Threat Feed Evaluation Series Introduction
The process for evaluating threat feeds is fraught with challenges. From the escalating demand for external threat intel, to the proliferation in vendors offering a broad range of virtually indistinguishable threat intelligence solutions in an already saturated market, to skilled cybersecurity staffing shortages, and more, the task of evaluating threat intelligence service providers can easily become overwhelming for even well-seasoned cybersecurity professionals. Complicating the issue further is a lack of universal standards or guidelines on how to evaluate threat feeds. The majority of organizations aren’t sure where to start, let alone know which questions to ask, what to look for, or exactly how to assess the quality, accuracy, and timeliness of a threat feed.
This threat feed evaluation series is designed to provide clarity and guidance amidst these challenges, as well as to establish the right mindset as you begin an evaluation. Our aim is to empower you to effectively evaluate threat intelligence feeds, ensuring you make the most of threat intelligence data in your organization’s strategy to prevent, detect, and respond to threats.
Part 1: Key Considerations for Threat Feed Evaluations
Threat intelligence feeds can be a valuable resource to help security professionals detect, prevent, and respond to cyber threats effectively. However, not all threat feeds are created equal, and evaluating their quality and effectiveness is vital to ensuring your systems are truly protected. This first post in our threat feed evaluation series is focused on the key considerations for threat feed evaluations to help guide you through the most essential elements to assess. For example, do you only want “commodity” threat intel, or do you require premium threat data because your sales teams need a competitive advantage, your customers are relying on the data for protection, or your incident response teams need accurate data for rapid response and elimination of false alerts?
Armed with this knowledge, you will be equipped to evaluate the relevance, accuracy, and timeliness of the data provided by these feeds. Furthermore, we will explore the ease of integration and consumption of threat feeds, as well as the crucial aspect of their actionability. By understanding these key considerations, you can make more informed decisions when selecting threat feeds that align with your organization’s security objectives and infrastructure. Whether you are evaluating threat feeds to enhance your threat detection capabilities or looking to strengthen your cyber defenses, this blog post will provide valuable insights to empower your decision-making process.
Measuring Threat Feed Relevance
Relevance can be measured by assessing the level of applicability, accuracy, and timeliness. Relevance focuses on providing information that is directly applicable to an organization’s unique security posture and infrastructure. By filtering out irrelevant noise, curated threat intelligence enables teams to focus their attention on threats that are specifically tailored to their industry, technology stack, or geographic region. This targeted approach helps streamline the identification and mitigation of relevant risks.
Applicability
The first area to assess when you evaluate threat feeds is the degree to which the threat data is applicable for your specific needs. This can be broken down further into two parts: Coverage and Sources.
Coverage. The first part is coverage, which is what enables visibility into the threat landscape. An organization’s ability to protect users and endpoints depends on having extensive geographical and industry coverage. Ideally, curated threat intelligence feeds that offer a high volume of global traffic reach across as many industry verticals as possible to maximize coverage.
Sources. The second part is to know which sources are used to compile the threat data, as well as how that data is processed and packaged.
zvelo uses a combination of third-party feeds plus proprietary detections and intelligence which are derived from the clickstream traffic from its global partner network of more than 1 billion users and endpoints. While zvelo, like virtually every threat intelligence vendor, leverages OSINT and commercial third-party threat data, it’s important to understand that zvelo is unique in meticulously and continuously curating third-party threat data to deduplicate, validate, and prune inactive threats, as well as to undergo numerous other checks to ensure that the threat data being provided can be trusted.
zvelo offers two different threat feeds: PhishBlocklist and Malicious Detailed Detection Feed. Both offer 99% global coverage for currently active threats and are enriched with valuable metadata attributes that will help to further assess how applicable a threat is relative to your needs.
