Mapping zveloCTI Threat Intelligence Data to the Pyramid of Pain for Indicators of Compromise (IOC)
Today’s cyber defenders face the unenviable challenge of facing threats to both known and unknown vulnerabilities in their systems from multiple MCAs on multiple fronts. Unfortunately for defenders, an MCA only needs to be right one time and an organization is compromised. To stay ahead of an increasingly complex technology landscape, cyber defenders have taken to utilizing models to understand their adversaries. Using these models, cyber defenders can look for patterns to help them identify the Tactics, Techniques, and Procedures (TTP) observed in an attack or incident so that they know how to stop the suspected MCA. Specific to cyber incident response (IR) we find the Pyramid of Pain model for assessing indicators of compromise (IOC). With the Pyramid of Pain, cyber defenders can determine the level of difficulty they can expect when tracking down an MCA that is or has been in their environment.
Pyramid of Pain Overview (Traditional)
The Pyramid of Pain was introduced by David J. Bianco (https://detect-respond.blogspot.com/2013/03/the-pyramid-of-pain.html) in 2013 as a way to define how cyber defenders might view IOCs in their networks. As a model, the Pyramid of Pain provided a way for cyber defenders conducting an Incident Response (IR) to quickly assess the data in hand, and determine if the task to secure the compromised environment would be easy or difficult.
Let’s look at the six layers of the Pyramid of Pain from the bottom (easiest IOC) to the top (hardest IOC).
- File Hashes: Every single file on a machine can be hashed (one-way-mathematical function) to produce a unique value for the contents. This includes malicious files. If you happen to grab the hash of a known or suspected malicious file on a host in your network, it is relatively easy to scan the rest of the environment to discover how widespread the infection happens to be. Even if the filename has been changed, the hash of the content does not. This is why file hashes are considered an easy IOC.
- IP Addresses: Fundamentally, if you want to connect to anything on the internet you must have an IP address. Whether IPv4 or IPv6, Layer 3 logical addresses allow routing from one place to another. As such, basic device-to-device connectivity is logged in most environments (hopefully, centralized using the Netflow or IPFIX standard). Thus, if you discover a host in your network connecting to a known bad IP address, it is relatively simple to find other machines doing the same.
- Domain Names: Humans are terrible with numbers. Who really wants to memorize an IPv6 address string to get to Google? The answer is no-one, hence we have the domain name system (DNS) which maps IP addresses to human-readable names (e.g. zvelo.com). Domain Names are a more difficult IOC to assess than IP addresses because the combinations across the Top-Level Domains (TLD) are almost infinite. When MCAs leverage this method, combined with Domain Generation Algorithms (DGA) and DNS fast flux, they have a recipe to rotate through multiple names with regularity — making it harder to pin them down.
- Network / Host Artifacts: Networks and the hosts that they support have usage characteristics that vary widely from one organization to the next, even if the exact stack is used. The human element, and the way organizations use networks and hosts, is the primary reason why they are organic and so varied. For example, User A downloads the malicious macro-enabled spreadsheet onto their desktop, while User B leaves it in the downloads directory. Now imagine you have 100s to 1000s of users in an enterprise, and your IR team has to find every instance of the malicious file. Have we mentioned yet that log formats vary across devices? Are you doing central logging? If you’re not, it is hard to even know where to start looking for these artifacts. Oops.
- Tools: Tracking down MCA tools at enterprise scale is increasingly challenging — especially with most conducting their evil in memory only. This is why tools IOCs are so difficult to grab. If you do not have a host artifact to inspect, did the incident actually happen? It did, but you will probably need a combination of all of the previous IOCs in the pyramid to pick up the trail.
