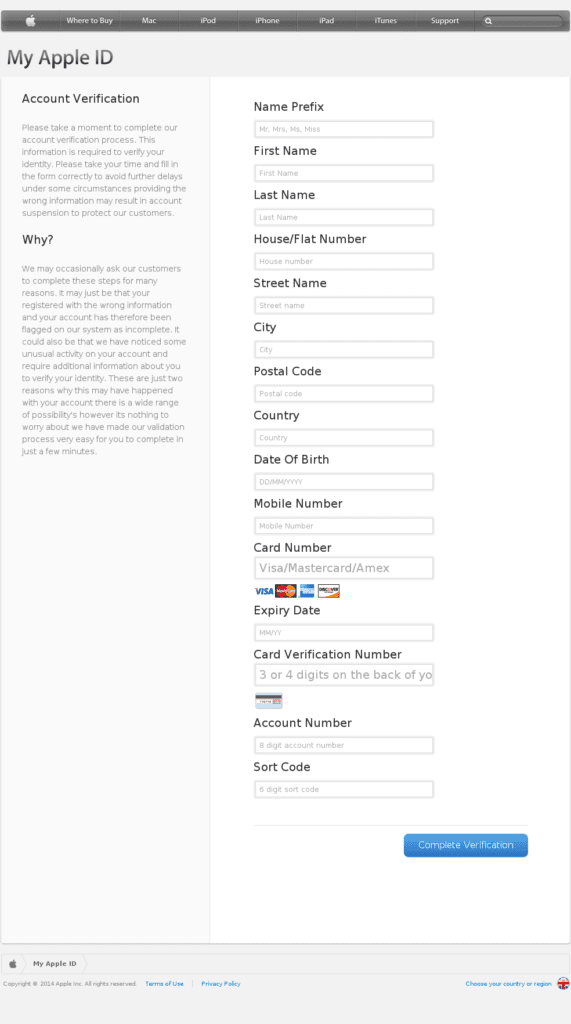
Fraudulent My Apple ID account verification phishing URL detected by zvelo
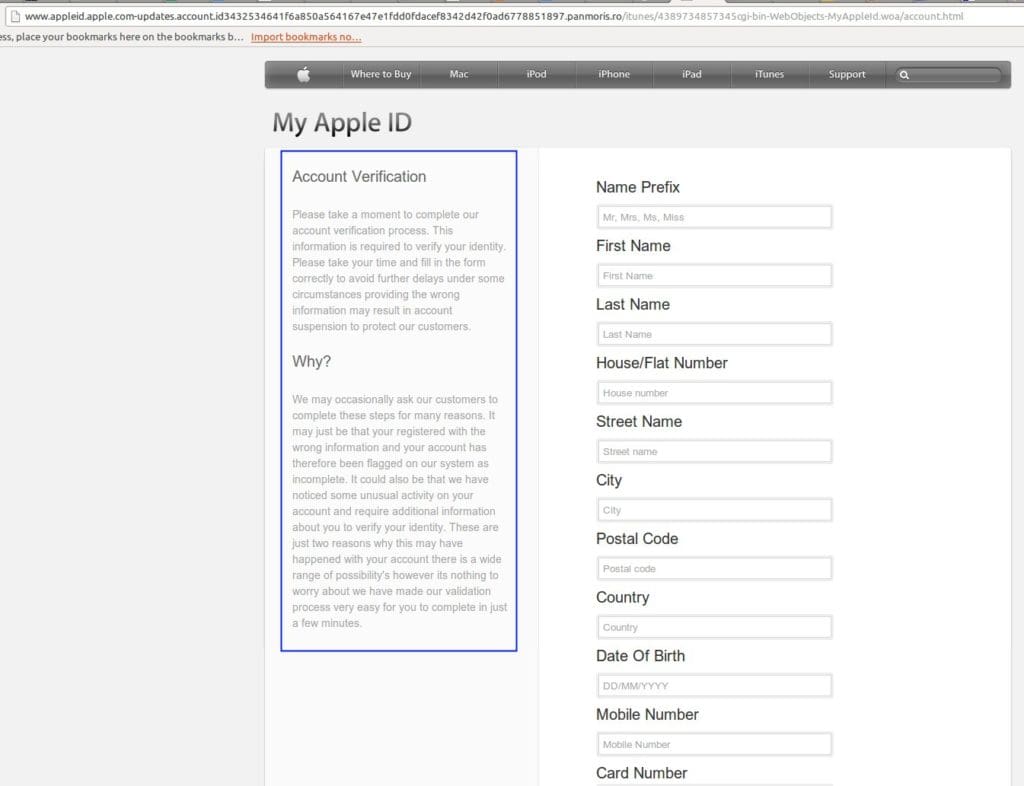
Recently, phishers tried to exploit Apple users to gain access to their accounts. They used a fake verification page to ask unsuspecting users with Apple IDs to verify their account by supplying personal information as well as credit card details. The author used similar trickery as other phishing websites to make users believe that it is a legitimate web page.