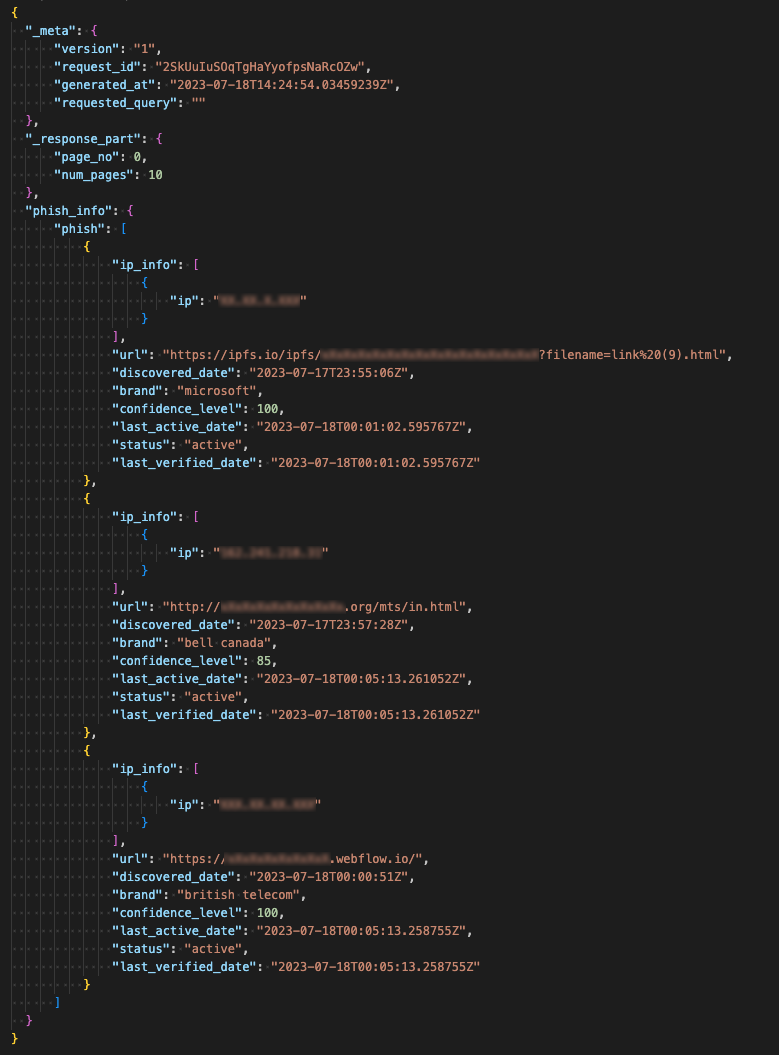
PhishBlocklist provides detections and rich metadata attributes like date detected, targeted brand, campaign detections, current status, and more.
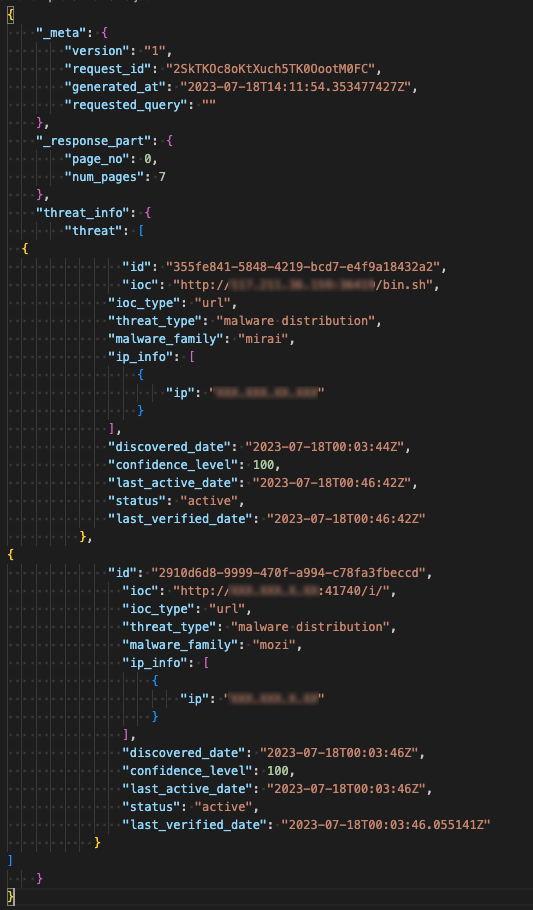
Similarly, the Malicious Detailed Detection Feed provides detections and metadata attributes such as date detected, threat type, malware family, as well as many others that can be used for further analysis.
