How Ad Networks are Being Used for Scamvertising
The Internet age has shown us a myriad of online scams, from get rich quick schemes to winning the lottery, typically originating via an email hook. This is a blind way of distributing scams, since scammers have no way of knowing if the scam is relevant to the person they are trying to lure. For example, a scammer might send a Lotto scam in a country where there is no Lotto. This has changed; scammers now have access to online advertising networks, which have proven to be very powerful targeting tools because of the vast amount of demographic and web usage behavioral information they possess about real people.
What is an Ad Network?
Ad Networks sell inventory, or advertising space on web pages offered by web publishers like CNN, the Wall Street Journal and even blogs. They package inventory based on consumers’ demographic information, then sell it on behalf of publishers to advertisers, commonly at a CPM (Cost-per-thousand impressions) model. This allows Advertisers to gain access to a diverse set of publisher sites on which they can then push highly targeted and relevant ads to consumers.
As such, this makes Ad Networks perfect distribution points for scamvertising and other potentially fraudulent activities. Ad Networks provide the reach and the targeting capabilities to easily and more efficiently target victims. In this article, we provide evidence of this trend.
The Investigation
Our investigation began as a result of an unrelated project. As part of zveloLABS’ ongoing focus on ad fraud and non-human traffic research and detection, we were analyzing malware behavior. The actual malware was called Poweliks. What piqued our interest is what we found during our analysis of the traffic.
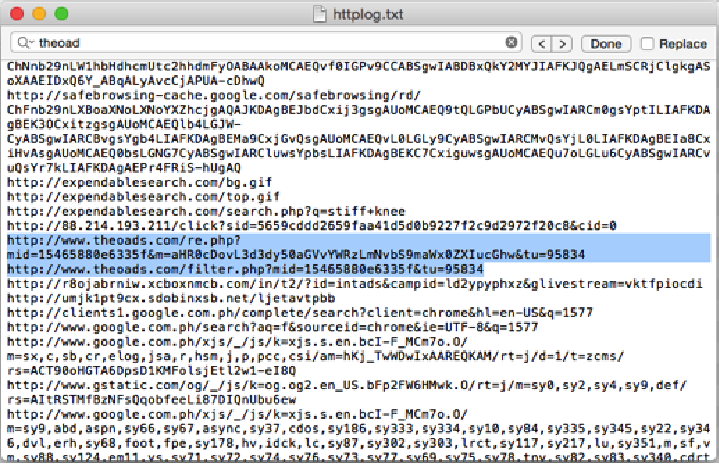
Image 1: Example of click fraud behavior
Based on the traffic, Poweliks was definitely exhibiting click fraud type of behavior. Noticeable in the screenshot (image 1) is the typical recipe for several of the most recent click fraud types of malware: use of low quality search sites to launder traffic and then the use of intermediaries to redirect to an advertiser’s landing pages. These intermediaries are Ad Networks.
Laundry Websites
The search websites detected are created in bulk for laundering non-human or fraudulent traffic. In this scenario, an Advertiser’s web referrers would be the search sites instead of the infected machines, meaning that the true traffic source would remain unknown.
For example, we found many of these sites with the exact same web templates, IPs and registration information (see image 2).
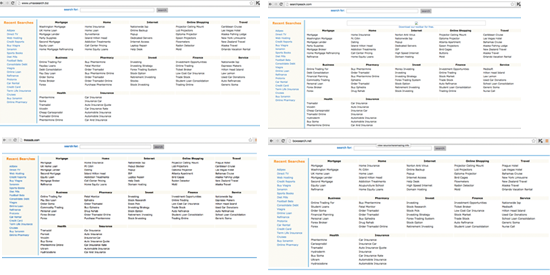
Image 2: Examples of search sites used to launder non-human, fraudulent click traffic
The malware typically sends a search query to one of the search sites. The search site then provides a result (an Ad), which then points to an advertiser’s landing page. In click fraud, malware generates a “click.” Clicks are then charged to advertisers commonly at a cost-per-click (CPC) model. CPCs range between a few cents to a few dollars, and can blow up Advertiser budgets real quick.
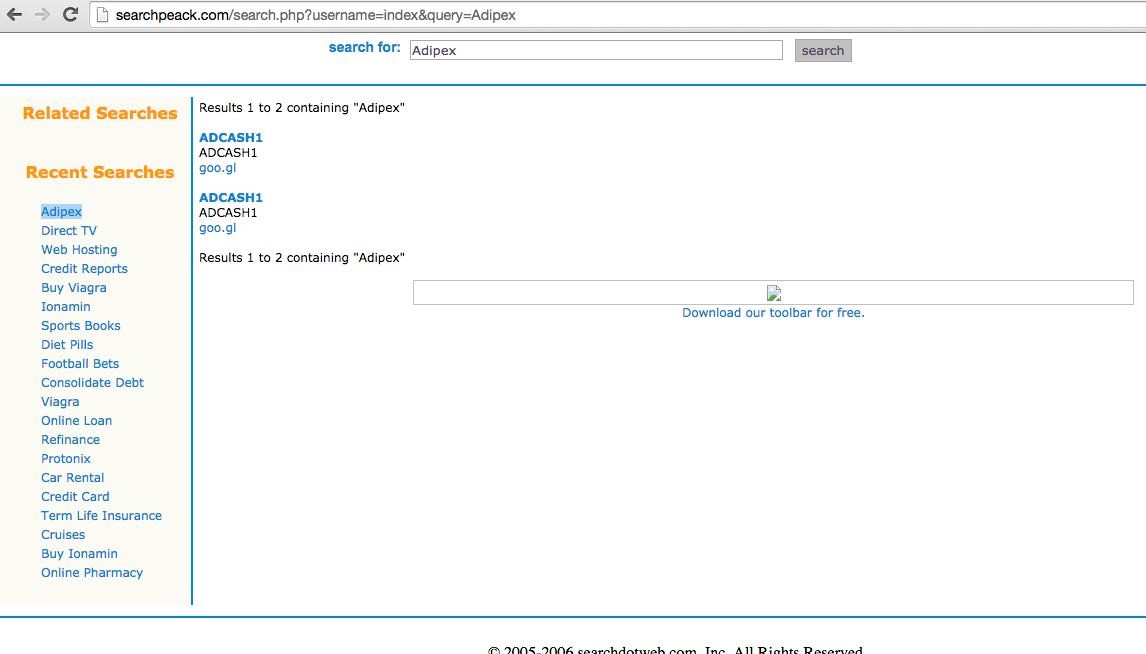
Image 3: Another example of a search site used to launder click fraud
The Ad Network and Scams
This is where it gets interesting. As stated, once the ad is clicked, it redirects to the advertiser’s landing page through a series of intermediaries, one of which is an Ad Network. In one of the examples we saw, the laundry search site provided this link:
http://www.theoads.com/re.php?mid=15465880e6335f&m=aHR0cDovL3d3dy50aGVvYWRzLmNvbS9maWx0ZXIucGhw&tu=95834
The link rotates and points to various sites seemingly through the AdCash Ad Network (image 4).