‘First, the phishing website used a layout and icons similar to the real Apple ID verification page, as shown below.
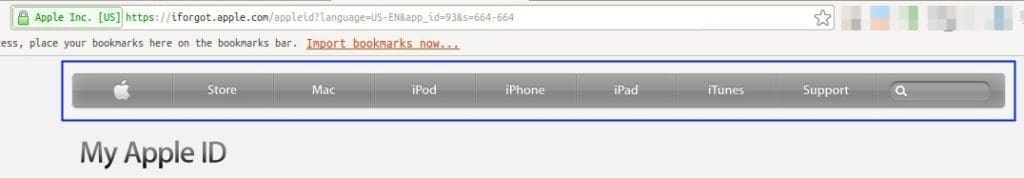
Header of the real My Apple ID account verification website
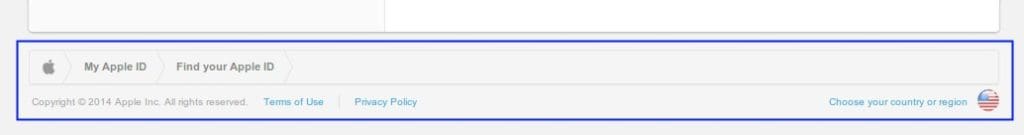
Footer of the real My Apple ID account verification website
Second, the author added the apple.com domain in the URL of the fake website as part of the long subdomain to conceal the fake domain used.
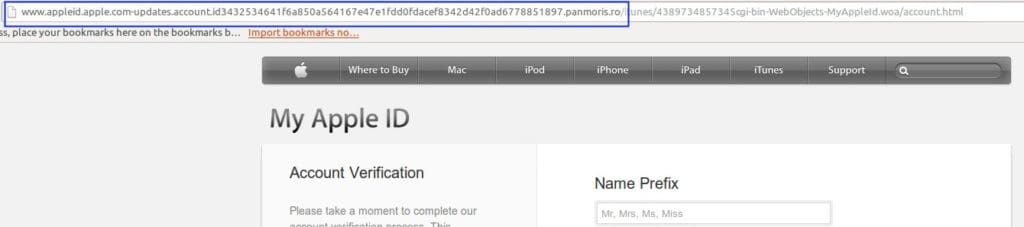
“appleid.apple.com” was hidden within the phishing URL detected
Examining the URL closely by dividing it into subdomain, domain and path reveals that this web page is under the domain panmoris.ro.
Subdomain:
www.appleid.apple.com-updates.account.id3432534641f6a850a564167e47e1fdd0fdacef8342d42f0ad6778851897
Domain:
panmoris.ro
Path:
/itunes/4389734857345cgi-bin-WebObjects-MyAppleId.woa/account.html
The author also used familiar Apple keywords like “iTunes” to make it appear that the page is legitimate.
Lastly, to convince the users to input their personal information, an elaborate warning at the left pane was added to explain the purpose of the verification page and to stress concern about the user’s security.
At the time of detection, only zvelo had detected the URL as “Phishing/Fraud”.