Accuracy
Accuracy is paramount when it comes to evaluating threat intelligence. High-quality data is sourced from trusted and reliable providers, ensuring that the information is factual, verified, and that the threat is currently active. It goes beyond mere speculation or unverified reports, providing security teams with a solid foundation for decision-making and response efforts. Accuracy can be measured by understanding how the threat feed is processed, curated, and the degree of confidence the vendor has that the data sets contain valid, active threats.
When it comes to zvelo’s threat feeds, producing premium quality threat intelligence with 99% accuracy is extremely complex, difficult, and expensive. It demands substantial resources, such as a global infrastructure to circumvent IP-based or geography-based filtering, automated browsers capable of emulating realistic interactions with web servers fortified with antibot detection techniques, AI-based algorithms that can automatically detect and analyze threats amidst complex scenarios, as well as feedback loops that facilitate the human review of any result that fails to meet the confidence criteria to further verify and validate the data. The end result, however, are data sets with a very high degree of confidence that any of the reported threats are valid, active, and blockable.
Timeliness
Timeliness is the next key consideration for threat feed evaluations. High-quality threat data is up-to-date, reflecting the latest threat landscape and emerging attack vectors. It allows organizations to stay ahead of adversaries by providing early warning indicators and proactive intelligence. Time-sensitive information equips security teams with the necessary tools to swiftly respond and defend against evolving threats.
When it comes to timeliness, the focus should be on active threats vs those which have been deactivated or removed from the web altogether. Security teams waste a significant amount of time and effort to analyze and investigate threats, only to discover that as few as 10% are actually critical and require immediate attention.
Evaluating Ease of Integration
The ease of integration can be measured by assessing how easy, or difficult, it is to ingest a threat feed into your existing SOAR, SIEM, or security solution. Factors to consider include the deployment methods, update frequency, and available feed formats.
zvelo enables access to its threat feeds through a web API which makes zvelo’s feeds easy to integrate and consume while offering clients maximum flexibility in choosing an appropriate update frequency to fit their need. When it comes to feed updates, there are two components: New detections and changes or updates from active to inactive threats. zvelo offers clients the ability to decide how frequently they want to ping the web API — every 5 minutes, hourly, daily, etc. — based on their unique needs.
zvelo’s threat feeds are delivered in json format which makes it very easy to consume and also easy to parse.
Measuring the Actionability of Threat Data
Actionability can be evaluated by determining the degree to which you are able to leverage the threat data to make well informed, strategic or operational decisions in a timely manner. Or, in simple terms, does the threat feed deliver actionable threat data or does it require additional processing, analysis, or enrichment to be made actionable?
zvelo’s curation process ensures that its threat feeds are highly actionable. In other words, every threat included in either the PhishBlocklist or Malicious Detailed Detection Feed is active and blockable with a high degree of confidence.
Following these key considerations can help guide you in making well-informed, strategic decisions when it comes to evaluating which threat feeds best align with your organization’s security objectives and infrastructure. Whether you are looking to enhance your threat detection capabilities or strengthen your cyber defenses, we hope these insights will guide your evaluation and decision making processes. Remember, relevance focuses on providing information directly applicable to your unique security posture, while accuracy ensures that the data is factual and verified. Timeliness allows you to stay ahead of adversaries, while ease of integration and consumption streamlines the integration process into your existing security solution. Finally, actionability ensures that the threat data provided is ready to be acted upon without requiring extensive processing or analysis.
Staying ahead of the threat landscape requires being proactive and selecting threat feeds that meet the highest standards of relevance, accuracy, timeliness, ease of integration, and actionability.
Next Up: