From Person-to-Person (P2P) and Application-to-Person (A2P) messages, tens of billions of text messages are sent and received daily, making Short Message Service (SMS) the most common form of communication globally. And, as mobile usage has increased, the threat landscape has evolved from phishing attacks via email, to include phishing attacks via SMS messaging — Smishing. Short for SMS Phishing, Smishing is a form of phishing attack where Malicious Cyber Actors (MCA) trick the user into clicking a link, disclosing sensitive information, or downloading a trojan, virus, or other piece of malware using the text—or SMS—features on their cellular phone or mobile device.
While MCAs still heavily favor using email to phish unsuspecting victims, there has been an increased use of SMS and messaging platform channels to deliver phishing attacks – At least as much as 17% according to the Verizon Mobile Security Index 2020.
User Behavior Exposes Mobile Security Gaps
A mobile user is 18x more likely to be exposed to a phishing attempt than malware. And channels like SMS and messaging apps are being leveraged at scale to distribute phishing links. (Wandera).
Attackers are highly adept at finding and exploiting the security gaps exposed through human fallibility. And when it comes to mobile devices, SMS and messaging platforms in particular, attackers are exploiting user behavior and using Smishing as the attack vector for their phishing campaigns. Below are just a few basic statistics which demonstrate the interdependent relationship users have with their mobile devices.
- Mobile accounts for approximately half of web traffic worldwide. In the third quarter of 2020, mobile devices (excluding tablets) generated 50.81 percent of global website traffic. (Statista)
- The average US adult will spend 23 additional minutes per day on their smartphones in 2020. Messaging, in particular, is expected to rise by 4 minutes. (eMarketer 2020)
- 98% of text messages are read and 45% are responded to, while the equivalent numbers for email are 20% and 6%. (Gartner)
As businesses continue to recognize the benefits of using SMS and messaging apps to facilitate legitimate communications with their customers, the MCAs are increasingly co-opting the same tactics to distribute phishing links which drive unsuspecting users to phishing sites.
Improving Smishing Protection
While it’s important to recognize the factors which make Smishing an attractive attack vector, it’s also critical to understand that it’s also only the potential access point for an attack. Mobile devices are no different than most other enterprise endpoints – except that the widespread BYOD policies used by 90% of enterprises (IDC 2019 Mobile Security Vendor Report), leave these endpoints unprotected.
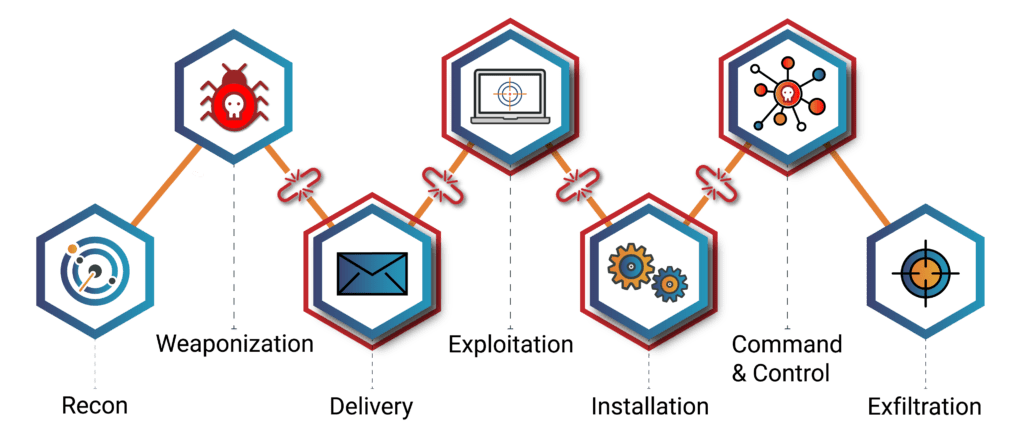
Enterprise Mobile Management (EMM) vendors, Communications Platform providers and Mobile Networks have a big role to play in preventing Smishing by either blocking access to bad URLs sent via texts and messaging apps, or by developing solutions which remove the malicious links before they are delivered to the target. And to increase phishing protection – whether it begins with Smishing, email or other mobile vulnerability – vendors need to develop solutions which leverage a multi-vector security approach armed with the capability to break the kill chain at multiple points of the phishing attack.
In the end, it’s important to keep in mind that Smishing foreshadows the problems presented by 5G, where every device is connected to the internet but not necessarily behind “walled gardens” that often are the backbone of security.
zvelo’s Premium Phishing Protection
PhishBlockList is an advanced phishing intelligence feed for vendors seeking to boost phishing detection and premium defense for their solutions. PhishBlockList delivers the insights and actionable phishing intelligence required to block adversaries along various points of the kill chain. PhishBlockList spans several potential attack points for robust and comprehensive protection against phishing attacks.