Threat Alert: Very Active US Postal Service Phishing Attack
Threat: USPS Shipment on Hold Phishing Attack
Threat Type: Personalized URL phishing attack, automated bot phishing
Threat Overview and Attack Characteristics
Beginning in the last 72 hours, zvelo continues to detect a very active US Postal Service (USPS) phishing attack. zvelo’s automated phishing detection systems have detected more than 3,000 unique phishing URLs targeting USPS customers. These attacks have been concentrated on two domains: 1qw2es2z.xyz and 53244ds.xyz. The URLs will have a randomly generated subdomain. Examples of the structure of the hosts for these attacks are shown here:
- oh46xq5pc8u7h7g59hlu5.1qw2es2z.xyz
- aqvdtf.1qw2es2z.xyz
Note that the length of the randomly generated subdomain will vary across the attack
This attack features USPS phishing pages that look similar to the following screenshot. The content of the page appears to be the same across all the different attacks, except that the delivery date shown tends to vary:
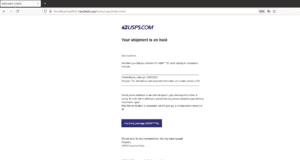
Navigating through the screens for this attack requests the victim’s mailing address information, and eventually will request payment information to “reschedule” the missed delivery.
zvelo’s Detection and Coverage:
zvelo’s PhishBlocklist provides protection against this USPS phishing attack, and others similar in nature. The recent predictive phishing enhancements made to PhishBlocklist are targeted specifically to identify this type of personalized URL attack. zvelo’s Predictive Phishing Detection has been curated through proprietary algorithms to identify phishing campaigns and create the proper intelligence records, allowing customers to efficiently and effectively block personalized URL phishing attacks.
Follow Up Recommendations to Protect Against Phishing Attacks
As with all phishing attacks, users and organizations can protect themselves through a comprehensive security risk mitigation strategy that includes:
- User education to train users to avoid suspicious email or instant messaging links
- Use of a password manager that will alert the user if they are attempting to login into an incorrect or unknown web address
- World class cybersecurity web filtering or DNS filtering solutions powered by accurate threat intel that specialize in phishing attack intelligence
In addition, to limit the damage that may arise from falling for a phishing attack, unique passwords should be used on every service so that a loss of one credential doesn’t compromise other services. Using multi-factor authentication (MFA) solutions will also make it harder for attackers to use stolen credentials. However, MFA isn’t a bulletproof solution to all potential attacks.
If you have been affected by the USPS phishing attack, or any other potential attack, immediately change your account credentials and verify any account information to ensure that the attacker hasn’t changed account details such as addresses, phone numbers, passwords, etc.





