them much more valuable in terms of blocking for a longer period of time. In cases where they do change, it’s typically because they are discovered or removed by the hosting vendor.
Malicious Payload. The value in having payload associated with the malware delivery site and the attacking IP can serve a dual purpose. First, it helps threat intelligence analysts correlate information about threat actors. Second, having the malicious payload helps defenders to understand what they are being targeted with, so they can better protect against that type of payload going forward.
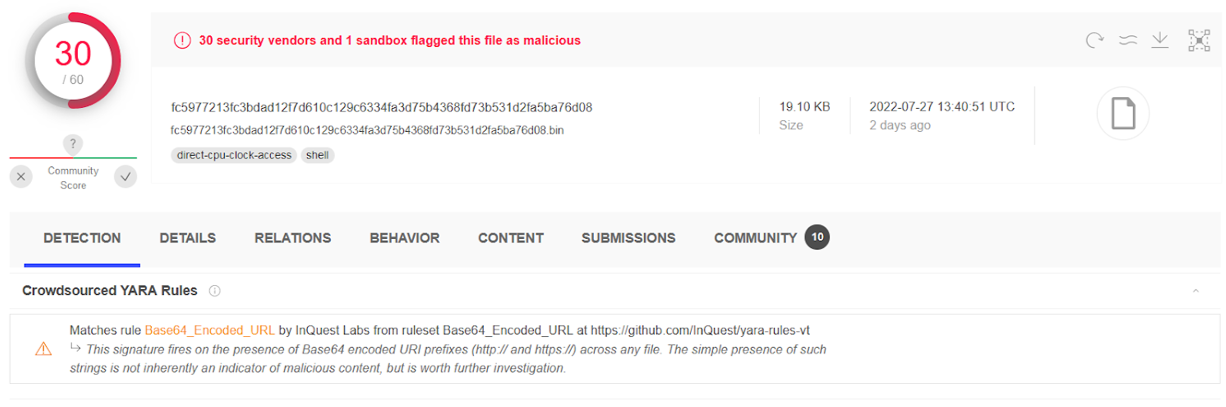
The screenshot below captures data from Virustotal confirming that a hash had been dropped onto one of the honeypots used for the purpose of this blog post.
 If we dig deeper, the graphic below illustrates what we can identify that gives us each of the above pieces of data — the attacking IP, malware delivery site, and the malicious payload which is a CoinMiner.
If we dig deeper, the graphic below illustrates what we can identify that gives us each of the above pieces of data — the attacking IP, malware delivery site, and the malicious payload which is a CoinMiner.
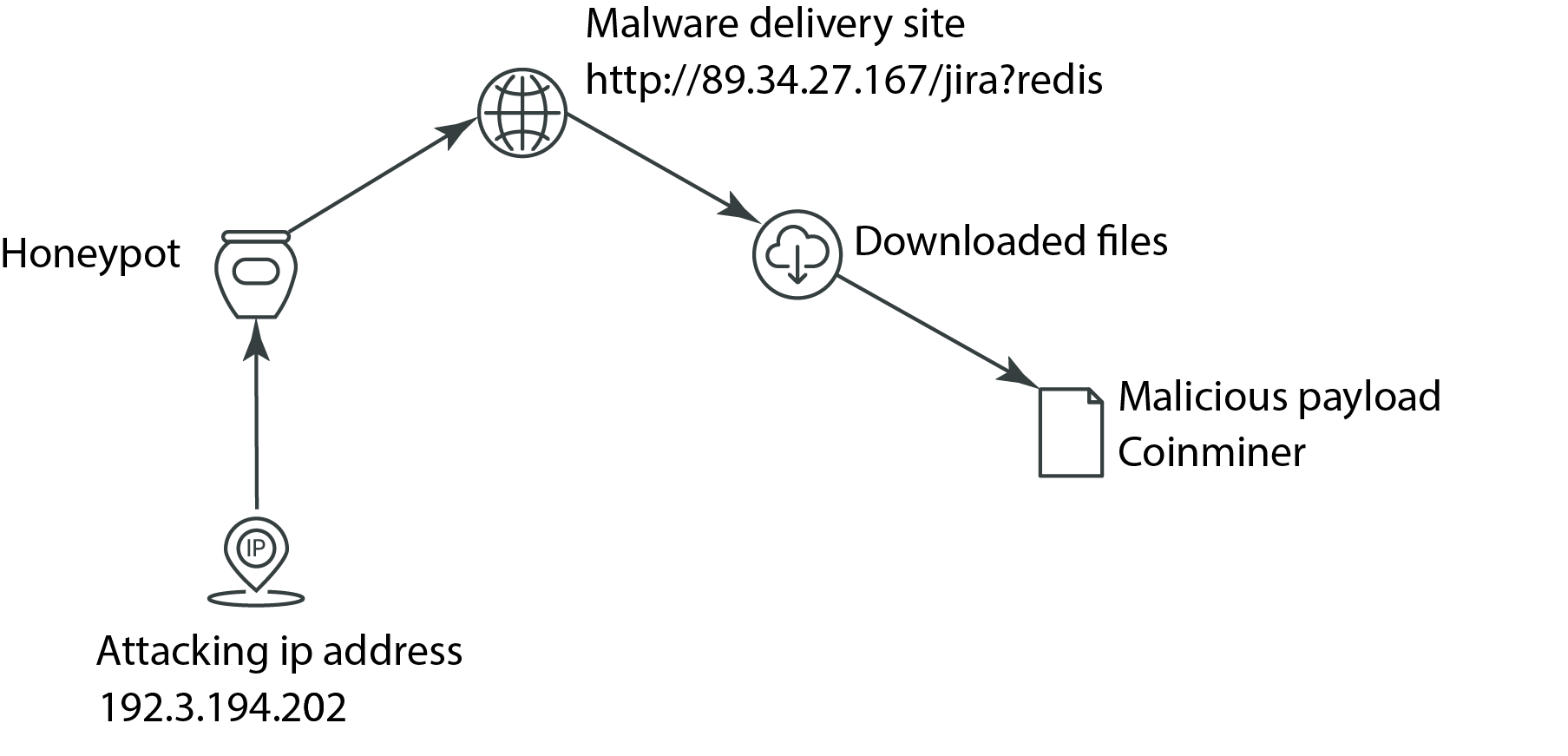 In this particular example, the malicious payload is a CoinMiner which would result in cryptojacking. Coin mining is a legitimate process, but it also requires extensive processing power which is incredibly expensive. Attackers resort to cryptojacking as a way to cut their overhead by hijacking systems to illicitly mine crypto coins. And while it’s not as severe as a ransomware event, it can have serious negative impacts if it runs on a production server. CoinMiners will max out the CPUs on a system which essentially renders it unusable so in addition to the consequences that come from system downtime, companies may experience slow performance across multiple systems, system degradation, or even skyrocketing AWS costs.
In this particular example, the malicious payload is a CoinMiner which would result in cryptojacking. Coin mining is a legitimate process, but it also requires extensive processing power which is incredibly expensive. Attackers resort to cryptojacking as a way to cut their overhead by hijacking systems to illicitly mine crypto coins. And while it’s not as severe as a ransomware event, it can have serious negative impacts if it runs on a production server. CoinMiners will max out the CPUs on a system which essentially renders it unusable so in addition to the consequences that come from system downtime, companies may experience slow performance across multiple systems, system degradation, or even skyrocketing AWS costs.
Attackers and defenders are always playing a cat and mouse game to stay one step ahead of the other but defenders, unfortunately, are always at a disadvantage due to the huge cost and number of man hours it would take to develop and truly secure a network. Instead, defenders have to focus on being proactive and building an Active Defense that can leverage tools like honeypots to stop the attackers before they are able to find a weak spot on the perimeter, or network by blocking them before they can do any damage.





