Estimated Reading Time: 7 minutes
Going Old School with Excel 4.0 Macros (XLM)
Malicious Office Documents Series, Part 3 of 3
This is the third article in a three part series designed to show various old school techniques regaining popularity that adversaries can use to subvert Microsoft Office documents for nefarious purposes. In part 1 of the series, we covered injecting macros from a remote Word template. Part 2 covered Symbolic Link (SYLK) files. This article, part 3, discusses how attackers use Excel 4.0 macros (XLM) to gain a foothold into a network and establish persistence.
Originally introduced in 1992, Excel 4.0 macros are the precursor to Visual Basic for Applications (VBA), a legacy feature incorporated in Microsoft Excel for backward compatibility reasons. Excel 4.0 macros use formulas in various cells to execute code, top down, left to right, and most likely located in hidden worksheets. Predating VBA, XLM macros are highly useful in offensive operations as a means of downloading and invoking the next stage of the attack — usually a DLL or executable. XLM can be difficult to analyze, and it appears that most antivirus solutions have trouble detecting XLM laden malicious documents. Furthermore, XLM worksheets (.XLS) files don’t have VBA macro code, therefore, detection under Windows Antimalware Scan Interface (AMSI) will fail.
Weaponizing Excel 4.0 Macros
Weaponizing Excel 4.0 Macros is an effortless and reliable method attackers use to get a foothold into a target network as this technique simply represents an abuse of a legitimate Excel feature, and does not rely on any vulnerability or exploit. XLM macros are very straightforward and easy to create, thus easily modified to bypass signature-based detection. Macros are also robust and provide various functions that can be leveraged to evade analysis, such as obfuscating the final payload, modifying the control flow, or detecting automated sandbox analysis through specific host environmental checks.
This technique will likely remain relevant, and join its successor (VBA macros) as a widely used technique to weaponize document files. Weaponizing Excel 4.0 macros does not rely on a bug, nor is it an exploit — it simply abuses legitimate Excel functionality. Samples can be challenging to assess as they are able to evade automated sandbox analysis. Some recent samples are password protected, code is obfuscated, worksheets are hidden, as well as several anti-sandbox checks — any of which leads to difficulties when assessing. As this is somewhat uncharted territory, malware authors and researchers are still exploring the depths of possibilities and capabilities of weaponizing this attack technique.
How Attackers Leverage Excel 4.0 Macros
Based on what defenders are seeing in the wild, the following steps demonstrate how attackers use Excel 4.0 macros to set up this type of attack. In order to conduct this attack, we first need to create a new Excel workbook. Once the workbook has been created, right click on “Sheet1” and click “Insert”.
Figure 1: The image below shows how a user can insert new objects into Excel spreadsheets.
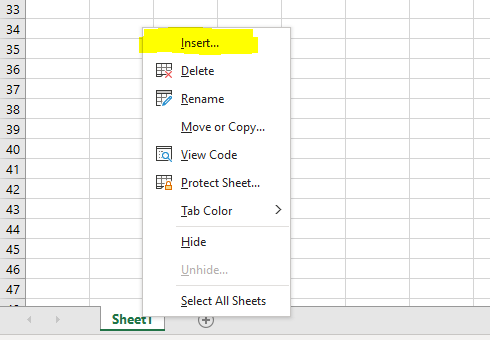
When you insert objects, a window opens allowing you to select from various objects that can be inserted. Here we will select “MS Excel 4.0 Macro” and click “OK”.
Figure 2: The image below shows what types of objects are available to be inserted into a given Excel spreadsheet.
