TTP: Living Off The Land at Scale
by Brad Rhodes, zvelo Head of Cybersecurity
While it is not the holiday season, one of my favorite movies that time of year is White Christmas starring Bing Crosby and Danny Kaye. Near the beginning of the film, Bob (Bing Crosby) says to Betty (Rosemary Clooney), “No need to apologize. Everybody’s got an angle”. In the complex world that is the Internet today, threat actors are always looking for their next ‘angle’, and the Tactic, Technique and Procedure (TTP) described here is no different. From a threat intelligence perspective, the TTP we’re going to present can be best described as Living Off The Land at Scale (LOTLS). LOTLS fits nicely into the Delivery portion of the Lockheed Martin Cyber Kill Chain (figure 1). LOTLS is great for threat actors as the cost is free (we will get to that).

(Figure 1: Note the colors are important in this diagram. Gray is open Internet, Red happens in threat actors’ spaces, and Blue indicates the inside of the defended perimeter.)
Let’s define some terms so that we have a common understanding of LOTLS. Traditionally, Living Off The Land has been used to describe the actions of a threat actor who wants to remain in an environment long-term and avoid detection. In an enterprise network, threat actors would ‘live off the land’ using the tools available and allowed in the environment, such as Powershell, psexec, Windows Management Interface Command-Line (WMIC), and even Group Policy Objects (GPO) — a more recent addition to this mix. In short, threat actors infiltrate the target environment and discover which tools they can use, and which ones are not well monitored so they can just hang out. LOTLS takes this concept and expands it by using cost effective, if not free, offerings to support their campaigns. The zvelo threat intelligence team has observed LOTLS used in concert with threat actor phishing efforts, likely to some degree of success. As a basic term, phishing means you are using email to trick a victim to visit a suspect website that appears to have some legitimacy (we will share an example in this article).
So What Exactly is the LOTLS TTP?
Fortunately for threat actors, LOTLS could not be easier. Unfortunately for defenders, it directly targets their users. In particular, it targets the remote access users, as they have become an easier target amid widespread stay at home mandates due to the COVID-19 pandemic. LOTLS takes advantage of the plethora of free form builder product offerings on the market today. The TTP is quite simple. The threat actor registers for multiple forms from their preferred vendor(s). As long as they stay below the established usage/complexity threshold, the out of pocket cost is zero. The threat actors then build enticing and potentially realistic looking pages to hook their victim. On the page, the victim clicks on the provided link and is redirected to a site that looks suspiciously like a Microsoft-branded login page. Due to the free nature of these sites and the limited verification by the providing vendors, threat actors can stand up and tear down LOTLS ‘infrastructure‘ at will. The only thing that remains constant is likely the redirect page, which is the credential harvester.
Here is an example of LOTLS recently observed by Team zvelo. First, the victim received an email asking them to visit a site to check for an important document. The first clue of evil in this case was that the link intending to hook the victim appeared to have been created using a Domain Generation Algorithm (DGA). Had the victim actually clicked on the link, he or she would have immediately landed on a page that was created by using a free form builder as shown below.
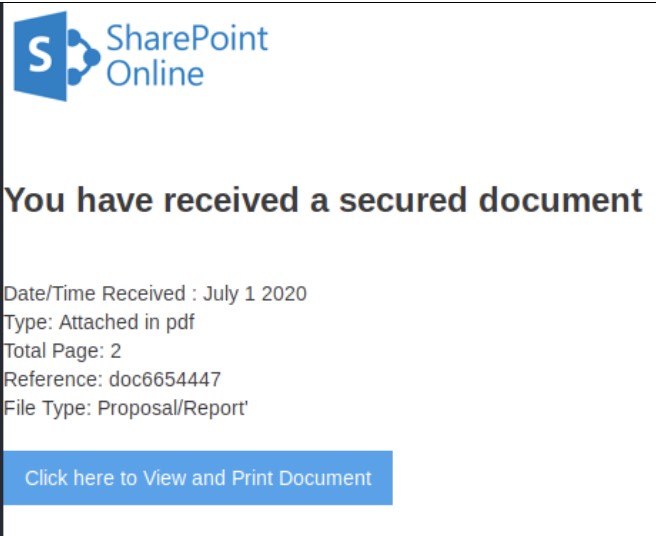
If the victim had clicked on the button as requested, they would have been sent to another page as shown in the image below.