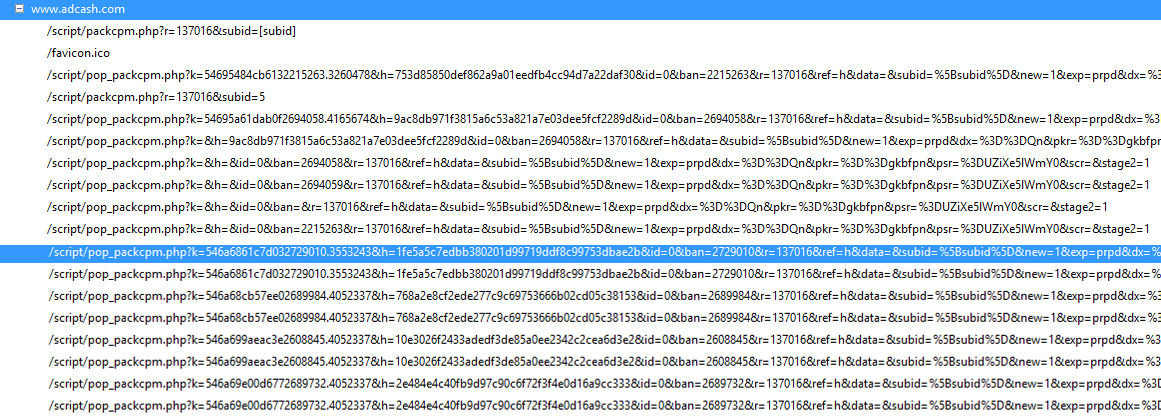
Image 4: Links in rotation seemingly from the AdCash Ad Network
When we followed the ads served by the AdCash, we were quite surprised that the network appeared to be serving potentially fraudulent scam websites.
Targeted Campaigns
Since we utilized a Philippine IP address to crawl through the Ad Network’s links, we got scams targeted to Philippine residents. Scammers surprisingly took the time and effort to tailor campaigns to this demographic.
The capability of Ad Networks to target the right audiences combined with the local theme, presentation and even vernacular found on the websites, this whole setup makes for very convincing scam campaigns. Following are a few examples of scam websites identified.
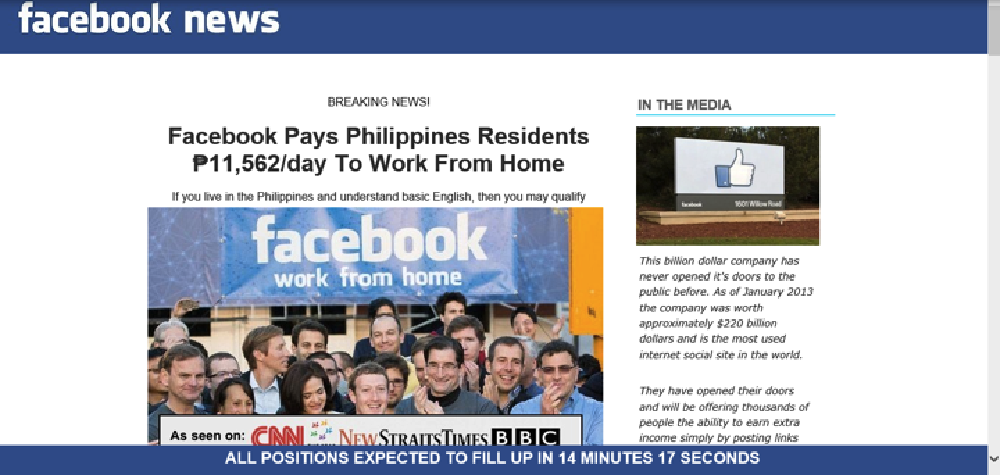
Image 5: Example of a work from home scam website tied to Facebook
Work From Home Scams – this appears to be an Internet scam to lead people to buy a work from home kit (image 5). Note how the article has a very specific locale and target (Philippines).
