The explosion in the number of XDR/MDR and Incident Response providers has ushered in a corresponding increase in the number of vendors trying to build their own in-house cyber threat intelligence (CTI) groups. Which begs the question: Will the multi-million dollar investment required to build your own in-house threat intel generate the ROI you need? In most cases, the answer is likely to be no.
These groups have virtually identical characteristics — They ingest commercial and open source phishing, malicious and threat feeds; implement big data systems where the ingested data can be stored and sorted; hire AI and Machine Learning experts to develop models for detecting threats; hire cybersecurity experts to review and analyze threats; hire data analysts to annotate and label the data; and more. And that is all separate from the teams that do the actual customer support and response for cyber threats.
The competition for scarce engineering, AI, cybersecurity, big data, and data annotation skills has left most vendors understaffed, over budget, and unable to fulfill the original vision of the benefits of building in-house cyber threat intel. Very few organizations have the wherewithal to make the necessary investments over several years just to create the initial capabilities, let alone sustain the investment on an ongoing basis. The result is that many of these organizations have had to rethink whether in-house cyber threat intel is a core competency, particularly in light of market pressures from PE’s/VCs and investors who are advocating for channel investments to grow and scale the business.
The High-Level Hard Costs for In-House Cyber Threat Intel
Though it may seem to be an easy problem to solve on the surface, developing a solution to manage the ingestion, aggregation, and curation of threat intelligence data requires significant financial investment that, even on the very conservative end, comes in at $1.2 Million USD annually just to cover the bare minimum hard costs for threat feeds, infrastructure, and staffing. The following table helps to identify the true costs of in-house CTI for those organizations who are evaluating — or re-evaluating — whether or not this might be the right strategy for their business.
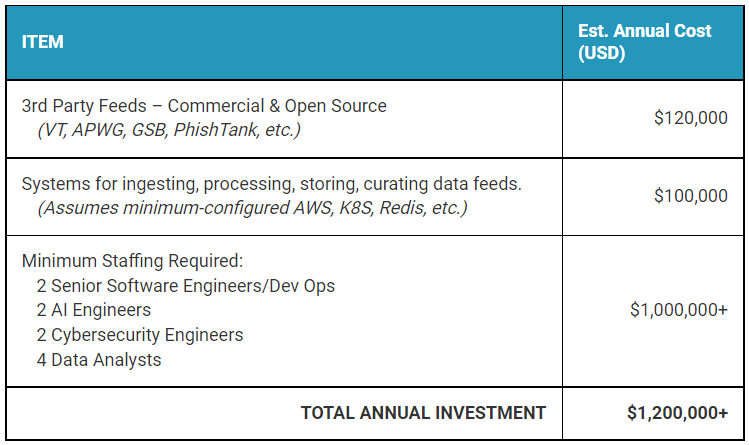
Note that the structure and costs above represent a “bare bones” (i.e., conservative) approach. If your organization isn’t deterred by the above costs, there are other numerous other considerations and hidden costs when it comes to developing, implementing and managing threat intelligence solutions.
In many cases, companies trying to pursue a XDR, MDR, MSSP, or Incident Response business strategy attempt to build an in-house solution, believing they can do it better, do it cheaper, or just have the freedom to customize the threat detection solution in any way they need so that it’s an exact fit for their requirements. In reality, that rarely proves to be the case as building the teams and systems to do threat feed ingestion and curation in-house is very complicated and expensive. If your organization is considering a DIY in-house cyber threat intel approach, you’ll most likely need an multi-million dollar annual budget, a minimum of 2 years to develop it, and even longer to realize an ROI that justifies the initial costs.
Realities of In-House CTI: Ingesting, Aggregating, and Curating Threat Feeds
If you think you can reduce and/or avoid some of the costs above by reducing staffing requirements, or the cost of third party feed options, you might be able to save from a cost standpoint, but you will be hard-pressed to provide a solution that can stand up against the competition in an already saturated cybersecurity market. When it comes to evaluating different threat intelligence feeds for quality, here are several things you need to carefully consider.
Threat Feed Subscriptions
The cost of a different threat feed subscriptions vary, but is in the range of roughly $1,500 to $10,000 per month, depending on the number of data feeds in the subscription. And, even on the more expensive end of the scale, there is little overlap in coverage from one threat feed to the next, so achieving broad global threat protection requires aggregating and ingesting numerous feeds. You could try to stretch your budget by opting for only a couple of threat feeds, but that severely limits your visibility across the threat landscape and will fail to deliver adequate threat protection.
Traffic Input
Traffic Input is critical for threat feeds as it determines geographical and industry coverage. Some feeds may focus on collecting threat intelligence that is limited to specific high-risk industry verticals like finance or healthcare. Some may have broad coverage across the industry verticals, but only have threat data that is specific to certain geographical locations. Knowing the traffic input is crucial to understanding the volume and visibility the different threat feeds can deliver. Ideally, you want to look for threat feeds that offer a high volume of global traffic reach across as many industry verticals as possible to maximize coverage.
Threat Feed Aggregation vs Curation
While aggregating cyber threat intelligence feeds may be effective in terms of compiling a dataset of IOCs in one place, it also creates a signal to noise problem because many are inactive threats, false positives, or just have little to no relevance to an organization’s unique operating environment. More often than not, rather than focusing on prioritizing and mitigating active threats, defenders are often plagued by alert fatigue as they are routinely steered towards wasting valuable time on unnecessary investigations, or simply left unable to take any effective action because there are just too many irrelevant IOCs to be useful in the first place.
Since the definition of what constitutes ‘curated’ cyber threat intelligence feeds vs aggregated threat feeds varies depending on the source, it’s crucial to understand how the different feeds are curated. Each company is likely to have its own proprietary sources and methods for collecting and curating data. From our experience, producing high quality in-house cyber threat intelligence data is both extremely challenging in terms of normalizing the various data feeds for a common view of the data — and quite expensive. To properly curate IOCs and threat data, it requires a 24/7 team of analysts to review and resolve potential false positives within minutes, as well as a team of threat analysts to track threat actors, TTPs, emerging attacks, as well as to provide data annotation and feedback to the teams that create the AI models.
Staffing Challenges
If you have the budget to secure the staff necessary to support doing in-house cyber threat intel, filling those roles will prove difficult amid the current shortage of available cybersecurity talent. According to a recent Fortinet survey, 60% of organizations struggle to recruit cybersecurity talent. If you’re lucky enough to secure qualified talent, you may struggle to keep them. The same survey indicated that 52% of companies struggle to retain qualified talent. The reasons behind retention problems vary from one organization to the next, but if you’re trying to build your own solution that is plagued with inefficiencies, your team may end up on the fast track to alert fatigue and burnout resulting in high turn-over. Instead of focusing on improving your solution, you end up caught in an endless cycle of trying to recruit, hire and train your team.
Time is Not on Your Side
The volume and velocity with which new attacks proliferate across the threat landscape is only increasing. Building an in-house cyber threat intelligence solution into an XDR, MDR, MSSP, or Incident Response business strategy requires years — a luxury that your current or ‘would be’ prospects cannot afford. Ultimately, if you’re not starting from a position where in-house cyber threat intel is already a core competency, your best strategy may be to leverage an industry-leading CTI provider with highly curated and unique threat detections with low false positives that can deliver CTI for a fraction of the cost of doing it in-house — allowing you to focus on growing your business.





