Tactics, Techniques and Procedures: Attackers are Targeting Vulnerable and Misconfigured WordPress Deployments to Serve Qakbot and other Malware.
A new strain of Qakbot, or Qbot, is making headlines and claiming victims by distributing the malware through compromised WordPress sites. From personal blogs, to small businesses, to global Fortune 500s, WordPress currently powers nearly 38% of all websites. Almost 60% of WordPress installations are running outdated versions of the software which creates a broad attack surface rife with vulnerabilities. Between the deep market penetration and thousands of known vulnerabilities to the core software, plugins and themes, WordPress sites are a prime target for Malicious Cyber Actors (MCAs) to attack and launch malware infection campaigns — like we’re seeing with Qakbot.
Qakbot
Qakbot is a banking Trojan designed to steal Personally Identifiable Information (PII). The overall goal for the MCA is to collect browsing activity and steal bank account credentials and other financial information. Qakbot is designed to be highly evasive and self-propagating which makes it difficult to stop.
Qakbot attacks are launched through phishing email campaigns which lure victims to click on an attachment that appears as a legitimate document — bills, invoices, etc. To open the file, a user must enable macro commands which then enables the attachment to run malicious macros and infect the machine. Once the machine is infected, Qakbot copies itself onto the network and onto removable drives, mutating itself while moving laterally.
The Escalating Trend
According to the 2020 CrowdStrike Global Threat Report, MCAs are disabling endpoint protection and compromising WordPress sites to steal data and credentials. CrowdStrike traces this trend back to Q3 2019 when it began detecting increasing numbers of compromised WordPress instances to distribute malware like Qakbot, Emotet, and REvil. From the zvelo perspective, our cybersecurity team is detecting Qakbot instances that are specific to WordPress sites. Below is an example showing some of the compromised URLs that our cybersecurity team has recently detected.
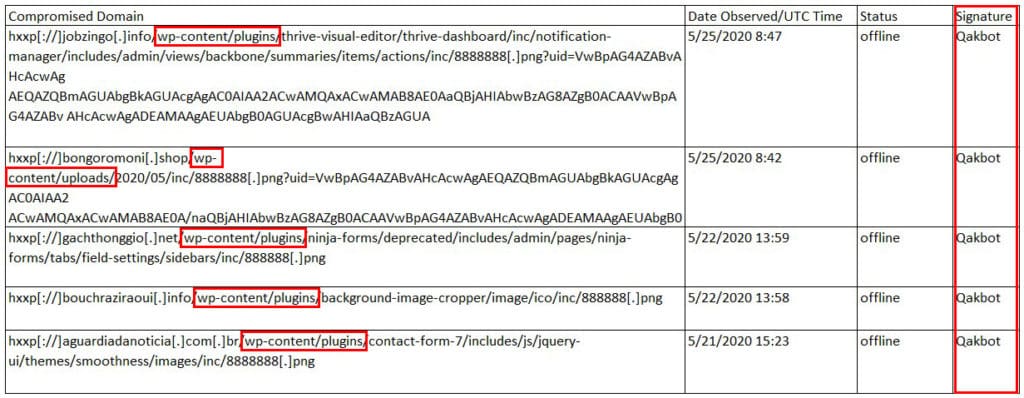
Based on the data that has been collected and publicly shared over the last few quarters, we do see a trend with a resurgence of Qakbot which is typical for most malware types whenever they are periodically updated with more sophisticated infection and evasion techniques. There are other plenty of other examples of malware being distributed through compromised WordPress sites, but this post highlights Qakbot as an example because it has recently resurfaced as a trending threat.
WordPress Vulnerabilities Are an Easy Target
WordPress is not the only attack vector used by the MCAs however, it is a popular choice because it is the most prevalent Content Management System (CMS) on the market, and is notorious for having thousands of vulnerabilities for the attackers to prey on.
In a 2019 threat report, a leading security platform noted an increase in the number of plugins affected by the misuse of WordPress’ update_option() function and other broken-by-design vulnerabilities. When developers don’t configure settings and permission flows correctly, MCAs are able to gain admin access and compromise a site. While the list of vulnerabilities is always extensive, it’s also incredibly dynamic because the list covers the WordPress core software, tens of thousands of plugins and WordPress themes.
