Earlier this year, zvelo announced extended support for two separate crypto categories: Cryptocurrency and Cryptocurrency Mining. These website categories offer improved identification and protections against malicious cryptocurrency mining for our partners in web filtering, anti-virus, network security, and ad tech who use the zveloDB™ URL Database and other deployments.
First off, let’s make it clear that there is nothing inherently malicious about the act of cryptocurrency mining. Rather, over the past couple of years cybercriminals and bad actors have leveraged existing exploits and found unsecured hardware to implant malicious coinminers and steal CPU/GPU cycles from computer owners and website visitors without their knowledge. These activities are what we refer to as “Malicious Cryptocurrency Mining“.
The category, Cryptocurrency Mining, has been implemented as a “malicious” category, providing identification of “cryptomining” or “coinmining” instances that do not properly notify or seek a visitor’s permission—or that commandeer more resources than advertised.
In this article, we’ll dive into the basics of cryptocurrency mining and explore the malicious coinmining trend.
So, What’s the Big Deal With this Crypto Craze?
Cryptocurrency has experienced an explosion in popularity over the past decade—creating a range of new digital-based methods for trading, generating value, and generally confusing millions of people around the world. Digital currencies like Bitcoin, Ethereum, Monero, and others have become a major trend not just in the trading and investment world—but having proposed technological applications in virtually every industry imaginable (many less than realistic). The excitement was only fueled in 2017—when over the course of the year Bitcoin surged in value from just under $1,000 (USD) in January to briefly over $19,000 in December. Here’s a look at Bitcoin growth for the year.
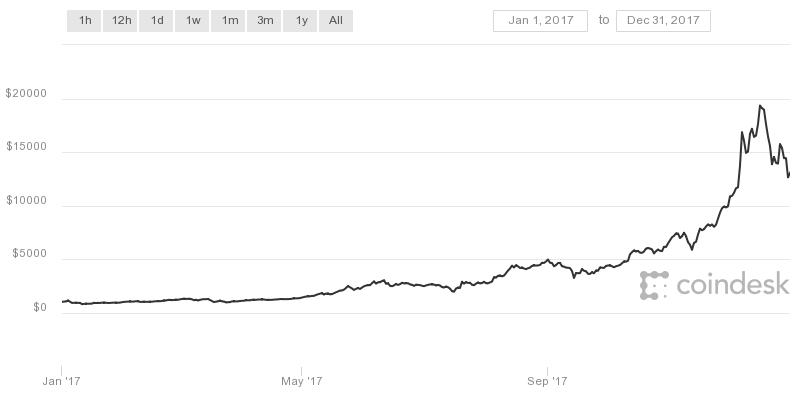
Bitcoin Value Surges in 2017 from $997 to briefly over $19,000 (USD)
The major advantages of cryptocurrency reside in its decentralized nature. This means that the global computing network of cryptocurrency participants jointly manage the database that records transactions—rather than relying on one central authority (banking or other institution). This peer-to-peer networking approach provides a number of freedoms and advantages, as well as redundancy (removes single point of failure/abuse)—reducing the potential power any one entity has over the entire system.
Additionally, cryptocurrencies provide anonymity (or pseudo-anonymity in Bitcoin’s case, since some traceability exists) giving transactions and users a level of privacy—perfect for illicit or “underworld” dark web behaviors. With traditional banking and payment systems, an individual’s identity is inherently connected to their account—making every transaction traceable. Not the case with cryptocurrency—whereas at the protocol level there is no connection to a user’s identity.
At this point—it may sound like blockchain and cryptocurrency are the best inventions since sliced bread. It’s going stop climate change, solve world hunger, and the like. Right? Maybe—maybe not. Time will tell. But, as with any technology or system that generates or provides value, we will inevitably see adoption for both good and nefarious purposes. Cryptocurrency is no exception.
What is Coinmining vs. Malicious Coinmining?
Mining cryptocurrency is the act of allocating a computer’s processing power (CPU or GPU cycles) to perform (or solve) intensive computations. Basically, every time a transaction is made with a digital currency, it is the responsibility of cryptocurrency miners to verify that transaction and add it to the decentralized ledger—thereby contributing to the overall system. For providing the value of performing these computations (or verifications), the individual allocating computer hardware is compensated with fractions of cryptocurrency. This is where the concept of “mining” is derived, producing trace amounts of a valuable material from the work.
For a savvy tech-enthusiast or organization with the capital to invest in pro-level graphics cards and specially-designed coinmining rigs—therein lies the opportunity to make a tidy profit (after equipment and electricity costs). Now imagine if there was a way to mine crypto without needing to buy equipment or pay the electricity bill…
Cybercriminals came to realize just this—capitalizing by stealing computer resources from website visitors and from unsecured computers around the world on our globally connected internet. And thus—Malicious Coinmining is born.
A Brief History of Malicious Cryptocurrency Mining
In 2017 and 2018, we’ve witnessed this major new trend, as cybercriminals across the world have increased efforts and focus on hijacking unsecured computers, servers, and the browsers of web surfers to fund their crypto wallets. Crypto abuses have rapidly become one of—if not THE–attack method of choice for bad actors and cybercriminals. Not only is it easy to set up coinmining on a server once the attacker gains privileged access, it also provides an added benefit of protection through anonymity (one of the many benefits inherent to cryptocurrency). This makes cryptocurrency ideal for illicit activities. One study of the Bitcoin network found illicit behavior with as many as 24 million (25%) of all users—and a staggering 36 million transactions, which amounts to 44% of all transactions. But Bitcoin isn’t even the most popular of cryptocurrencies for illegal mining activities. In a report by Bloomberg, “Privacy coins such as monero, designed to avoid tracking, have climbed faster over the past two months as law enforcers adopt software tools to monitor people using Bitcoin.” Other cryptocurrencies such as Monero, Ethereum, and Zcash are actually more prevalent in the underground crypto world. In fact, due to this perfect storm of technological benefits and exploits, cash-starved nation-states trying to circumvent sanctions are increasingly turning to this activity to generate digital currency, which can then be exchanged for hard currency.