Virus Total Analysis:
https://www.virustotal.com/en/url/2d433735faef8957df09eef4fd28c84761735754aa9f0dbb189733564869a22b/analysis/1389588048/
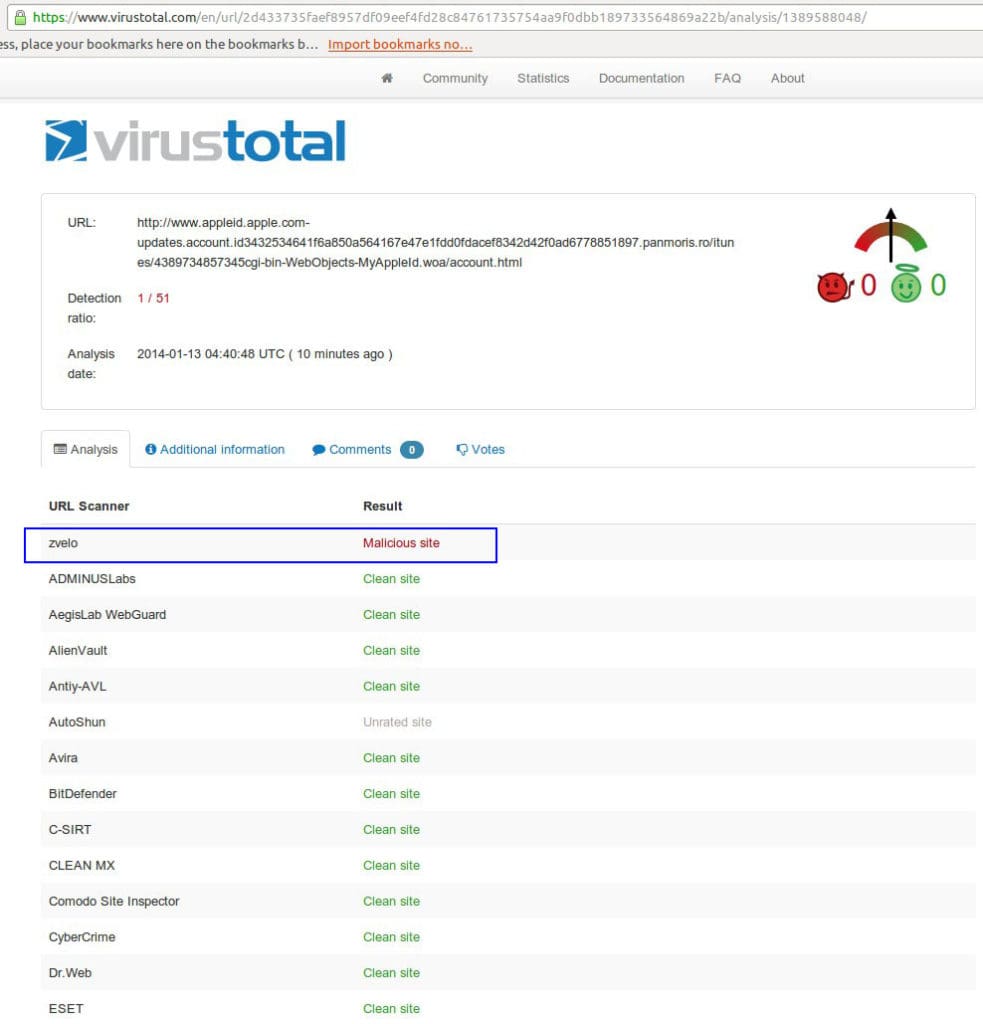
Virus Total scan showed that zvelo was the only software company to detect this phishing URL
Based on the site profile information from domaintools.com, the domain panmoris.co is hosted at the IP address 195.64.179.242 located in Romania. The domain was registered on 2005-01-06. In other phishing attacks researched by zveloLABS, the fraudulent websites used were newly registered, unlike panmoris.ro which has existed for 9 years. Research on panmoris.ro did not reveal any information about the site profile, or any past history of malicious activities. Thus, no definite conclusion can be made whether the the domain was compromised and was used for the Apple ID phishing attack or was created for the sole purpose of launching phishing attacks.
