As the popularity of the InterPlanetary File System (IPFS) grows, so does the risk it poses. Initially developed using Web 3.0 technology in 2015, the adoption of IPFS is driven largely by data privacy, and the desire to reduce reliance on centralized big tech companies like google, Microsoft, Facebook, etc. Unfortunately, increasing adoption rates also include a contingent of threat actors who have been quick to weaponize the IPFS technology over the last couple of years to expand their cybercriminal enterprises. This article will provide a brief overview of IPFS, how malicious attackers are leveraging this technology for phishing attacks, and best practices to protect your organization against IPFS phishing attacks.
What is IPFS?
The InterPlanetary File System (IPFS) is a modular suite of protocols to organize and transfer data. As an open-source technology, there are numerous implementations of IPFS although the main use case is for publishing data (files, directories, websites, etc.) in a decentralized fashion. More simply put, IPFS is a modern way of sharing and storing information on the internet that focuses on efficiency, reliability, and decentralization.
Unlike traditional methods, which rely on a central server or authority, IPFS connects individual computers in a network, allowing them to work together and share information directly with each other. When you access a file or website using IPFS, the system breaks the data into smaller pieces and distributes them across multiple computers on the network, referred to as nodes. Each piece is given a unique fingerprint, known as a hash, which helps to identify and locate it. Instead of requesting the entire file from a single server, your computer collects these individual pieces from multiple sources within the network, making the process faster and more resilient to failures.
This decentralized approach makes it more difficult for information to be lost or censored, it also allows for better use of available resources, as computers can share data directly with their neighbors, reducing the load on centralized servers. When used for legitimate purposes, IPFS uses cryptographic hashes to verify the authenticity and integrity of files to prevent attackers from tampering with or deleting files. The flip side, however, is that defenders are equally challenged when it comes to removing any phishing sites or malicious files they discover.
How Attackers Use IPFS in Phishing Attacks
Open-source technologies while fostering collaboration, innovation, and diverse implementations, also present opportunities for threat actors to broaden their attack surface. IPFS is no exception, particularly in the realm of phishing attacks.
IPFS phishing attacks operate in the same way as phishing attacks through a centralized network, where attackers use social engineering techniques, email and messaging platforms, and cloned websites to impersonate legitimate brands with the intent to harvest a user’s credentials and gain access to a network. One key distinction, however, lies in the nature of IPFS. Once content is published on the IPFS network, it becomes accessible to anyone who can then republish it on their own node. By taking advantage of the distributed file system, IPFS makes it easy for attackers to create permanent and untraceable phishing sites that can remain active long after the original source has been taken down.
Accessing the IPFS network can be achieved through various methods, including desktop applications, IPFS Command Line Interface (CLI), browser extensions, web app integrations, or public gateways. In the context of IPFS phishing attacks, threat actors typically employ public gateways as proxies, enabling victims to open file access links regardless of whether they use any of the previously mentioned applications.
IPFS Phishing Attack Example
The following 2 images show one example of an IPFS phishing attack that zvelo has detected within the last several days. As you can see in this example below, the phishing page impersonating a Microsoft login page isn’t particularly creative or complex — most IPFS phishing attacks observed have been fairly basic.
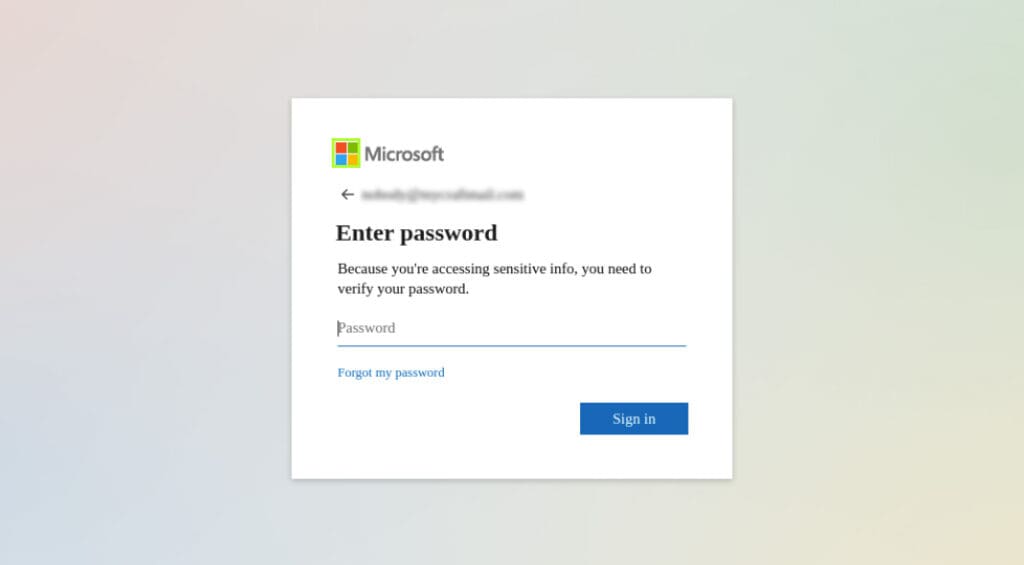
Like most phishing sites, it can be nearly impossible for an end user to visually differentiate between a fraudulent site vs a legitimate site.
![]()
The URL (shown above) clearly shows that the content is hosted on the IPFS network, but that isn’t really an indication of anything significant because there is nothing inherently good or bad about IPFS content.
Mitigating IPFS Phishing Attacks
There also isn’t a reliable way to differentiate between benign IPFS activity and that which is malicious. As organizations face the increasing threat of IPFS phishing attacks, they have a couple of options when it comes to leveraging cyber threat intelligence to implement or improve phishing detection.
The first option would be to block all IPFS gateways at the domain level, barring end users from the ability to access that type of content entirely. The risk with this approach is that you cut off access from an entire network that has shown a great deal of adoption and demand in the last couple of years. Although IPFS doesn’t have the same widespread adoption as other centralized file sharing services like google drive, One Drive, Drobox, the risk that comes with blocking the at base domain is the same ‘all or nothing’ approach.
The most effective option would be to ensure that you have the capability to block full-path URLs. In this manner, you would be able to maintain access to the network but still have the added security that users would be blocked from accessing any phishing or malicious files and links.
zvelo Solutions
zvelo’s premium threat intelligence feeds for phishing and malicious threats deliver the full-path threat protection required to power your security platforms and applications with robust defense against IPFS phishing attacks.
PhishBlocklist
PhishBlocklist offers proven market-leading detection coverage and speed of active phishing threats from the global ActiveWeb traffic stream across web surfing, email, SMS/text and other applications. Further enhanced with zvelo’s predictive phishing detection, PhishBlocklist delivers validated active phishing threats that are enriched with additional metadata attributes like date detected, targeted brand, phishing campaign identification, and more.
Malicious Detailed Detection Feed (MDDF)
Malicious Detailed Detection Feed delivers curated malicious intelligence data which identifies, confirms, and enriches malicious IOCs with a range of metadata attributes such as date detected, malware family, and many key intelligence attributes which can be used for further analysis and enrichment.
Please contact zvelo for more information if you have questions about PhishBlocklist, MDDF, or how to best protect your organization from IPFS phishing attacks with premium threat intelligence data.





