Connected Consumer-Grade Equipment is Poised to Be the Next Attack Surface
From smart-phones, to gaming consoles, to laptops, to smart speakers, and so much more, the moment consumer devices make it home, they are almost immediately connected to home networks. While most devices connect without issues, in some cases, users may encounter trouble establishing a connection or completing the set up. Unfortunately, when things do not go smoothly, users often take short cuts which undermine the security of the device, the network, or both. Worse than potentially placing an individual’s personal data at risk, the sudden shift in the last year to a widespread, global work from home culture has connected consumer-grade equipment poised to be the next attack surface.
What Are Consumer-Grade Modems/Routers?
Consumer-grade modems/routers are those devices that provide home connectivity to the internet enabling you to surf the web, send/receive emails, engage with social media, etc. Consumer-grade modems/routers are either rented or purchased from the Internet Service Provider (ISP) in the form of Digital Subscriber Line (DSL), cable, fiber optic modems, or satellite terminals if located in a rural area. Regardless of type, they each provide some modicum of functionality including routing for the home network, Wireless Fidelity (WIFI) Access Points (WAP) to connect the gamut of devices, and usually a basic firewall for security. ISP consumer-grade routers are considered centrally managed devices – meaning the ISP manages the device.
Consumer-grade modems/routers (DSL, cable, fiber, or satellite) can also be purchased separately from the ISP. The obvious implication here is that the consumer has some degree of knowledge to install, operate, and maintain their own equipment. Consumers who purchase their equipment outside of ISP channels tend to be those who are more security and privacy conscious. While there are advantages and disadvantages to owning the equipment by which you connect to the internet, the devices themselves come with the same basic flaws as those obtained from the ISPs. Let’s explore what may be exposed on the consumer-grade router in your home.
What is Exposed on Consumer-Grade Routers?
This next section looks at what gets exposed via consumer-grade equipment that makes it vulnerable to becoming the next attack surface. Consumer-grade routers are designed in a way that meets a couple of primary end-user needs. First, consumer-grade routers need to be easy enough to configure by the average unskilled user. Thus, asking someone to jump into a command line interface to perform more detailed tasks during set up, is out of the question – although, more advanced consumer-grade routers do have this option. Second, consumer routers also need to be affordable, which is also why most lack a slick, out-the-box setup interface. To meet these requirements, manufacturers of consumer-grade equipment standardized on two things:
- A reduced version of Linux Operating System (OS) to run the equipment
- A web-based interface for the Graphical User Interface (because everyone knows how to generally use a web-browser).
With the previous statements in mind, let’s take a look at exposures on a typical ISP provided modem/router. The following shows a basic nmap scan of said equipment:
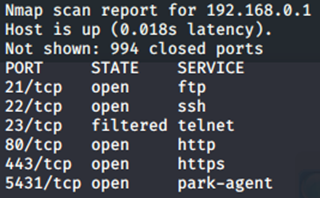
Hold the phone! FTP? Telnet? What is going on here? Remember, ISP consumer-grade routers are centrally managed as part of the service agreement made when a consumer rents the equipment. While there is something to be said for centralized management to keep equipment up to date, doing this via unsecure protocols is a definite risk – especially for organizations using consumer-grade equipment or those with remote employees who work from home. Worse, depending on the ISP, these vulnerable ports cannot be shut down by the individual user which exacerbates potential exposures.
Whether a router is rented or purchased separate from the ISP, it’s common to see port 80 (HTTP) and port 443 (HTTPS) open on consumer-grade equipment as this enables access to the GUI so users may configure and maintain their equipment. For purchased modems/routers, the consumer may be able to shutdown exposed ports and even enable command line SSH interactions for increased security, but that type of setup is inconvenient and thus, less common.
This next image shows an example of an easily discoverable login GUI exposed to the internet:
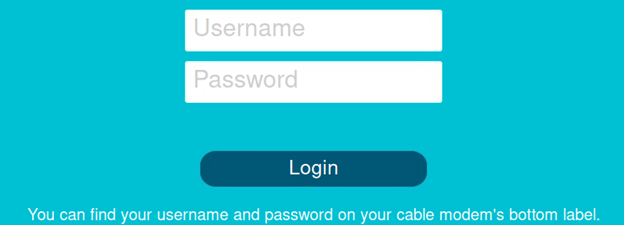
Let’s say your consumer-grade router login is exposed to the internet. Is that a problem? Absolutely! Another question, what is the brand of your consumer-grade router? That’s not hard to find as branding is usually prominently displayed in the web-based GUI. Most consumer-grade modems, especially those purchased directly by consumers, have default credentials at first start up. To make things easy, manufacturers insert these credentials into their equipment user manuals which are posted on the internet. As such, attackers download these manuals and maintain lists of default credentials to try when they encounter an exposed modem/router on the internet. The cybersecurity best practice here is to always change the manufacturer’s default settings.