Further investigation showed that there were close to 100 URLs under the panmoris.ro domain used for phishing, but not all targeted Apple IDs. Some of the phishing URLs targeted the Royal Bank of Canada homepage. The layout and information of the fake homepage was similar to the real website.
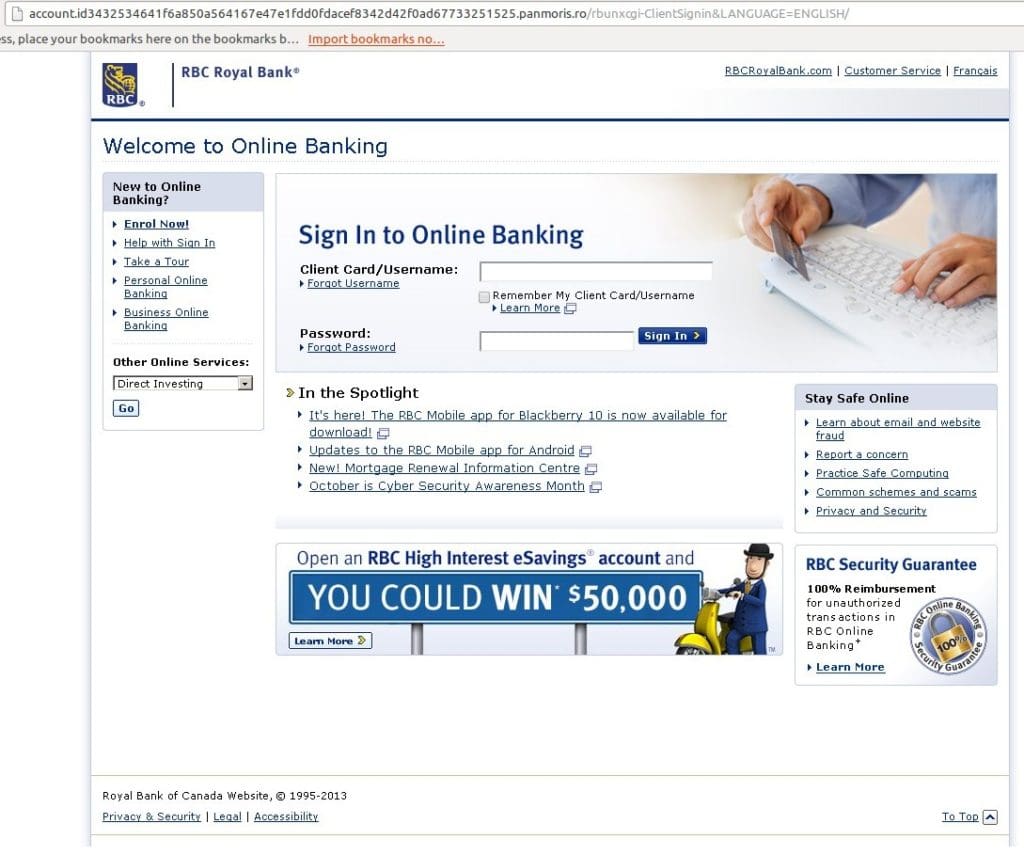
Other phishing URL formats used:
h00p://ituneapples879798797787897987awdawd.panmoris.ro/itunes/apple.php
h00p://theappletunes87897435com.panmoris.ro/
h00p://www.theappletunes87897435com.panmoris. ro/itunes/apple.php
h00p://apple.com-updates.account.id3432534641f6a850a564167e47e1fdd0fdacef8342d42f0ad67716214745.pan moris.ro/
The techniques and bogus web pages used for the Apple ID phishing attack are not new. However, despite the vast abundance of blogs, news stories and other online resources informing users about these types of malicious websites, countless victims continue to fall prey to such phishing attacks. That is why at zvelo, we are continuously enhancing our automated phishing URL detection systems and processes. We make sure that our systems are able to detect varying types of malicious websites even if the attacks or techniques used are trivial. Phishing and fraudulent website detection is one of the many content categorization services zvelo provides to its technology partners.