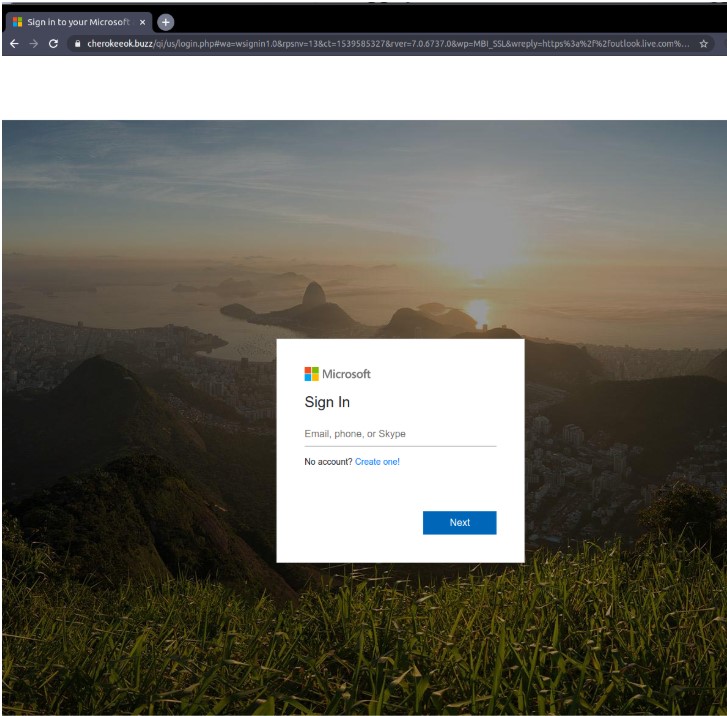
The page shown above is from a well-known malicious site, and is a simple credential harvester. If the victim had not been paying attention and signed into this site, their Microsoft account would have been compromised, which would have led to unforeseen consequences. LOTLS works for three main reasons:
- First, these resources are very low cost, if not free, for everyone — including threat actors.
- Second, the providers of these resources don’t monitor or police their offerings, and only bring down these “forms” if someone reports it to them.
- Third, it is easy for threat actors to scrape legitimate sites in order to create fake pages that resemble the real thing closely enough to evade detection by the human eyeball.
LOTLS presents a unique challenge from a threat intelligence perspective as the threat actors are using multiple TTPs found in MITRE ATT&CK to snag their potential victims. For example, we see T1556: Phishing (https://attack.mitre.org/techniques/T1566/) in the initial delivery. Next comes T1190: Exploit Public-Facing Application (https://attack.mitre.org/techniques/T1190/ for part two of this attack. However, I would argue that the threat actors did not “exploit” anything, they simply used the tool as designed for their own nefarious purposes. Finally, we have T1199: Trusted Relationship (https://attack.mitre.org/techniques/T1199/) attack. This is the final step in LOTLS. By using the fake Microsoft account login page, the threat actor is able to elicit the credentials they need to effect their actions on objective (likely Exfiltration in the Actions on Objective part of the Kill Chain). It is important to note that LOTLS skips the exploitation, installation, and C2 pieces of the Kill Chain, getting the threat actors to the prize without even having to move around in your environment.
What Actions Can You Take?
- First, educate your users about TTPs such as LOTLS that combine a number of pieces. As you improve your defenses, threat actors may string together multiple vectors to victimize your workforce and go after your intellectual property.
- Second, invest in one or more threat intelligence feeds that can be tuned to your environment to protect your employees and data.
- Finally, integrate response to combined TTPs into your organization’s incident response plan to prepare for these increasingly easy to deliver attacks.