Even if a user completely secures everything they can in terms of the equipment, their public facing IPv4 address is still exposed on the internet. When it became clear that 4.3 billion IPv4 addresses were not enough, the Network Address Translation (NAT) concept was developed to allow for private IPv4 (space) traffic to be routed onto the internet. Effectively, every consumer has an internal (private) network which is viewed on the internet as a single, public-facing IPv4 address. Consumers receive their public-facing IPv4 address from their ISP. In fact, ISPs own blocks of IPv4 networks to serve the customers. Because these netblocks are publicly available via multiple sources, consumers can identify their IPv4 address, along with their ISPs and, unfortunately, MCAs! To manage their customer networks, ISPs assign DNS (A Record) accessible hostnames to consumer-grade routers, usually based on the public facing IPv4 address as shown next (obfuscated to ensure anonymity, obtained from a publicly available sources):
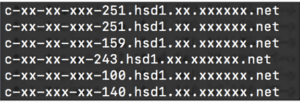
In short, your home modem/router has a routable internet name. If you have exposed ports as described previously this makes you a potential MCA target.
Why Are Consumer-Grade Routers an Easy Target?
There are three things that make consumer-grade modems/routers an easy target for an attack surface. First, many consumers set up their router and forget it. If your internet connectivity is functioning and you can surf the web, why mess with a good thing? The second reason consumer-grade routers are of concern is default credential usage. If your connection point to the internet credentials still has a username/password of “admin/admin” as the default, out of the box setting, MCAs already know it. Finally, ISPs create DNS A records associated with your modem/router as presented previously. This means the entry point to your network is visible on the internet right now.
You might say that your public exposure is just the cost of doing business when you are connected to the internet via any ISP. And you would be correct. However, the point here is that understanding the exposure and working to minimize it is key to protecting your home and business networks. Any IPv4 address on the internet is susceptible to probing by MCAs of any ilk (script kiddies, cyber criminals, Advanced Persistent Threats (APT), etc.). The bad news is the majority of these scans are completely automated bots. The worse news is that if an MCA discovers a useful exposed port (e.g., 3389/Remote Desktop Protocol), they are going to attempt to breach it and gain access to your home or business network. The following figure shows the connections, or breach attempts, coming from a variety of countries trying to access an example home network monitored using Security Onion:
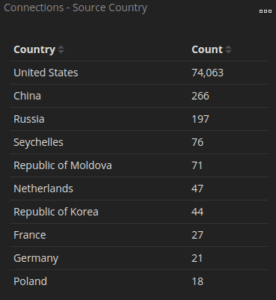
The next figure drills down to show port 3389, Remote Desktop Protocol (RDP) being scanned by a suspected MCA. MCAs are always looking for easy vectors into environments and RDP has proven to be a reliable tactic. It should be noted that RDP is not open in the example home network.
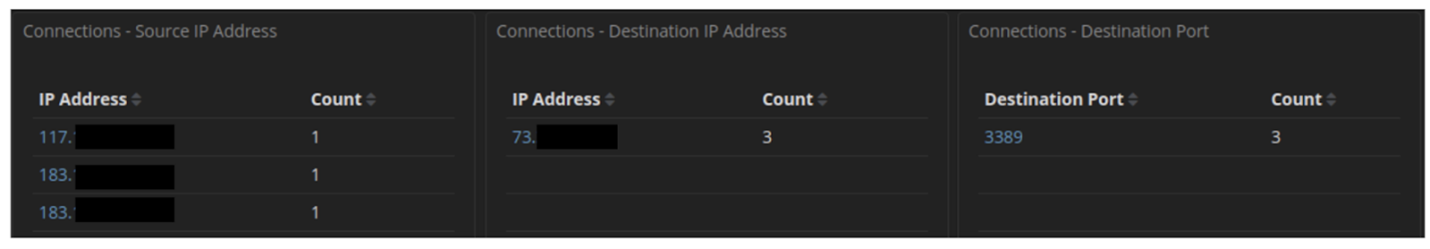
Looking at IPVoid, at least one of the 183 addresses is tracking as malicious, seen here:

In addition to MCAs trying get at what is inside networks via consumer-grade routers, they are also using known vulnerabilities to host malicious content on unbeknownst to the user. This is possible because consumer-grade equipment delivers their GUIs via a “local” webserver on Linux OS. Depending on the webserver version and/or Linux version, either are easily exploitable. Figure X-X shows an (obfuscated) example of such hosting, specifically a fake IRS portal:
![]()
Considering the extensive cyber-attacks seen throughout 2020, we recommend checking your consumer-grade networking equipment and make any or all of the changes mentioned in this post.