- TTPs: Finally, we look at the behaviors observed during the incident (or maybe before if you’re proactively threat hunting) and try to determine which MCA is in play. TTPs are ultimately a combination of the previous IOCs in the pyramid. Most likely, you will need to use another model (e.g. MITRE ATT&CK) to ascertain a reasonable answer.
Mapping zveloCTI to the Pyramid of Pain
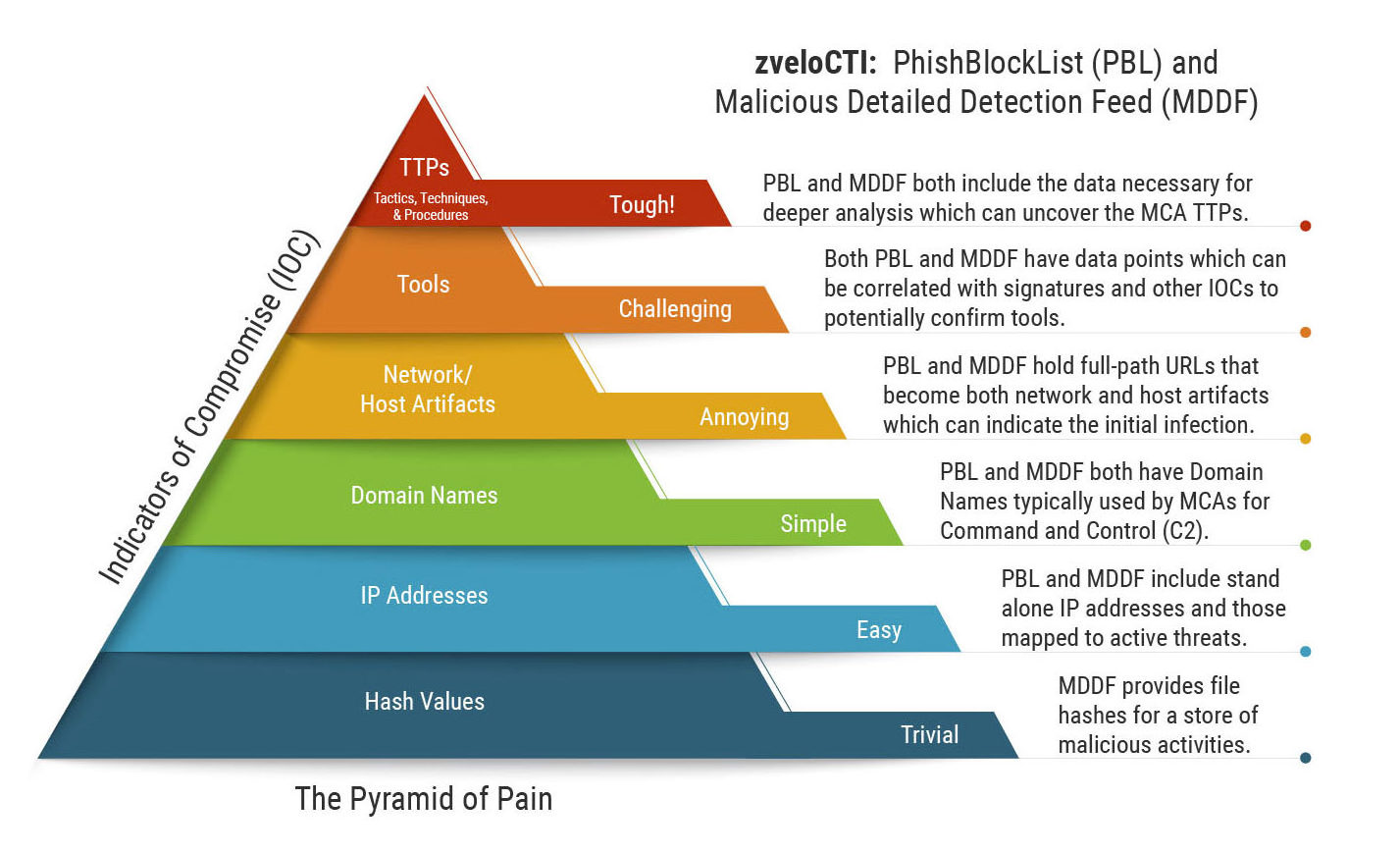
If you are a responder, analyst, researcher, or threat hunter, having the right seed data is critical and can accelerate your response during an incident or prevent it altogether. zveloCTI’s PhishBlockList (PBL) and Malicious Detailed Detection Feed (MDDF) are built to deliver high-fidelity, high-accuracy, and low false positive IOCs so your organization can head off MCAs before they strike. Let’s map PBL and MDDF to the Pyramid of Pain.
| Pyramid of Pain IOCs* | PBL | MDDF | zvelo Pain Points |
|---|---|---|---|
| File Hashes | MDDF provides file hashes for a store of malicious activities. These hashes can be used for threat hunting across networks or in incident response situations for verification of IR team findings. | ||
| IP Addresses | PBL and MDDF include two types of IP addresses. The first are stand alone IP addresses used by MCAs to serve phishing or malicious content. Next are IP addresses mapped to active threats (domains, subdomains, and full-path Uniform Resource Locators (URL)). As such, these IP addresses can be used in threat hunting across networks and hosts. | ||
| Domain Names | PBL and MDDF both have Domain Names (TLD+1 and subdomains), typically used by MCAs for Command and Control (C2). This data can be used for both threat hunting and proactive defense applications. | ||
| Network/Host Artifacts | PBL and MDDF hold full-path URLs. Lower-level MCAs (e.g. small-time cyber criminals) co-opt infrastructure and Live Off the Land at Scale (LOTLS) to exploit victims. When a user clicks on, mouses over, or gets hit by a drive-by-download, it will likely be a full-path URL. These full-path URLs become both network and host artifacts that can indicate the initial infection. | ||
| Tools | Both PBL and MDDF have data points that may indicate Tools (e.g. known Phishing Kits or Ransomware as a Service (RaaS) in use by MCAs). Correlating PBL and MDDF data with signatures and IOCs discovered can potentially confirm tools. | ||
| TTPs | Analyzing PBL and MDDF data, MCA TTPs can be found (e.g. LOTLS). The zvelo Cybersecurity Team is conducting that analysis right now and will be publishing the results in our annual Malicious Trends Report in October — stay tuned! |
* Availability of IOCs is dependent on sources, if a phishing or malicious site is online/offline, and various other factors.
A Word About Models
Models are just that, models. They are useful tools to make use of data you may or may not already have in-house. Not all models will be a fit for every organization. The key is picking the models that are most appropriate for your environment. There is a tendency to try to use lots of models which may be okay depending on the size and complexity of the organization, but usually this can be confusing for defenders and leadership alike.
Recommendations
The zvelo Cybersecurity Team has the following recommendations when it comes to leveraging IOCs and models:
- First, understand your cyber operating environment (COE) and what you can “see” in logging (hopefully, a Security Information and Event Management (SIEM) system). Don’t rely on a single capability (for example, Endpoint Detection and Response (EDR)). It is critical to look across the Defense-in-Depth and establish visibility throughout an enterprise.
- Second, after mapping the data in-hand, determine the best model(s) to use. Note, you may need one model for the defenders in your Security Operation Center (SOC) and another for your IR team. Regardless of the model(s) you choose, organizing IOCs logically will speed up response to an incident or breach.
- Finally, visualize the outputs of the models where possible. A picture is worth a thousand words!
zvelo’s PBL and MDDF can be leveraged to find Pyramid of Pain IOCs in your organization’s COE right now. Please contact us if you would like to try them out!





