By Eric Watkins, Senior Malicious Detection Researcher at zvelo
Two large annual security conferences are taking place in Las Vegas this week and I will be attending the second one. The first one, Black Hat, is primarily targeted at corporate audiences and sponsorships with well-known industry leaders and vendors supporting and attending the conference year after year. Traditionally, training sessions about computer security are also offered at Black Hat. The second security conference, DEF CON, is really quite different from the first one. At DEF CON, there are far fewer corporate sponsorships than at Black Hat. DEF CON vendors actually sell products associated with hacking. While both conferences focus on computer security, Black Hat is for the “defenders” while DEFCON is geared towards the hackers who refer to themselves as “white hat” (non-malicious hackers). Having attended DEF CON through the years, each year I look forward to learning about current and upcoming security activities and trends. I am thrilled to be going to DEF CON 25 – the twenty-fifth anniversary of DEF CON.
One of the most intriguing items associated with the DEF CON culture is their event badge. While on occasion, these badges are just a badge, sometimes computers are embedded in the badge or some sort of puzzle is involved. In fact, there is usually a contest around the badge creation, but there was no DEF CON 25 badge contest.
Here’s my DEF CON badge from 2016 (on the right). 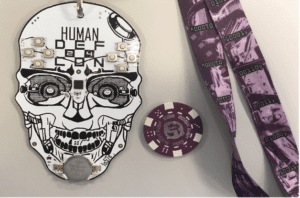
Each lanyard contains pieces of the puzzle for the crypto challenge. Because not every lanyard contained same images, DEF CON 24 attendees needed to hunt and collect images and data from of all of the different lanyards in order to piece together the puzzle and win the badge challenge. As you might imagine, the speculation and anticipation has been mounting around the unveiling of the DEF CON 25 badge.
IoT (Internet of Things) is a major theme of this year’s conference and I’m looking forward to attending several IoT sessions, such as “All your Things Belong to Us” and “Controlling IoT devices with Crafted Radio Signals.” With all of the IoT Denial of Service (DDos attacks) activity in 2016/2017, I will head towards IoT Village to check out content and current events discussions about the Internet of Things.
I’m also very excited about participating in this year’s DEF CON 25 Hack Fortress competition with the DC719 (The Colorado Springs DEF CON group). If you’re interested, read my blog about DC719’s 2016 competition in Hack Fortress.
In Hack Fortress, teams of 10 people (4 Hackers + 6 TF2 players) compete to score more points than their opponents during a 30-minute match. Last year DC719 made it to the semi-finals and this year, we’ve been practicing hard all year to compete again. Although DC719 always fields a great gamer team, this year we’re on upping our game from the CTF/Hacker side.
While we’re keeping our finger on the pulse of what’s going on in computer security at DEF CON 25, as you might imagine, many Las Vegas businesses share a very different perspective on the event. Several industries in Las Vegas have taken additional precautions to guard against DEF CON attendees hacking their infrastructure. Signs, such as the one on the right, have been spotted around Las Vegas area and also posted on Twitter.

Because email is more secure?
Stay tuned, we’ll provide additional tweets (@zvelo) and blogs on what’s happening at DEF CON 25.
In the meantime, here’s my four part series from DEF CON 24, zvelo Spent the Week with over 20,000 Hackers at DEF CON 24:
Part 1 – DEF CON 24
Part 2 – DEF CON 24
Part 3 – DEF CON 24
Part 4 – DEF CON 24






