Estimated Reading Time: 5 minutes
Tactics, Techniques, and Procedures (TTPs):
Malicious Cyber Actors Look to Exploit the COVID-19 Pandemic
When the World Health Organization (WHO) declared COVID-19 (more commonly known as the “coronavirus”) a pandemic on March 11, 2020, the world began grappling with large-scale impacts to daily life. As world leaders called on their citizens to prepare for these impacts, another group began rolling out their own plans to take advantage of the situation. This “other” group is made up of Malicious Cyber Actors (MCA) who have been biding their time procuring internet infrastructure, registering domain names, writing or reusing code, scraping content, and looking for victims. It is important to note that the term MCA is meant to span the spectrum from script kiddies to Cyber Criminals to Nation State actors. All can leverage the same Tactics Techniques and Procedures (TTP) for different goals. While the initial MCA campaign related to coronavirus was relatively quiet, the US Department of Health and Human Services (HHS) was hit by a suspected Nation State actor on Sunday, March 16. This is not the first time that MCAs have looked to take advantage of a “disaster” to further their end goals (be it for fun, stealing personal information, theft of intellectual property, etc…), just look at what happened during Hurricane Florence in 2018.
Over the past two weeks, zvelo has investigated thousands of domain names, registered since January, which are related to the coronavirus. By and large, domain name registrations occur on a daily basis and are usually not nefarious. Domains are usually purchased to support a business, brand, or for some other legitimate reason. MCAs also purchase domains to support their activities which includes a common technique known as domain squatting. This is where an MCA purchases a domain that is one character off from the actual domain hoping that a potential visitor will mistype and land at their website. Domain names can be a money making proposition. The introduction of Generic Top Level Domains (gTLD) by ICANN made even more domain name space available for use by for good and potentially bad.
In analyzing the coronavirus-related domain data, our Cybersecurity Team identified two trends of interest. First, some of the registrations were created for specific geographies. Three examples are: coronaviruscalifornia[.][TLD-redacted], coronaviruschicago[.][TLD-redacted], and coronavirusitalia[.][TLD-redacted]. In light of the current world situation, these types of domain registrations may be for legitimate purposes. The coronavirusitalia[.][TLD-redacted] is particularly interesting because it was registered outside Italy and includes email servers. Although not confirmed to be specifically malicious, these types of registrations are suspicious as they are exactly what MCAs could use to serve malicious content to fearful populations.
The second trend our Cybersecurity Team identified is the use of redirectors. Similar to domain name registrations, redirectors can be used for both good and bad purposes. On the good side, redirectors are used to protect brands, push customers to specific content, and support legitimate ad tech. For example, a large organization might procure a gTLD related to their brand to prevent someone else from doing so. On the bad side of things, MCAs utilize redirectors to herd victims to sites either hosting or delivering malicious content. It is not uncommon in the cyber domain to observe seemingly good techniques and technologies (in this case redirectors) being used in the same fashion by the good, bad, and ugly actors on the internet.
Upon further review of the coronavirus-related domains, zvelo identified two redirectors that pointed to what appeared to be a suspicious domain. In the course of our investigation and collaboration with organizations involved, we learned that the suspicious domain was actually stood up for legitimate purposes*.
The story does not end there. After observing the website furnished via the previously suspicious domain, our Cybersecurity Team discovered it was delivering a malicious payload, specifically, corona-virus-map.com.exe.
(known malware: https://www.virustotal.com/gui/file/2b35aa9c70ef66197abfb9bc409952897f9f70818633ab43da85b3825b256307/detection).
This executable delivers AZORult malware which steals cookies, browsing information, usernames and passwords, and other personal information. Specifically, some part of the website (an external link, a script, or third-party content) appeared to be reaching out to coronavirusstatus[.]space to drop the previously mentioned executable. It is also possible that the website in question was not directly compromised but that one of the pieces of third-party active content was the culprit. Either way, visitors to the website utilizing Windows operating systems to connect to the website would have unknowingly downloaded this malicious content and potentially had their data stolen.