Don’t Forget to Secure the WIFI!
Consumer-grade modems/routers tend to be all-in-one type devices which provide network connectivity, wired connections, and WAPs. This is obviously convenient for the average user, especially if they’re not comfortable with setting up their networking equipment. If a user procures their own modem/router, it may or may not have an onboard WAP. If it does not, then the user will likely buy and deploy a WAP. It’s also common for users to install multiple WAPs, or the latest mesh networks to cover larger spaces or multiple floors.
Just like the modems/routers used to connect homes and businesses to the internet, WAPs out of the box have a default set of credentials (check out https://www.softwaretestinghelp.com/default-router-username-and-password-list/ to see if your WAP is on the list). Who cares about your WAP credentials? If you have not heard of the concept of War Driving, you may be surprised. In War Driving, groups and individuals drive around looking for available WAPs and test default credentials. War Drivers then report their discoveries to a community of users, via sites such as Wigle, looking to take advantage of free WIFI. Who does not like free WIFI, right? The results look something like this from Wigle:
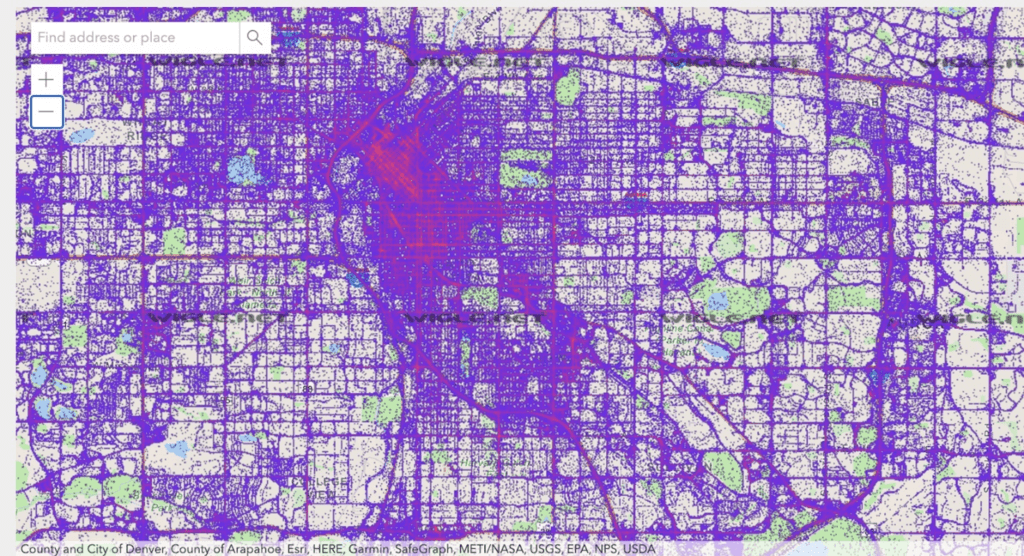
As you zoom in on the map, you discover WAPs that have been reported by multiple observations. Of concern is when you find “brand name” Service Set IDentifiers (SSID) WAPs on the map. It is quite likely these WAPs have default credentials. The real danger here is an outsider may join your WAP and snoop around in your home or business network.
It is not just WAPs that can be found on resources like Wigle. You will also find printers, streaming devices, and many other Internet of Things (IOT) devices which can be exploited remotely to provide low-level cyber criminals easy access to networks, many be even yours. So, please do not forget about the WIFI in your environment.
What Can You Do to Secure Your Connected Consumer-Grade-Equipment?
Whether you’re a consumer tech aficionado with all the latest smart technology, one of millions who are part of the global remote workforce, or even a business which leverages the use of consumer-grade devices, your equipment is likely exposed on the internet with exploitable vulnerabilities that are being actively probed by MCAs. These are a few basic steps you can take to make yourself less of a target and ensure that your connected consumer-grade equipment does become part of the next attack surface.
- First, realize you are a target! Your home or business network, no matter how big or small contains data of value to a variety of MCAs.
- Second, change your default credentials on all modem/routers and WAPs in your environments! Do not make it easy for an attacker to get in.
- Third, close any unneeded ports on your modem/routers and WAPs. Remember, if any of these are exposed to the internet, they will be probed by MCAs looking for a target of opportunity.
- Fourth, patch your systems, even if it is upgrading the firmware on your equipment.
- Finally, do not broadcast your SSID. Can an experienced attacker still sniff out a WIFI network that is not broadcasting? Absolutely, but why make it easy?
When it comes to securing your home or business environments, doing the basics goes a long way. Be a hard target, not a soft one.