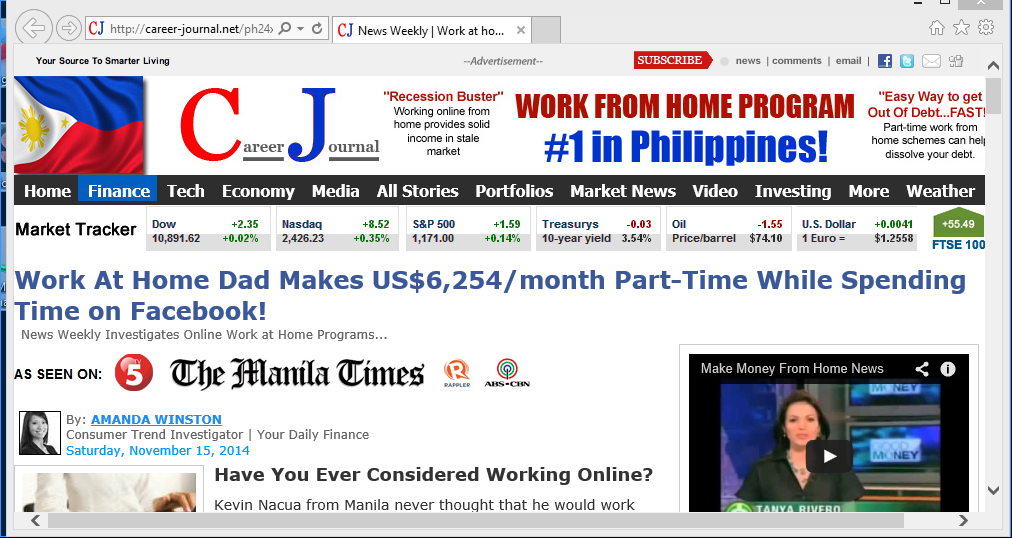
Image 6: Example of a scam website leveraging local media
Different Version – here’s the same scam but presented differently. Scammers leverage local media outlets (image 6).

Image 7: Example of a scam website tied to Facebook Fortunes
Facebook Fortunes – the scam begins with articles focusing on Philippine residents and even includes pictures of checks from local Philippine banks. Scammers are asking people to pay around $160-180 USD for a work from home kit that will allow them to make just as much, or more, money. Obviously, no kit is ever delivered. In some cases, it has been reported that they charge credit cards without consent. $257 USD per day may not be much, but considering that the minimum daily wage in the Philippines is only about $10 USD/day, it can be eye candy for many.
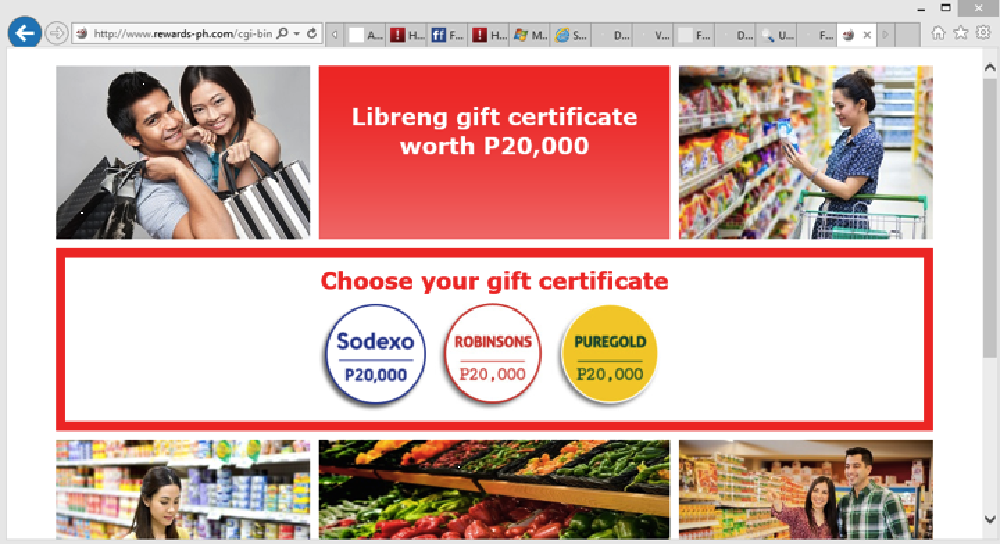
Image 8: Example of a scam website tied to gift certificates
Gift Certificate Scams – some of the retail outlets mentioned (image 8) have already warned their customers about these fraudulent sites. Again, this scam web page is very locale specific and therefore must require the demographic targeting information provided by the Ad Network in order to be effective.
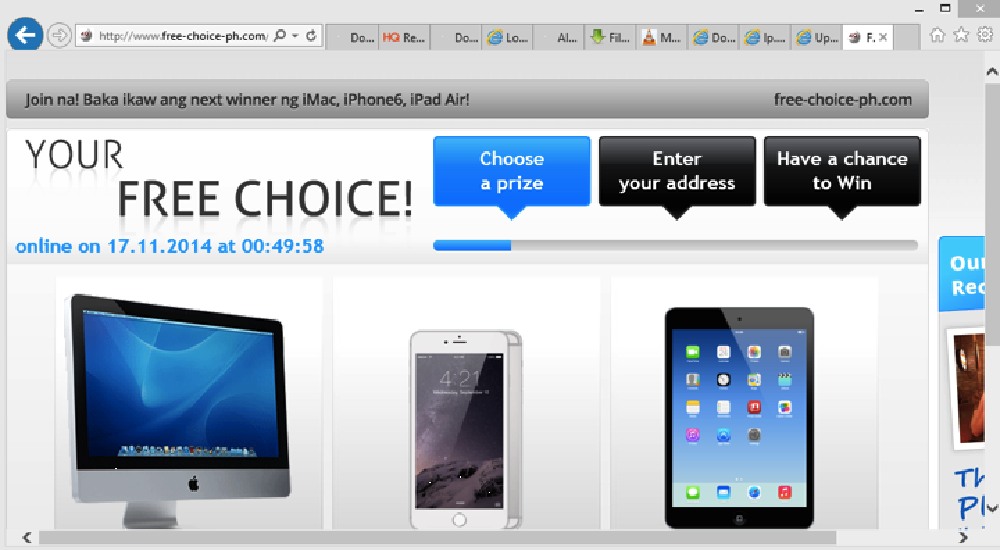
Image 9: Example of a scam website served tied to a rewards campaign
Rewards Scam – this site (image 9) is actually hosted in the same IP as the rewards-ph.com so it’s probably the same scammers. Additional research shows that this is related to “Planet 49,” which is under investigation in some countries. This web page uses local vernacular at the top, in addition to specific local Philippine retailers. Had we used a US-based IP address we would have likely seen US retailers.
