Anatomy of a Modern Compromised Website
When a hacker gains control of a site, they generally do one of several things:
- Nothing — they sit on it waiting for a later date,
- Malware — they load exploits and malware or links to sites that host these in an attempt to infect visitors to the site,
- Defacement — they put up a big notice saying they hacked the site,
- Attack relay — they use the site as part of a chain of sites that lead to malware, or
- Hijacked advertising — they put ads on the site or change ads on the site to make themselves the beneficiaries
- Blackhat SEO — they use the site to trick search engines into thinking that some other site or sites are very popular and should be elevated in search page results
It is the last one, Blackhat Search Engine Optimization (SEO), where hackers are seeing so much success (see our previous blogs on this topic). SEO is the pseudo science of increasing a website’s ranking in a set of search results. Landing at or near the top means more traffic to a website, which can mean advertising revenue or, if the site is malicious, a larger number of infected computers. In either case, the motive is money. And in some cases, hackers sell their SEO services and make money by increasing that search engine ranking.
In any case, search engine rankings are largely driven by popularity. The top results have links coming from many other sites where the more popular the sites that link, the higher the popularity of the site being linked. We call it Blackhat SEO because hackers use the websites they’ve compromised to host links to a website that they want to appear high up in search results.
These links are usually hidden so that casually visitors to the site and the site’s maintainers don’t see them. The links are disguised by putting them off screen or using other techniques to make them invisible to a human visitor, while they remain perfectly visible to computers like Google’s crawlers.
Take, for example, the case of Nauman Sod Farms, a small business in Iowa with a simple website that zvelo first flagged as compromised on February 4th, 2009. It was continuously rechecked and found by zvelo to be infected from then up through this posting.

It is easy to see why someone would think this site is innocent. To a normal user, it appears perfectly fine, but this small business is being exploited by hackers. If you view their home page without security precautions, everything looks normal. If you then disable javascript (using the NoScript plugin or your browser preferences) and reload the home page, you’ll see a long stream of cell phone related links show up at the bottom of the page including:
- cf card gsm review siemens
- unlocking nokia 5210e
- tocatta and fugue in d minor ringtone verizon
- motorola e1 secret codes
- samsung le32r41bd
- free download polyphonic ringtones through sms
- motorola java games
- law and order ringtone
In this case, javascript was used to hide the links, but that is not necessarily the case. And in this case, the links are search engine bait for various mobile phone searches, but we more often see links to pornography sites and malicious sites inside these PageRank Bombs.
Two pieces of obfuscated javascript (meaning it is loosely encrypted to evade anti-virus signatures) add some code to the page that hides the links for those who have javascript enabled. This obfuscated javascript looks like this:
document.write(unescape('%3C%73%63%72%69%70%74...
dF(‘*8HXHWNUY*8J*5Fi…
This evaluates to this:
document.write('
Here, that height of 1 pixel is what instructs the browser to hide the links from a visiting user.
Scanning this compromised page with novirusthanks.org shows that of their 20 AV scanners, none detect a problem. Similarly, not one other URL checker shows any problem with this site including Google’s Safe Search and SiteAdvisor.
Unfortunately, in the case of this particular site, the infection runs deeper. Clicking through into the site offers up a new threat. At the bottom of the page, a hidden iframe has been injected. Essentially this means that the attackers have chosen to have the browser fetch content from another site but not for the purpose of displaying anything to the user. These are typically used to embed exploits hosted on another site onto the compromised site while reducing the maintenance effort. In this particular case, the iframe links to a page that is now missing, so for the moment, visitors are not being infected with malware. Based on our records though, the embedded iframe used to lead to malware, meaning that visitors to this site were targeted with viruses.
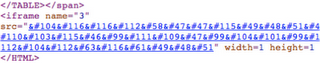
This site has been compromised like this for over a year without the owner of the web site knowing — and this is quite common. It is difficult for security companies like eSoft to automatically notify website owners when their websites are compromised since public information about sites is frequently hidden through privacy screens or else leads to spam traps. zveloLABS™ reached out to Nauman Sod Farms four days ago using the email address on their site to alert them to the problem, but so far there has been no response and the website remains under the control of hackers. Until this is fixed and because of the likelihood of that the hackers may again start infecting visitors with malware, we recommend that folks avoid this site for now. Users of eSoft’s secure web filtering will see this site marked as “Compromised.”
In general, we believe it is important to identify sites that are under the control of hackers even when those sites aren’t being used to propagate computer viruses. These sites may at any time become threatening in that way and are frequently used as part of the machine that drives other sites where the actual malware is stored. The industry as a whole needs to pay more attention to these sites. In the meantime, zvelo does provide protection from these sites and identifies thousands like this one every day.