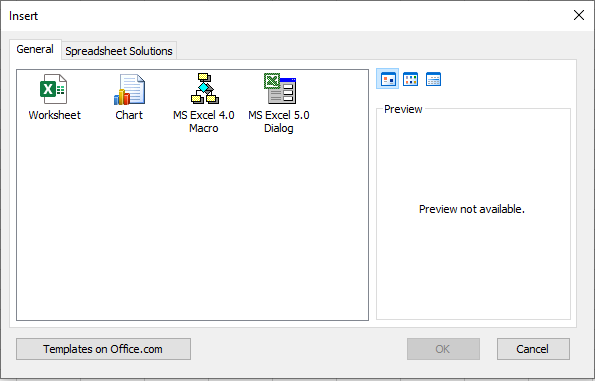
MS Excel 4.0 Macro sheets are special worksheet types in which XLM macros can be entered. By clicking any cell you can enter formulas, such as “=EXEC()” which will execute a given command or “=ALERT()”, which will popup an alert dialog box and so forth. These sheets can be set to execute any number of actions when a condition is met, such as when the document is opened or closed.
Figure 3: The image below shows the execution of XLM macros to run commands on a system.
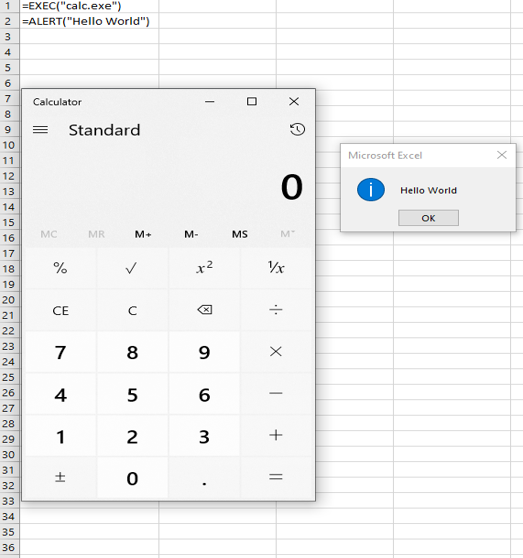
Attackers hide their worksheets by a right mouse click on the sheet name (“Macro1”) and selecting “Hide”. Auto_open XLM macros will still run from hidden worksheets. It is also not uncommon to see obscurity tricks, such as the usage of white font on a white background, formulas existing on columns or rows normally out of sight (e.g. column “AA” or row “240”), or having formulas scattered across the sheet or even multiple sheets in the workbook.
Malicious File Examples
Now that we have discussed at a high level how attackers can leverage Excel 4.0 macros, we can look at some of the malicious files discovered in the wild. These types of attacks are usually initiated through the use of phishing campaigns, where the email attempts to masquerade as a resume or invoice of some sort. Regardless of the gimmick, the actions are the same — get the user to open the document and click enable editing.
Figure 4: The image below shows an example of a phishing email designed to look like a resume / contact information.
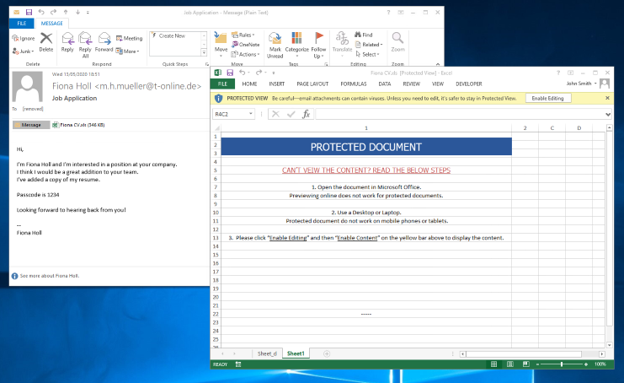
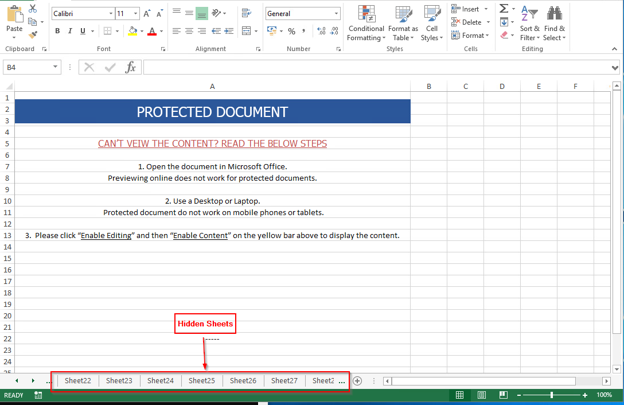
From here, one of the first tasks is to check for any hidden sheets. This can be done by going down to the bottom and right clicking on any visible sheet tab, and then selecting “unhide”. A dialog box will appear and you can select which sheet you want to unhide. This can quickly become tedious if there are multiple sheets present. Another option is to use the ExcelSheetUnhide powershell script to quickly reveal/unhide all hidden sheets within a workbook. Regardless of how you choose to unhide the sheets, you will be presented with the following:
Figure 5: The image below shows the hidden sheets present in the Excel workbook.