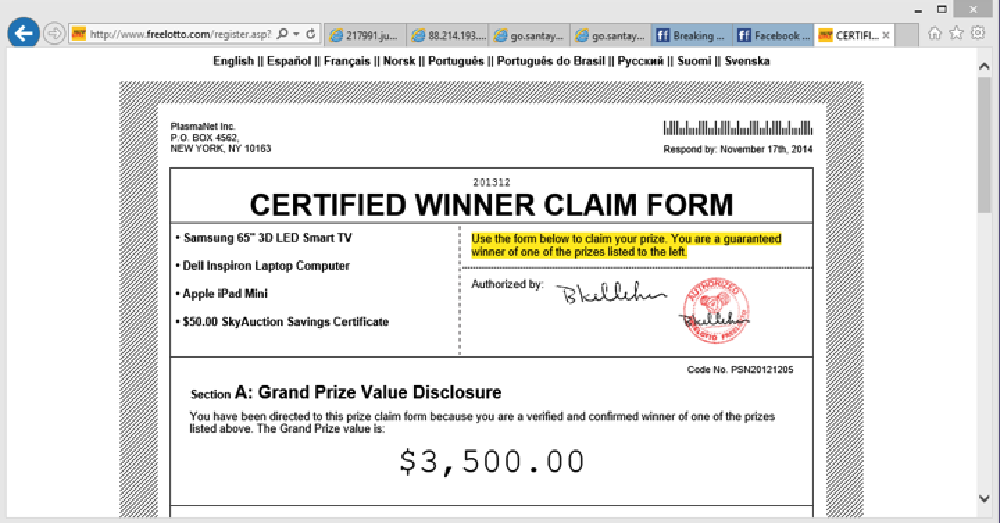
Image 10: Example of a Lotto scamvertising website
Lotto Scam – it appears that this particular claim form (image 10) has been reported as fraudulent. Scammers promise “winnings” but victims need to pay fees for delivery, insurance, and taxes first. How convenient.
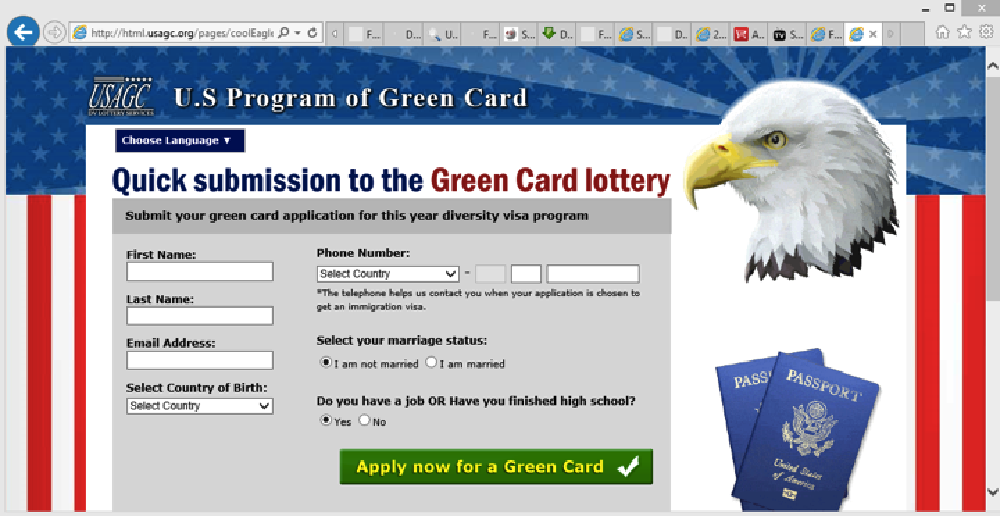
Image 11: Example of a Green Card Lottery scamvertising website
Green Card Lottery Scam – multiple fraud reports have already been documented for this green card lottery scam (image 11) and in some cases people have reported losing in excess of $1,000 USD.
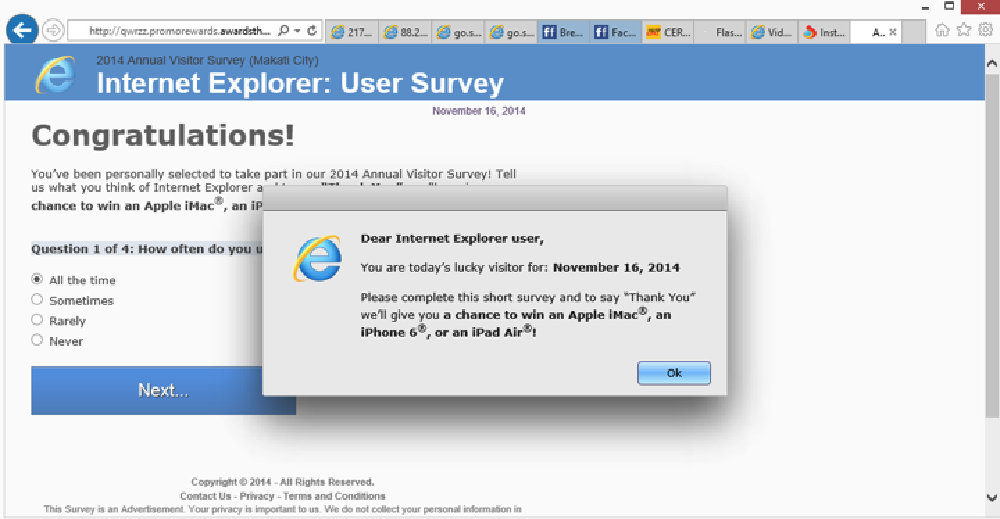
Image 12: Example of an IE survey scamvertising website
IE Survey Scam – an IE survey to win a Mac (image 12)? Very little information was available but it is obviously not a Microsoft IE survey.
