Over the last 24 hours, zvelo has identified numerous phishing campaigns using personalized and randomly-generated URL paths or subdomains using the recently released predictive phishing detection feature. As a result, PhishBlocklist subscribers have the enhanced capability to block these phishing attacks at the campaign level, before the attack can proliferate. However, it is critical that PhishBlocklist partners understand how to interpret the phishing campaign data they are ingesting to ensure timely and maximum protection for end users.
Brief Background
zvelo recently announced the release of predictive phishing detection to combat automated bot phishing campaigns that use personalized or randomized URLs for each victim. This enhancement enables PhishBlocklist partners to proactively address phishing threats by performing blocking at the campaign level, rather than waiting for the next full-path URL phish to be detected, which would be too late for the intended target, offering no protection. zvelo’s proprietary algorithms use massive traffic data to proactively detect phishing campaigns, allowing customers to efficiently and effectively block these types of phishing attacks and prevent them from proliferating.
How to Use PhishBlocklist Data to Protect Your Users Against Phishing Campaigns
When zvelo identifies a new campaign, a new URL record is inserted into the PhishBlocklist data feed to represent the scope of the campaign that was identified. This record will be at the domain (tld+1) or full subdomain on which the campaign was detected. Once zvelo has identified the campaign and inserted the campaign record into the datastream, zvelo will stop ingesting individual campaign URLs to reduce the amount of repetitive data in the feed that is providing limited value. Thus, it is important for PhishBlocklist customers to interpret the data properly and block accordingly.
For example, if a campaign is identified at the domain level, a record like https://<tld+1>.tld/ will be inserted into the feed. This means that all URLs with this TLD+1 should be blocked whether or not there is a path or a subdomain on the URL. If the campaign was detected at the subdomain level, the record inserted will be similar to https://<sub1.sub2.tld+1.tld>/. Customers should block any url with that host in the URL, regardless of whether or not there is a path. Interpreting the PBL data in this way allows you to deliver the maximum protection against any future/unseen URLs that are part of this phishing campaign.
Current Campaigns
To further illustrate how the PhishBlocklist data should be applied to protect users against phishing campaigns, below are a couple of examples of the current active attacks that have been identified.
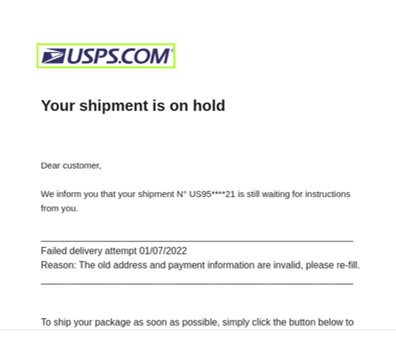
USPS Phishing Attack
The USPS attack is currently active and has been ongoing for at least a couple of weeks. The attack is at the domain level but uses randomly generated subdomains to make blocking on the actual URL difficult which may be why the phishing campaign is still active. There have been more than 14,000 variants observed to date.
Example URLs in the USPS Phishing Campaign:
- https://1f0xqoqohcbc8wumw4vmqddy4tvm.qwo231sdx.club/index/usps/index.htm
- https://ol5u9hcbblt6vhshsh9opac.qwo231sdx.club/index/usps/index.html
In this case, zvelo inserted the following record into PhishBlocklist: https://qwo231sdx.club/. Based upon this entry in the feed, customers should block any URL that contains this TLD+1 in the URL, regardless of what subdomain is observed.
Electrum Wallet Phishing Attack
The Electrum Wallet attack is another example of a phishing campaign that zvelo has identified. This attack is different from the USPS attack in that it is targeted at the IP/host level, rather than the domain level.
Example URLs in the Electrum Wallet Phishing Campaign
- http://92.255.57.10/?login=BOWtvGLsiy4dEmq&legitimation=vjybV7ri8ZsY3kK&privatkunden=nUf3k1gPFSvOQHy
- http://92.255.57.10/?login=VB45MUOmgsX6yiw&id=0G78wxP1UeBCuYD&kunde=1bLBmk7GVSavHgE
In this instance, zvelo inserted http://92.255.57.10/ into PhishBlocklist indicating that any URL with this IP as the host should be blocked, regardless of whether or not there is a path.
Please contact zvelo for more information if you have questions about PhishBlocklist or how to best protect your organization from phishing and malicious threats with premium threat intelligence data.