Our Cybersecurity Team was able to grab a copy of the executable via the website in question and detonate it utilizing the any.run sandbox (https://any.run/) with the results shown here:

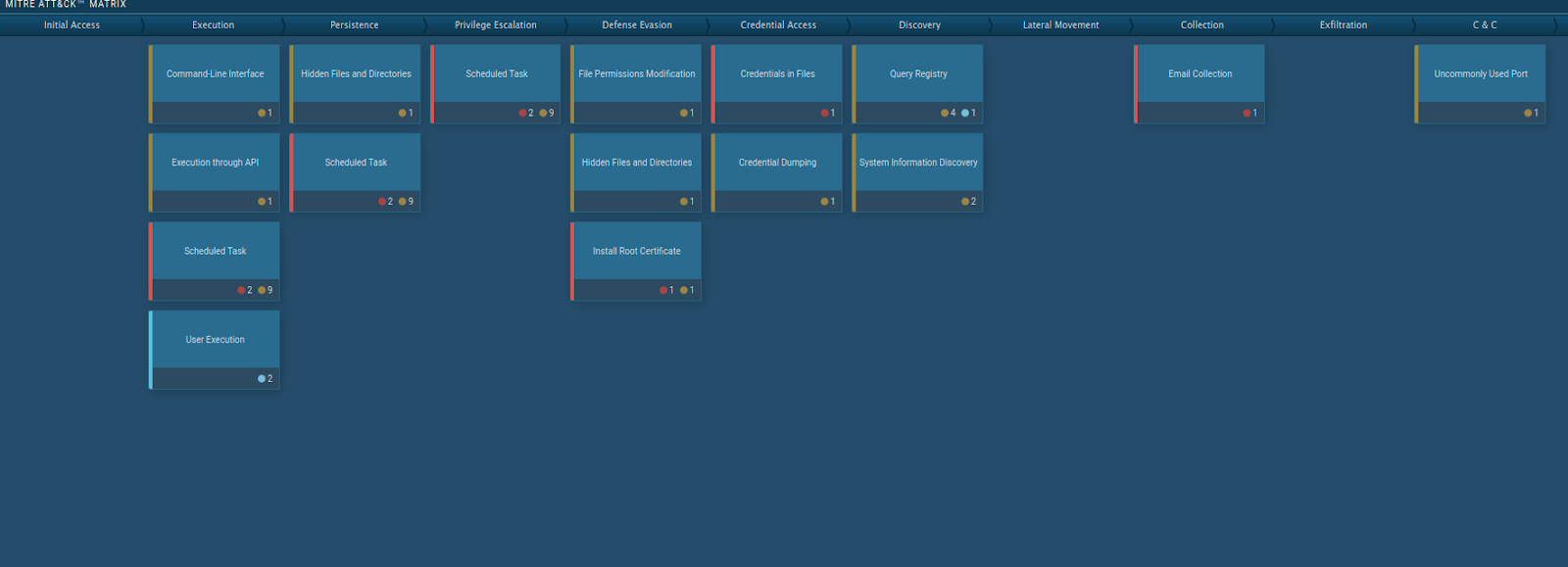
The good news for the owner of the website in question and potential users is that coronavirusstatus[.]space was taken down by the content delivery network where it had been hosted a few hours after the malicious behavior was observed. zvelo made responsible disclosures of our discoveries to the parties involved to ensure transparency, and foster an ongoing dedication towards working with other organizations to help to make the internet safer for everyone.
Take Aways and Recommendations
- MCAs are paying attention to the world situation and will look to take advantage of people when they are most vulnerable. Fear and uncertainty can and will be leveraged to great effect.
- MCAs only have to get it right once to compromise an organization or your friends and family. This is what MCAs are counting on, so do the basics: Complex passwords (even better with Multi-Factor-Authentication), patch/update your systems, refresh anti-virus signatures regularly, and use a VPN. Be a hard target!
- Website developers should implement secure development techniques to include sandboxing sites prior to deployment including all external links, scripts, and third-party content. Websites can be compromised both directly and indirectly.
- The general public should be vigilant now more than ever. Scams are everywhere. Be careful what you click on even if you “trust” the link. Slow down and be wary of official looking emails promising unreasonable things or requesting payment to secure treatment for a loved one, they are most certainly fake.
- If you are working from home right now, be sure to continue to leverage your organization’s security team if you think you have been compromised or are a target. You are never alone in cyberspace. Your cyber defenders are ready to stand in the gap so you do not have to!