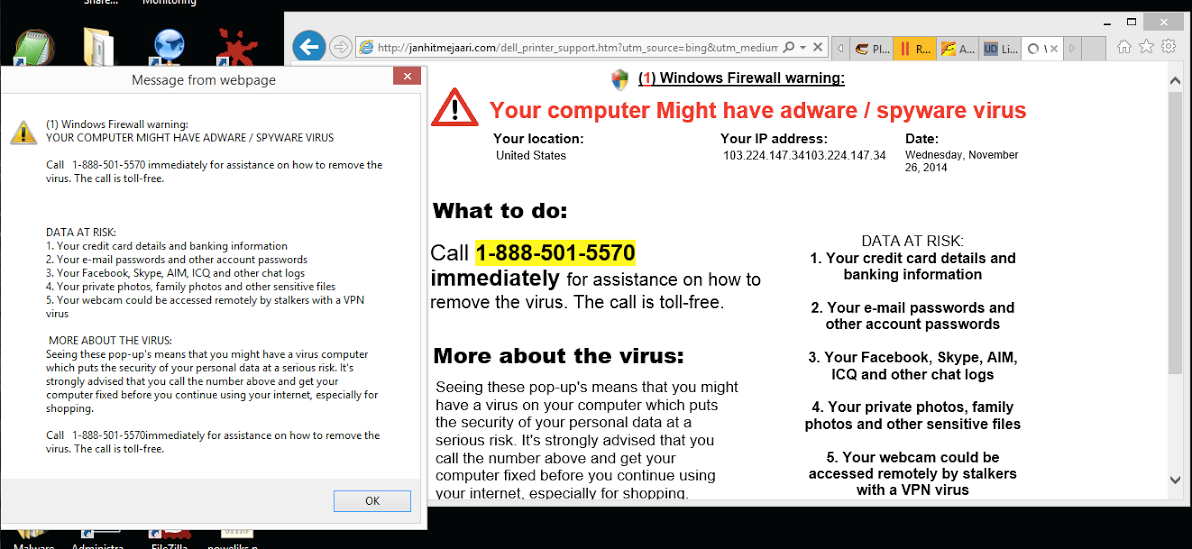
Image 13: Example of a computer repair scam website
Computer Repair Scam – freezes your browser due to the continuous pop-ups (image 13). According to multiple reports, the number connects you to a sales person who will attempt to get you to install a rogue AV and a browser adware extension.
Spam, Adware and Malware
We decided to run the various Ad Network links through our malicious detection engine to identify other potentially suspicious websites. Our results identified multiple spam and adware sites being served.
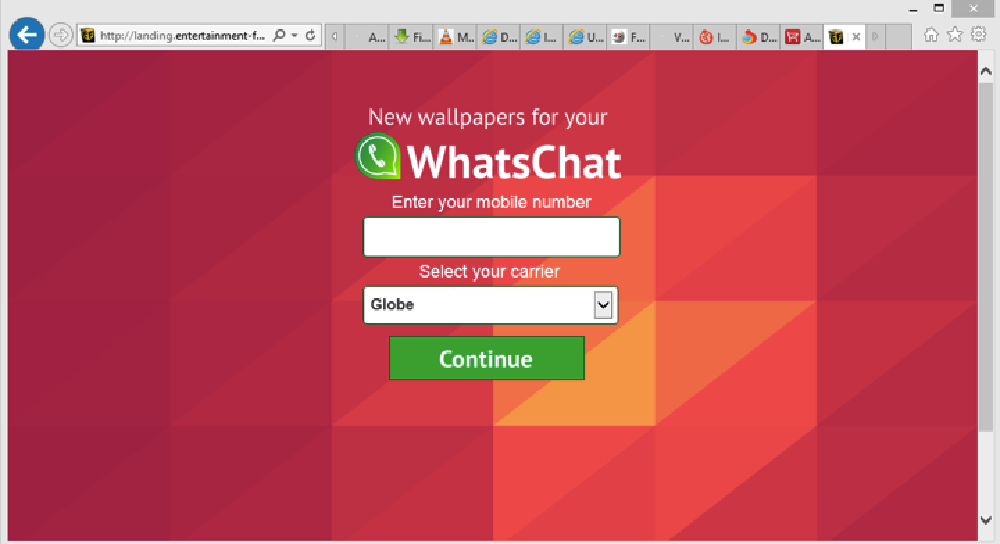
Image 14: Example of a WhatsChat website tied to a SMS spam campaign
SMS Spam – interestingly enough, WhatsChat (image 14) is real but in this case the “entertainment-factory” URL distributes SMS spam, popups and adware. Note that the carrier is also locale specific.
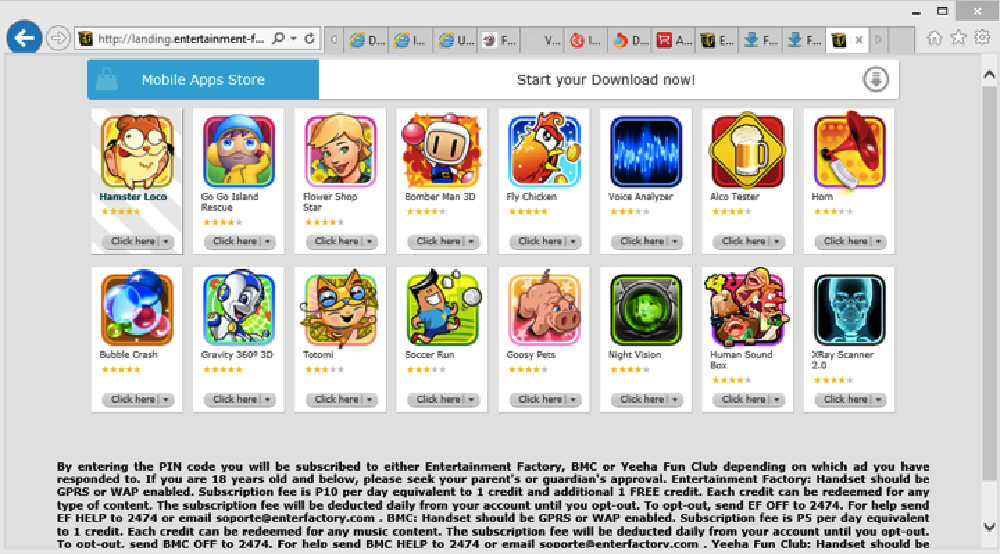
Image 15: Example of a mobile apps website tied to a SMS spam campaign
Mobile Apps – this similarly appears to be a mechanism for SMS spam (image 15). It appears one has to pay a subscription fee. The “landing.entertainment-factory.com” URL in general has a very low reputation and it appears to employ highly invasive spamming techniques.