With the hidden sheets exposed, we can check for, and remove, some basic obfuscation techniques by selecting all cells in sheets and changing the background color to “No Fill” and the text color to black. We can also toggle formulas on by pressing the Ctrl key, and the backtick key ( ` ) —frequently located above the Tab key on standard US keyboards. By doing so, some indicators of compromise (IOCs) will be visible but may be incomplete. The amount of data revealed will vary. It is the execution flow of the enabled macro that will combine strings, replace variables, etc., to output a more complete result. In order to get such a result, you will most likely need to dynamically analyze the file.
Figure 6: The image below shows the hidden values and formulas once obfuscation methods have been removed.
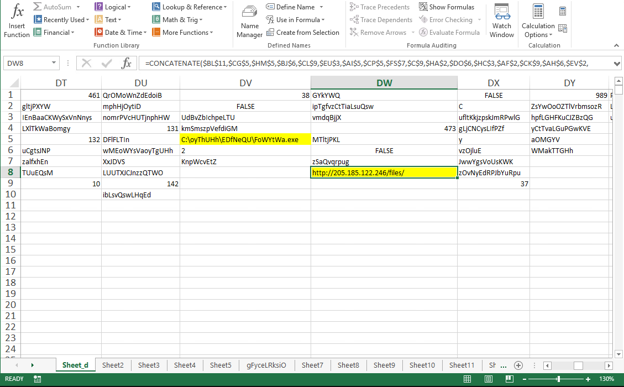
As you can see in the image above, this document will concatenate the content of various cells to get its execution parameters. From there, it will look to reach out to a malicious server located at 205[.]185[.]122[.]246 and download an executable to the system. Recently we have seen prolific malware such as Trickbot and ZLoader use this style of payload delivery to gain access into a network, scrape any data they can find, and establish persistence. What makes this even more deadly is that Trickbot has been observed in the past aiding in the delivery of ransomware.
Recommendations
Remember, social engineering attacks are designed to take advantage of a user’s possible lapse in decision-making. To help prevent attacks that leverage Excel 4.0 macros from occurring, zvelo’s Cybersecurity team offers the following recommendations:
- Additional security measures have been added to Microsoft Office 2019 following its release that will now detect malicious XLM macros and, in most cases, outright prevent a user from even opening the document. Therefore organizations should either update to the latest version of Microsoft Office, or use Office 365 which offers added protection.
- Don’t open attachments or links in unsolicited emails — even if the emails came from a recognized source. Whenever an email is unexpected, always be wary about opening the attachment without first verifying that the sender intended to send the email.
- Organizations should educate and train their employees to be wary of any communication requesting personal or financial information. They should also instruct employees to report any threat or suspected threat, to the organization’s security operations team immediately.
Conclusion
Excel 4.0 macros continue to prove valuable to attackers by providing a reliable method to get their code to run on a target. Excel macros provide a near endless, and continuously evolving list of possibilities for malware authors. Just as an example, we are now seeing malicious documents use XLM macros to access Win32 APIs. Excel worksheets with macros are so widely used for legitimate business purposes, disabling or blacklisting them is not a viable solution in most cases. Instead, network defenders and analysts alike will just have to get used to consistently updating tooling, signatures, and more importantly, their investigative methodologies as attacks continue to evolve.