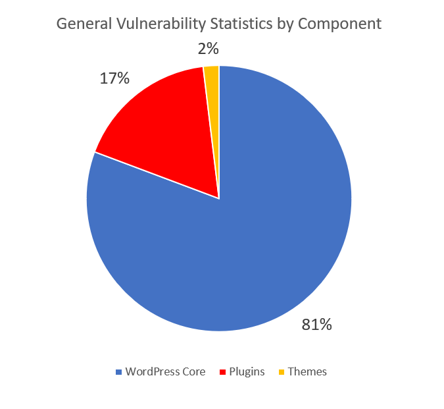
The specific statistics and details around known vulnerabilities all vary depending on the source, but for the purpose of sharing a sample set of data, we’ll use some numbers from the WPScan Vulnerability Database. WPScan currently has 21,642 vulnerabilities cataloged — 4,045 of those are unique. (Note for clarification: One vulnerability can affect multiple WordPress versions, Plugins and/or Themes. If the same vulnerability affects two different WordPress versions, we would class this as two vulnerabilities or one unique vulnerability.) The chart below shows the breakdown of vulnerabilities by component based on their database.
The data looked at another way, shows a breakdown of the known vulnerabilities by type.
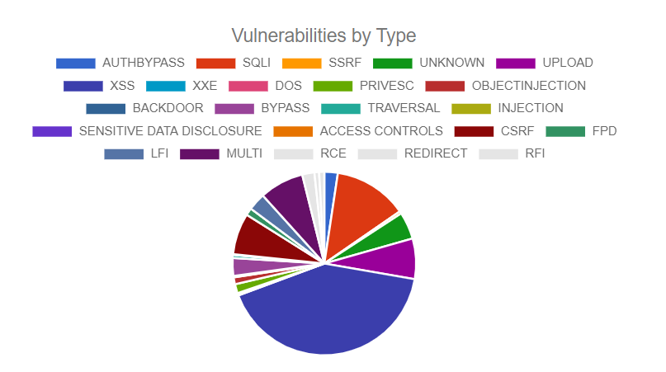
The top 4 vulnerabilities based on the chart are as follows:
- Cross-Site Scripting (XXS). XXS is a web application security vulnerability enabling attackers to inject client-side scripts into web pages viewed by other users.
- SQL Injector (SQLi). SQLi is a code injection technique targeting data-driven applications which enable an attacker to control and manipulate the database.
- Cross-Site Request Forgery (CSRF). CSRF is a web security vulnerability that enables the attacker to trick users into executing an unwanted action within an application for which they are properly authenticated.
- Upload Vulnerability (UPLOAD). The Upload vulnerability has to do with how files are uploaded to WordPress sites. While files can be uploaded directly via the local file or via remotely via URL submission, there are vulnerabilities in both available methods. The image below is an example showing one of the detected malware instances via the WordPress uploads.

Conclusions and Recommendations
Wherever there are vulnerabilities, the MCAs are certain to find them and launch targeted malware campaigns against the easiest targets. While WordPress happens to be a fairly easy target, it’s important to note that the majority of successful attacks are typically the result of human error. Human error is by far the largest contributing factor to successful attack whether it be due to misconfigurations, ignored security updates, weak user authentication policies, etc.
To reduce the risk of being attacked and having your WordPress site compromised to serve Qakbot or any other malware, here are a few recommendations from the zvelo Cybersecurity team.
- Update WordPress software, plugins and themes regularly. Updates will typically fix known vulnerabilities which is key to preventing attacks.
- Implement Multi-Factor Authentication (MFA). Even 2-Factor Authentication (2FA) is better than a single password, but the more difficult you make it for an attacker, they more likely they are to move on to an easier target.
- Backup your site regularly. Better yet, automate the site backups. If you discover your site has been compromised, you can revert back to the most recent ‘clean’ copy.
- If your organization does not have an in-house security team, use a third-party service to install and manage security tools like firewalls, virus and malware scans, etc.
- Protect your wp-config.php. This is the most valuable file on your site. One simple step you can take to protect it is to move it one step above your WordPress root directory, which will keep it hidden from attackers without negatively affecting the actual site.