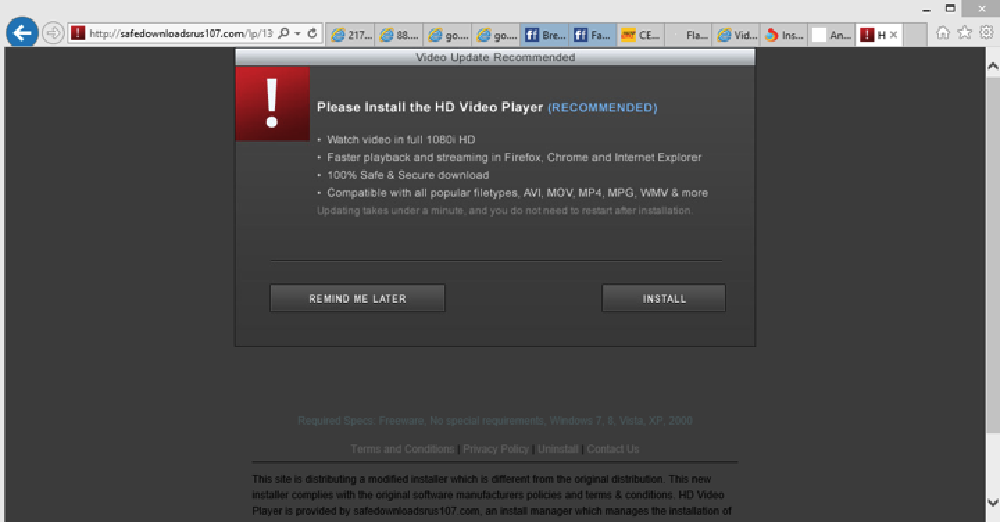
Image 16: Example of a malicious website tied to a web browser hijacker
Browser Hijacker – this infects various Internet browsers. It has been reported as a malicious website (image 16) by multiple anti-virus software solutions. Interestingly, it appears to utilize multiple, incremental domains (e.g. safedownloadsrus104, safedownloadsrus107, safedownloadsrus109 and so on).
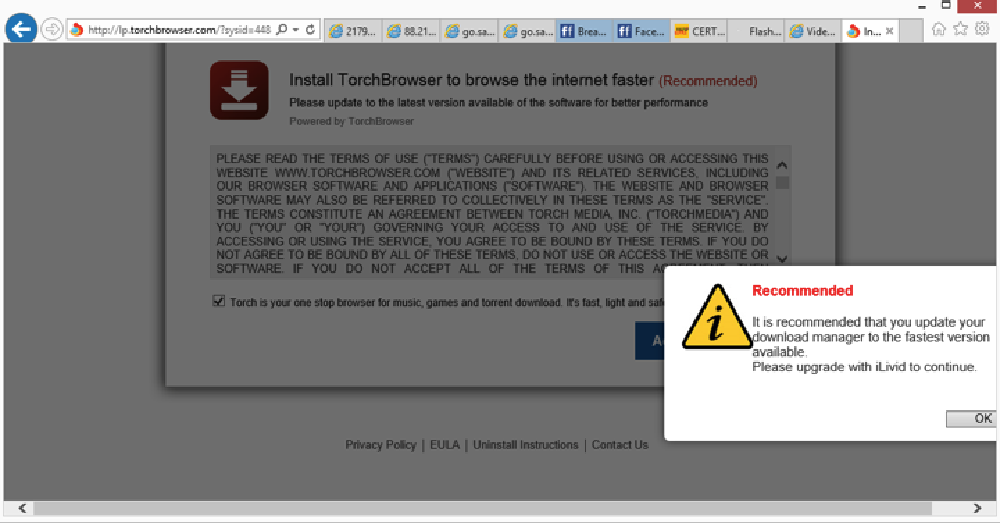
Image 17: Example of a malicious website tied to adware
Adware – launches new browser windows or tabs to show banner ads (image 17).
