Thousands of Legitimate Websites Compromised
The cybercriminals involved in this campaign are primarily targeting pornographic search terms. Poisoned searches involve celebrities and porn stars nude, nudism, sex parties and searches that are much more lewd and inappropriate. Obfuscated javascript is used to redirect a visitor to Rogue Anti Virus and other malicious payloads.
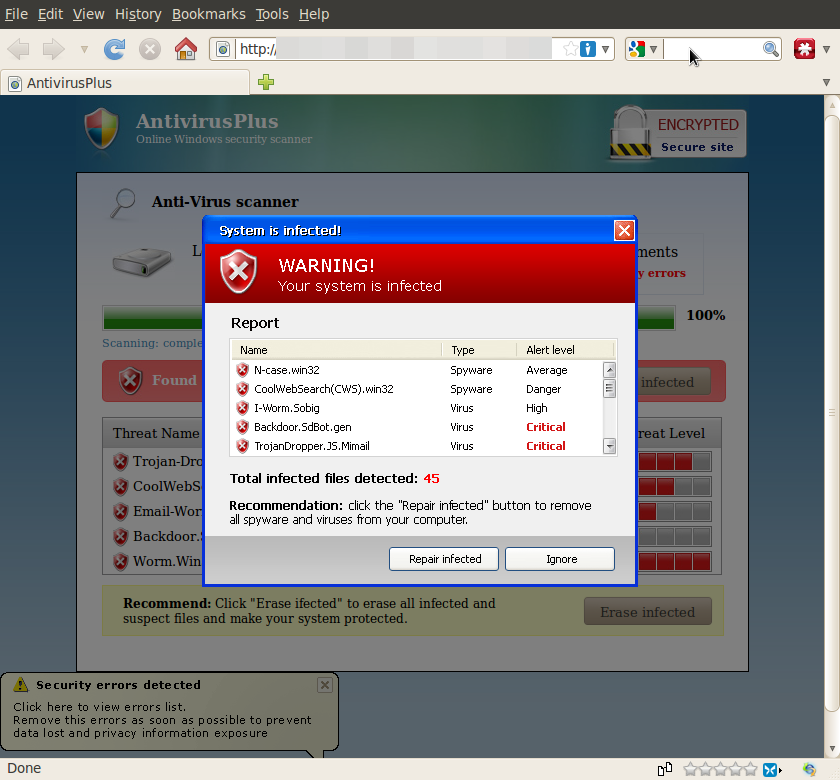
At the time of writing most infected pages lead to the rogue anti virus scam “Antivirus Plus” as shown below.
Cybercriminals are increasingly infecting legitimate sites rather than creating their own websites. Otherwise honest sites that have been compromised have a much longer lifetime with which to infect visitors and have a better chance of passing undetected through web filtering technologies, infecting a greater number of users. Sites created specifically for malware distribution or malicious intentions can be shut down by the domain registrar or ISP much more quickly than a legitimate site that’s been compromised. With granular URL classifications, zveloNET™ is able to detect and block these sites before a user is infected.
Based on the number of different platforms and web server software that are infected in this specific attack (recognized by the recurring malicious code it uses), it’s most likely the sites were compromised using stolen FTP credentials. For webmasters out there, be sure to keep your FTP passwords secure, and don’t save them in popular FTP programs where they can easily be harvested by attackers. If possible, use SFTP and key based authentication instead of the less secure FTP protocol. Also avoid passwords that are found in the dictionary or are common place or person names (even adding a number to the end will not protect you from a determined brute force attack).
Further details are available for security researchers interested in the specific attack and related code. Right now, zvelo estimates that the attack affects 3,200 websites.





