Phishing is by far the biggest and most consequential cyber threat we face. In fact, 95% of corporate network attacks and data breaches are the result of a successful phishing attack.1 Over the last couple of years, the phishing threat landscape has evolved to a whole new level of sophistication. Phishing attacks rapidly morph by adopting new technologies and tactics — out-performing existing security layers. While we continue to see phishing attacks accelerate in volume and scale, we also see a sharp drop in the lifespan of phishing sites. The adoption of single-use phishing URLs is driving both the increased volume and decreased longevity of the phishing URLs.
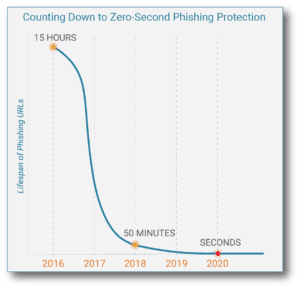 In 2016, about 84% of phishing sites existed for less than 24 hours, with an average life cycle of under 15 hours. In 2018, the average lifespan of a phishing site was under 50 minutes. Further, the median time for the first user to click on a phishing URL is only four minutes. Most recently, the increased adoption of ‘single-use’ phishing URLs slashes the time to live down to zero seconds from first user access.
In 2016, about 84% of phishing sites existed for less than 24 hours, with an average life cycle of under 15 hours. In 2018, the average lifespan of a phishing site was under 50 minutes. Further, the median time for the first user to click on a phishing URL is only four minutes. Most recently, the increased adoption of ‘single-use’ phishing URLs slashes the time to live down to zero seconds from first user access.
The fleeting lifespan of phishing URLs — further hastened by single-use URLs — is driving an urgent need for accelerated phishing detection and protection. Local threat databases must be updated with phishing detections in a matter of minutes, or even seconds, to adequately protect users. This type of zero-second phishing protection requires an entirely different approach to detection and protection.
For the purpose of providing some background context, a single-use, or one-time use phishing URL is a specially-crafted address that is valid for one access only. It’s usually provided to a user to gain privileged access to a file for a limited time or as part of a particular activity, such as user account validation. It’s what we see as the next generation of spear-phishing, which can be mobilized on a mass scale with minimal effort from those who deploy the phishing campaigns. The ability to deploy this type of phishing campaign comes readily available in phishing kits containing the PHP code to automatically generate each phishing site in milliseconds for each unique visitor, providing their own custom, one-time use phishing site.
The proliferation of phishing campaigns employing these single-use URLs reduce the lifespan of phishing sites from hours or minutes to literally seconds. It more critical than ever to prioritize up to the minute detection and protection — neither of which is inherently enabled through the standard phishing protection approaches.
Blacklist-based solutions are widely used but are becoming less and less effective in protecting users against these newest threats. Phishing URLs and web domains change too quickly for blacklist-based services to keep up. In the case of the single-use phishing URLs, by the time the URL has been processed by a phishing detection vendor or aggregation service, it’s too late — the damage is done the moment the user comes into contact with the URL.
Browser blocking, which is largely based on using external black- and blocklists, is also increasingly ineffective against the short-lived and single-use phishing URLs. Results of the NSS Labs browser security test showed that by the end of the first 60 minutes, automated browser-based protections range from 77.3% to 89.5%. While protection effectiveness increases over time to between 94.3% and 96.7%, that is well beyond the lifespan of the short-lived URLs and completely useless against the single-use phishing URLs.
Manual remediation is, perhaps, the most ineffective. According to a 2018 report from the Aberdeen Group, the median total time to identify, verify, and remediate using this approach to post-delivery incident response is more than three hours — only reducing your risk from phishing attacks by less than 5%.6
Combating the very short-lived URLs and single-use phishing URLs requires a completely new approach, involving real-time phishing detection ‘in-line’ as opposed to utilizing feeds from external threat detection vendors or blacklists. As we begin to see zero-minute detection losing its edge, an in-line detection solution may be the only method to enable maximum user protection through zero-second detection.
Thwarting these single-use URL phishing attacks continues to be a race against the clock. However, there are steps you can take to shut them down before they reach your end users.
First step is to streamline the workflows around threat feeds and updates to the databases protecting your users. It should take no longer than one hour at the most, from the time of phishing detection to the time your database protecting users are updated.
Some solutions may provide you with a feed that gets updated daily, or even every few hours. Those, however, can’t protect against the growing number of phishing attacks that come and go in less than an hour on average. And, if you receive a threat feed that is current, but don’t have a workflow that immediately updates the databases protecting your users, you still fail to deliver an effective solution.
Adequately protecting against the newest and most insidious forms of phishing attacks, will require you to identify how to implement real-time, in-line phishing detection to close the detection gap for single-use phishing URLs and provide zero-second detection.
When evaluating phishing detection and protection solutions, keep the following recommendations in mind:
- Ideally, you should identify and implement a real-time, in-line phishing detection solution. This is your best protection for users against even zero second, single-use phishing attacks.
- If implementing a real-time, in-line solution is not an option at this time, your efforts would be best spent on streamlining your workflow and update procedures. Minimize the time between the moment a phishing site is detected (from your vendor, service, other) to the time your database protecting users is updated. A good rule of thumb is to aim for a window of 30 minutes or less.
When it comes to phishing protection, time is of the essence and, quite literally, every second counts. Effective solutions must be able to deliver real-time, comprehensive and scalable detection and protection.
To learn more about how zvelo is delivering real-time phishing detection and protection, see zvelo’s PhishBlocklist solution. If you would like information about pricing or to schedule an evaluation, contact [email protected].