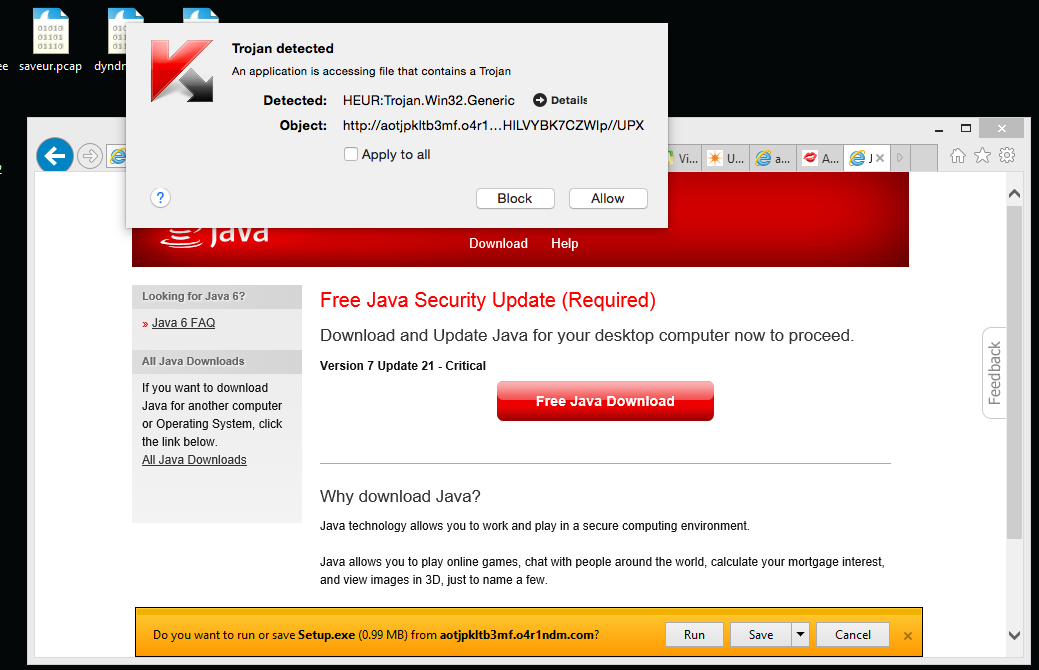
Image 18: Example of a malicious website tied to a Trojan computer virus
Malicious Websites – some of the landing pages detected (image 18) attempt to serve a Trojan to the user.
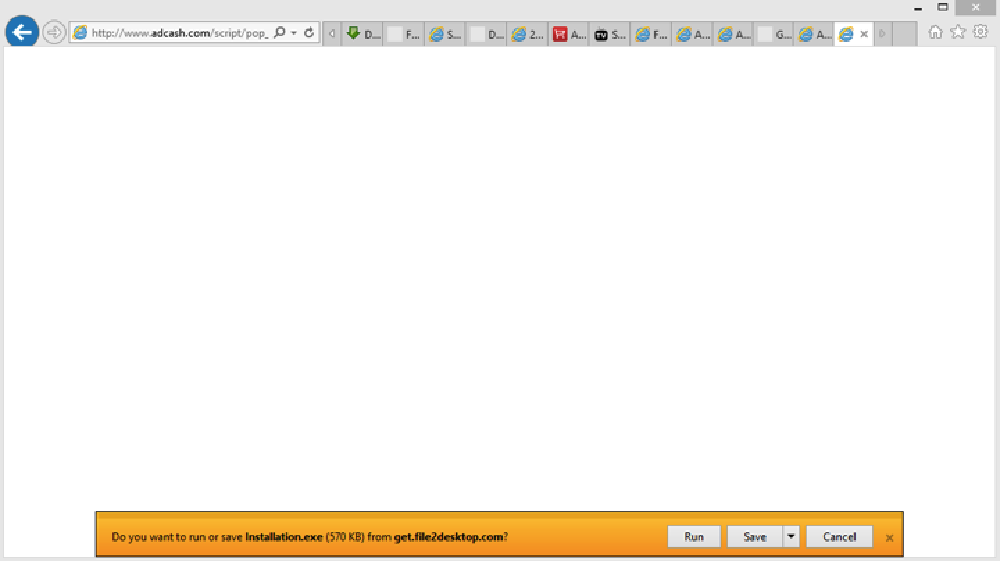
Image 19: Example of a malicious website tied a malicious executable file
Download Attempt – this malicious website (image 19) does not even show any content, but rather attempts to download an executable file right away.
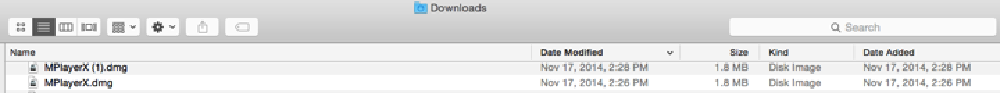
Image 20: Example of a malicious website tied a drive by download threat
Drive by Download – some sites (image 20) download the executables to the user’s machine immediately without their permission. This is known as a drive by download.
And it appears like this is just the tip of the iceberg as we were served with a lot more low quality, malicious websites (image 21).
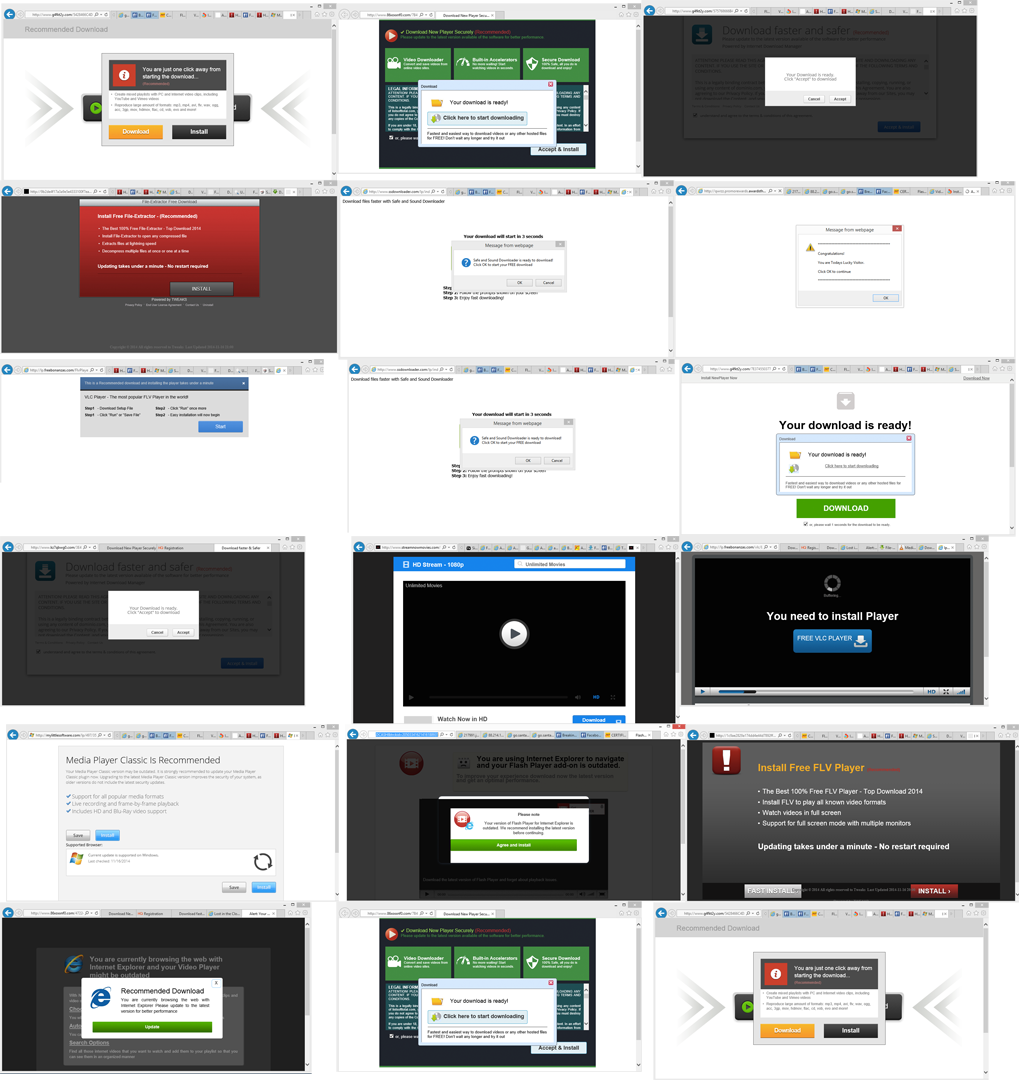
Image 21: Multiple examples of malicious websites tied to spam, adware and malware
It’s a Jungle Out There
During the course of our research, it was interesting to witness a real Ad Network being utilized to deliver scams, spam, adware and other low quality and suspicious sites to a wide and highly targeted audience. More concerning was the realization that fraudulent and scam sites could actually hurt people emotionally and/or financially.
AdCash is a fairly large advertising network. It ranks in the Alexa Top 500 websites, and delivers content to hundreds of millions of unique visitors per day through an estimated 100,000+ websites and mobile applications. With such a vast reach, imagine the number of victims scammers can reach instantaneously.
Our research led us to ask if Ad Networks should be held responsible for policing their advertisers. Some of the Advertisers, in this case after all, are scammers. What about other mediums? If a TV network runs an ad for a pyramid scam, for example, would the TV network be liable for any damages that may ensue? This is a very grey area, but in our opinion, some form of due diligence should be conducted by the Ad Network. We suggest two solutions.
More In-depth Vetting of the Advertisers
How easy is it to advertise via an Ad Network? There are many ways but sometimes it’s as simple as filling out an online form along with a small monetary investment. In most cases, there is little, if any, vetting of Advertisers or their ad campaigns.