We can also note that this represents a significant shift away from ransomware as the most common cyber attack—the practice of breaking into computers and networks to encrypt system files, thereby holding data ransom until a payment is made to the attacker. While malicious coinmining efforts may only rake in a fraction of the profits compared to a ransomware campaign, they require significantly less work, fewer moving parts/processes, and require no interaction with victims. Once a vulnerable web server, website, router, or other piece of hardware has been found and compromised—a hacker can install their coinmining code, configure it to deliver to their crypto wallet, and start getting paid immediately.
To to be clear, this doesn’t mean that ransomware is any less of a threat. It is alive and well, expected to cost some $11.5 Billion USD per year by 2019. But this does show an evolution in cybercrime tactics. It should also serve as a reminder to remain current and knowledgeable about vulnerabilities, exploits, and trends—as well as to actively secure resources and actively monitor for anomalous behavior.
What’s the Risk For the Average User?
What does all of this mean for the average person or employee? Well, even if you’re not participating in buying/selling crypto—or “mining” it—you may still be at risk. In fact, aware of it or not, you may be actively mining cryptocurrency as you go about your daily routine, surfing the internet or reading that news article that came up in your business alerts feed.
How?… One of the most common and widespread forms of malicious Cryptocurrency Mining—browser hijacking. Once a hacker has compromised a website or server’s security—they can easily install a small snippet of javascript (configured to send the mining proceeds to their own anonymous crypto wallet) which will perform the malicious mining on any visitor’s browser sessions for the duration they visit the site.
At this point, the hacker can basically set it and forget it. If the website or computer’s administrator doesn’t actively monitor activity—and web visitor’s aren’t diligent—the mining script can run unimpeded for an indefinite period of time, accruing profit for the hacker without being found.
At least it requires a talented hacker with advanced knowledge and tools at their disposal to perform these attacks, right? Not quite. Thanks to open-source sharing repositories and other advancements—mining scripts and other exploits are easier than ever to execute. Probably the most notable coinmining code comes from CoinHive—a cryptomining service that uses javascript implanted on a website to mine bits of Monero cryptocurrency. CoinHive quickly vaulted to the top of the list earlier this year as the most used malicious crypto technology. In fact, in an article from March 2018, Krebs on Security covered that nearly 32,000 distinct websites (legitimate or infected) were running the CoinHive mining script. Today, checking with publicWWW.com, we find that number is down to around 15,000. Thanks to increased awareness by the general public, code patches that have closed some security gaps, and growing sophistication of cyber criminals—the number of CoinHive instances continues to shrink, but that doesn’t mean that there are any fewer malmining campaigns.
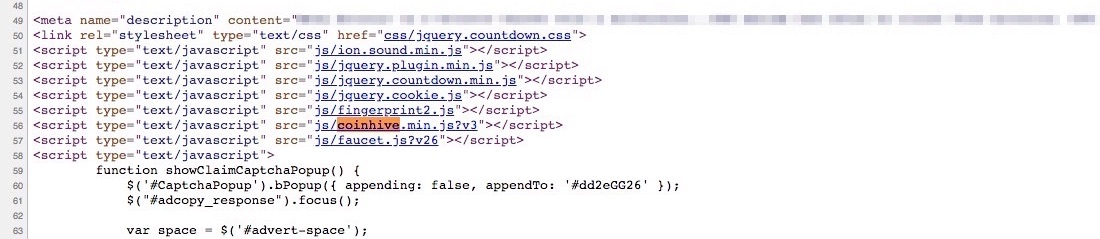
Example of CoinHive Javascript on page source code
While not as lucrative as other malicious cryptocurrency mining efforts such as compromising web servers, browser hijacking still represents an inherent security vulnerability, stealing computer resources, electricity, and putting unnecessary strain on your devices thereby shortening their lifespan. All while funding cybercriminals or potentially illicit activity behind a veil of anonymity.
Additional Thoughts
The best form of defense from malicious cryptocurrency in this case—is knowledge.
Stay up to date with the latest vulnerabilities and trends, perform an audit of your security infrastructure, and continuously educate yourself and your teams (through security awareness training) about attack vectors and mitigations options). If you’re in charge of IT or security within your organization, you should have mitigation and recovery processes in place so that you’re prepared—not only to protect your networks/devices from new threats, but so that you have an action plan in the event of a catastrophic failure or breach. Planning for worst-case scenarios will help harden your security, systems, and reduce your expenses and time to recovery.
Otherwise, the #1 way to improve network security for yourself and your organization is to ensure that you have the protection of a premium web filtering solution that is actively managed for coverage, accuracy, and identification of malicious threats. Threats and malicious websites are in a state of constant flux—therefore it is critical that your web filtering solution continuously analyze the ActiveWeb and remain up to date on new and existing threats.
Stay tuned for our next installments on cryptocurrency, where we’ll explore best practices for identifying and preventing unwanted coinmining, criminal cryptocurrency trends, and more.





