Cybercrime is a significant and growing problem for organizations of all sizes, with new records being set in terms of costs, volume, and scale of attacks on a regular basis. From malware, to phishing, to ransomware and beyond, it’s critical for organizations to understand what it actually takes to protect their networks and sensitive information. The reality is that an organization could make significant investments to build the latest and greatest threat detection platform – like SASE, XDR, etc. – using a suite of different solutions and still fall short. That is not to say those threat detection tools and platforms are not critical, because they are. However, equally as important is that threat detection, and ultimately cybercrime prevention, is dependent upon the quality of threat intelligence data that is fed into those systems.
Challenges in Producing High Quality Threat Intelligence
Producing high quality cyber threat intelligence is a complex and difficult task. One of the major challenges in this process is managing aging data in threat intelligence feeds. Threat intelligence feeds can provide valuable insights into potential threats and vulnerabilities, but the sheer volume of data that is generated can make it difficult to effectively utilize this information. As the volume of data grows, it becomes increasingly challenging to sift through and identify relevant and accurate information, leading to potential issues with data overload. These challenges can make it difficult for organizations to effectively use threat intelligence data to protect against potential threats.
Approaches to Addressing These Challenges
To overcome these challenges, organizations must develop effective strategies for managing and curating aging threat intelligence data. This involves ensuring that the data remains accurate, relevant, and actionable, and that older threats are re-evaluated and removed if they are no longer active. Many threat intelligence feeds are frequently updated with newly discovered threats, but they may lack the diligence or capability to re-evaluate older threats and remove those that have been cleaned up or are no longer active.
One approach to addressing this problem is to arbitrarily prune the dataset once the data in the feed ages beyond a certain point. For example, some organizations may prune out entries older than a certain number of months. While this does solve the problem of unbounded growth, it also runs the risk of removing data that is still an active threat. An alternative approach would be to curate the data and age out information based on the current attack status.
An Example of Curated Threat Intelligence
To illustrate why the curated threat intelligence approach is crucial to cybercrime prevention, we’ll share a real-world example using a phishing threat. Phishing threats can vary greatly when it comes to the length of time an attack remains active. While the majority of phishing attacks are short lived and active for only a few hours to a few days, that isn’t always the case, and some phishing threats can hang on for a long time. Curated phishing threat intelligence is crucial to combatting the tactics, techniques, and procedures (TTPs) attackers use to evade detection which allows them to remain active for longer periods of time putting countless organizations and end users at risk.
For example, zvelo started tracking the following phishing campaign on September 12, 2022. As of, December 9th, 2022, the phishing threat was still active as can be seen in the following screenshot:
Hostname: abnamro.nl.mijn-abnamro.aanvragen-online.getexcitedevents.net
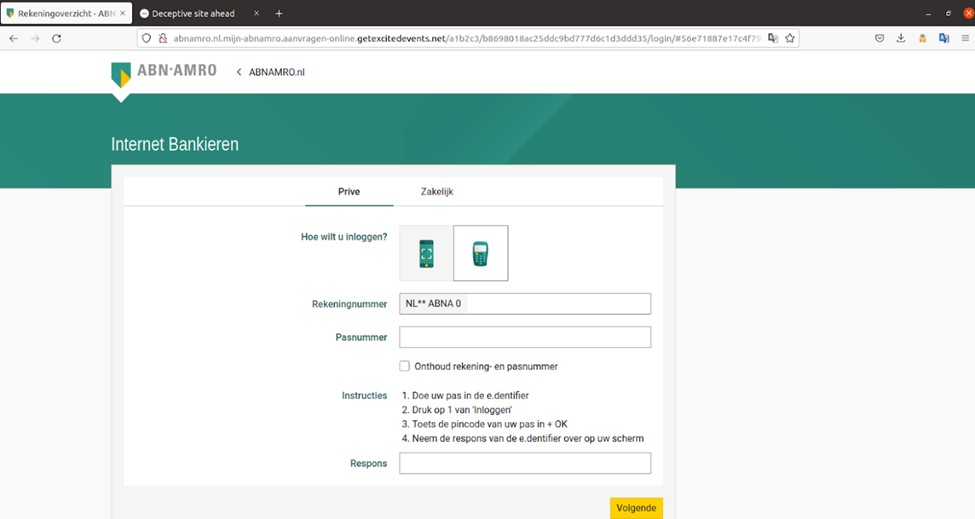
There are many reasons why a particular phishing threat may manage to stay active for a longer than normal time. In some cases the site is hosted on a bulletproof hosting site that doesn’t respond to abuse or takedown notices.
In this case, the site uses mechanisms such as returning a fake 404 error to visitors from IP address blocks it believes belong to security scanning solutions. While this tactic is fairly common in many phishing kits, the attacker behind this phishing attack adds an additional layer of bot detection by only serving up the page if a particular cookie is set in the visitor’s browser telling the web server to look for a cookie called ‘real’ with a value of ‘ok’ before it can serve up the phishing page – cloaking itself from security analysts and automated trackers. These tactics make it difficult for automated tracking processes to detect and track the attack so that it can be blocked.
The Crucial Role of Curating Threat Intelligence in Cybercrime Prevention
Building an effective system for monitoring and curating threats at scale requires significant resources including a global infrastructure to avoid IP-based or geography-based filtering; automated browsers that look realistic to web servers that are protected using antibot detection techniques; and AI-based approaches to automatically detect threats as well as to make proper decisions in a variety of complex situations.
High-quality, curated threat intelligence is a vital investment in cybercrime prevention. It is essential for organizations to understand the challenges involved in producing premium threat intelligence data and to develop effective strategies for addressing these challenges. Unfortunately, many organizations lack the budget and expertise to adequately address these challenges. More concerning is that many security vendors that claim to offer premium threat protection don’t even make these sorts of investments.
When considering buying or building your next threat intelligence solution, consider the critical nature of how threat intelligence data is managed with respect to aging data. Understand that a curated threat intelligence approach, in which data is managed and curated based on current attack status, is particularly important for ensuring that your organization, your clients and your end users have the most accurate, timely, and relevant information available to block potential threats to help prevent cybercrime.
.