Understandably, the core business of Ad Networks is to make money from connecting ad units placed on publisher websites to relevant audiences, so vetting advertisers is probably a low priority. There should at least be some due diligence in the part of Ad Networks to ensure that their Advertisers are not fraudulent, like more in-depth background checks and auditing of ad units and landing pages.
Auditing of Advertiser Landing Pages
In digital advertising, heavy focus is placed on the quality of publisher websites. How much traffic do they get? How visible are the actual ad placements (header, sidebar, in-line with web page text, etc.)? What’s usually overlooked is the quality of the Advertiser. Ad Networks should audit both the ads and the Advertisers’ landing pages to identify scams, adware and malicious sites and objects. In this study, we simply ran the Advertiser landing pages through our malicious detection engine and were able to detect fraudulent, adware and malware sites without much effort (image 22).
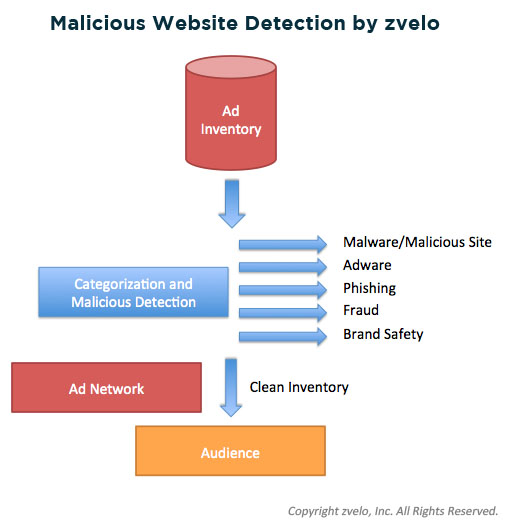
Image 22: zvelo’s malicious detection service in action
Our detection service can “audit” an Ad Network’s inventory (the URLs where the ads point to) to identify malware, adware, phishing and other malicious websites, and can even help with the detection of non-human or bot generated traffic. Also of value would be the ability to detect porn, violence, hate, and other inappropriate content to help package and sell brand safe inventory.
Conclusion
The ad ecosystem is extremely complex. There are many players and transparency is difficult to provide. Increased transparency is in high demand, especially from legitimate Advertisers that continue to lose credibility, customers and billions of dollars in revenue due to scamvertising and the laundering of non-human and bot generated traffic. We reached out to AdCash and notified them of our findings, and would welcome the opportunity to help them, and any ad network for that matter, clean up their ad inventory. To be fair, our research and analysis is not a bash against AdCash, but is intended more to boost awareness about how Ad Networks are being exploited to disseminate spam, scams, malware, viruses and other web threats.
Lastly, the fault does not fall entirely on Ad Networks. End users ultimately bear the final responsibility whether they fall victim to a scam or not. Websites and offers behind an ad campaign are not always trustworthy.





