DEF CON is one of the largest, (if not the largest), hacker conferences in the world. Held over four days every August in Las Vegas, DEF CON is now in its 24th year and is bigger, better — and scarier — than ever. Our Senior Malicious Detection Researcher, Eric Watkins, participated again this year and provided a great multi-blog brief; giving us a glimpse into the very real, and scary, threat vectors coming out of the hacker world today.
DEF CON 24 – Wrapping it all up 
One of the biggest overall themes I noticed at DEFCON 24 has to be the concept of weaponization. In previous years there was a slightly larger focus on jaw-dropping zero day hacks that would prompt vendors to release massive rafts of patches. What we saw this year was the refinement, scaling, and weaponization of some things that were introduced in previous years. This was evident in several talks as well as the DARPA Cyber Grand Challenge. Info on CGC here: https://www.cybergrandchallenge.com/
 In the CGC, DARPA asked teams to take their intel and build their techniques into high-performance computer systems that could do the hacking on their own. This same trend is being held in the Active Directory audit world where older tools such as PowerShell are being combined with graph theory to map AD using very low-level account permissions. This new tool is called BloodHound and details on it can be found here: https://github.com/adaptivethreat/bloodhound
In the CGC, DARPA asked teams to take their intel and build their techniques into high-performance computer systems that could do the hacking on their own. This same trend is being held in the Active Directory audit world where older tools such as PowerShell are being combined with graph theory to map AD using very low-level account permissions. This new tool is called BloodHound and details on it can be found here: https://github.com/adaptivethreat/bloodhound
This trend toward weaponization is concerning because it’s taking previously obscure or time consuming processes for subverting security and making the technique available to script kiddies. This can help increase an enterprise security posture, provided they are audited by a good team of pen testers.
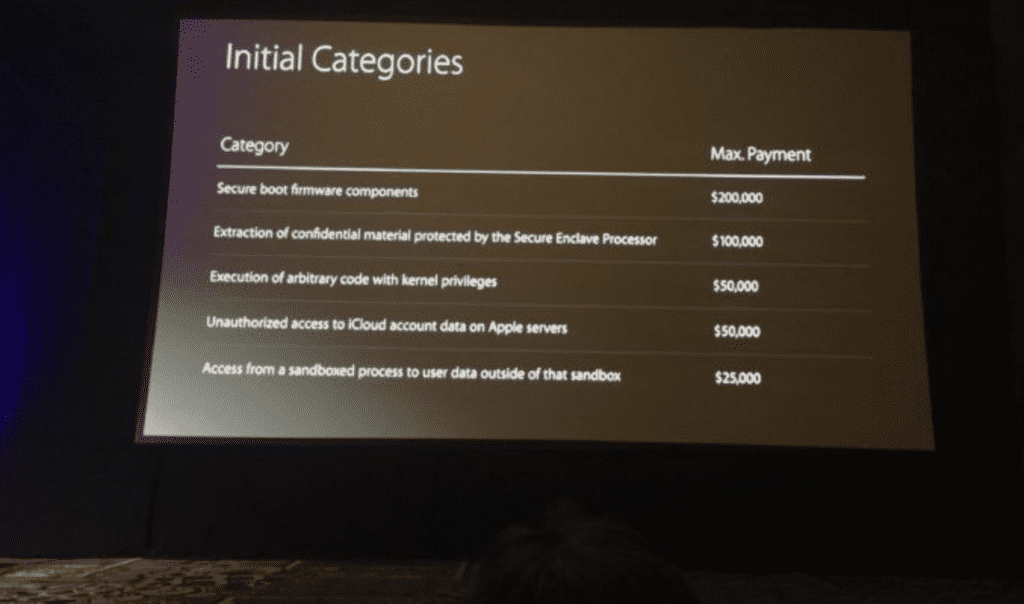
 Another trend that was being talked about at DEF CON this year was the debut of Apple’s bug bounty program. Apple had been giving out hardware to security researchers in the past and they finally came out with a formal schedule for actual cash payments. While this was introduced at the BlackHat conference, several speakers made reference to it, and the topic came up in several casual conversations I had on the floor.
Another trend that was being talked about at DEF CON this year was the debut of Apple’s bug bounty program. Apple had been giving out hardware to security researchers in the past and they finally came out with a formal schedule for actual cash payments. While this was introduced at the BlackHat conference, several speakers made reference to it, and the topic came up in several casual conversations I had on the floor.
Apple’s effort has been viewed by the entire hacker community as “greedy” and another company came out less than a week later with a much better program, paying almost double for the same bugs.
This escalation is exactly what isn’t supposed to happen with bug bounty programs and it’s widely viewed as a misstep by Apple. I can see this negatively impacting Apple users in the future as things will take much longer to get fixed.
As expected, Defcon 24 was awesome this year, and not just because it validated our position that IoT is going to continue its trend to be a huge vector for security breaches in 2017. The way we see it, both enterprises and consumers will need to work together to ensure new the IoT devices they purchase and install in their environments are properly secured. And, given the security barriers that the IoT landscape presents, this will be an ever-increasing task for the average end user.
See you there next year!
About the Author
Eric Watkins is our Senior Malicious Detection Researcher and he brings 20+ years of combined information security and IT experience to zvelo. When not haunting DEF CON, Eric leverages his deep knowledge in Information Security by utilizing an extensive background in research, engineering and IT security architecture. Additionally, his unique perspective in penetration testing and IT security audit experience to validate website threat vectors will further enhance zvelo’s malicious detection services.





