Estimated Reading Time: 5 minutes
The cybersecurity space has witnessed a rapid transition away from malware and ransomware as the primary threats facing users and businesses in recent years. Cyber criminals have looked to low-effort malicious cryptocurrency mining for generating income without ever having to deal with victims in order to receive payment. But the most dangerous security threat by far is phishing—particularly targeted phishing attacks such as spear phishing and whaling.
Today, it is expected that 1 in every 100 emails received by an enterprise is a phishing attack. In a report from Wombat Security, 76% of organizations say they experienced a phishing attack in 2017, but this figure is just what IT and security officials are aware of.
With a 65% growth in phishing attacks over the course 2017, businesses and organizations have bolstered IT and training efforts to tackle the phishing threat with security awareness for all employees. This has led to a rise in penetration testing and phishing simulation tools in order to continuously train and improve cyber defenses against human error. It only requires one lapse in awareness—one password entered on an insecure page or one downloaded Microsoft Word document—to breach defenses and hand over access to sensitive information.
And so cybersecurity experts have looked to personnel security training and awareness, as well as machine learning to help patch the security gap.
Where Do Phishing Attacks Come From? What Are The Top Industries and Brands Targeted?
In a forensic report from Comodo, it was found that the United States ranked number 1 for both hosted phishing sites at 65% of the total, as well as country of origin (36%). So while the majority of botnets, C&C servers, ransomware campaigns, and other malicious behavior tend to come from elsewhere in the world—the United States is a haven for phishing campaigns and hosting.
As far as targeted industries and brands go, digital commerce, payment systems, and the financial sector are the aim of over 50% of known phishing attacks. Targeting these industries and businesses allow cyber criminals to tap directly into personal information and credentials related to their victim’s bank accounts and assets. It’s no surprise that these industries continue to be the primary focus for phishing attacks. It’s also no surprise that fake invoice emails/messages are the #1 phishing lure.
Tech companies and cloud providers—as a group—come in second with SaaS, Webmail, and cloud storage companies specifically. From a value perspective, these services require constant authentication for access and tend to store intellectual property and valuable proprietary information for businesses. If an attacker can breach these systems—they may be able to achieve persistence on an organization’s systems or just exfiltrate information that will return top dollar on the black market.
The Top brands targeted by phishing include Microsoft, Google, Facebook, Apple, PayPal, Adobe, Dropbox, FedEx, Wells Fargo, and the list goes on.
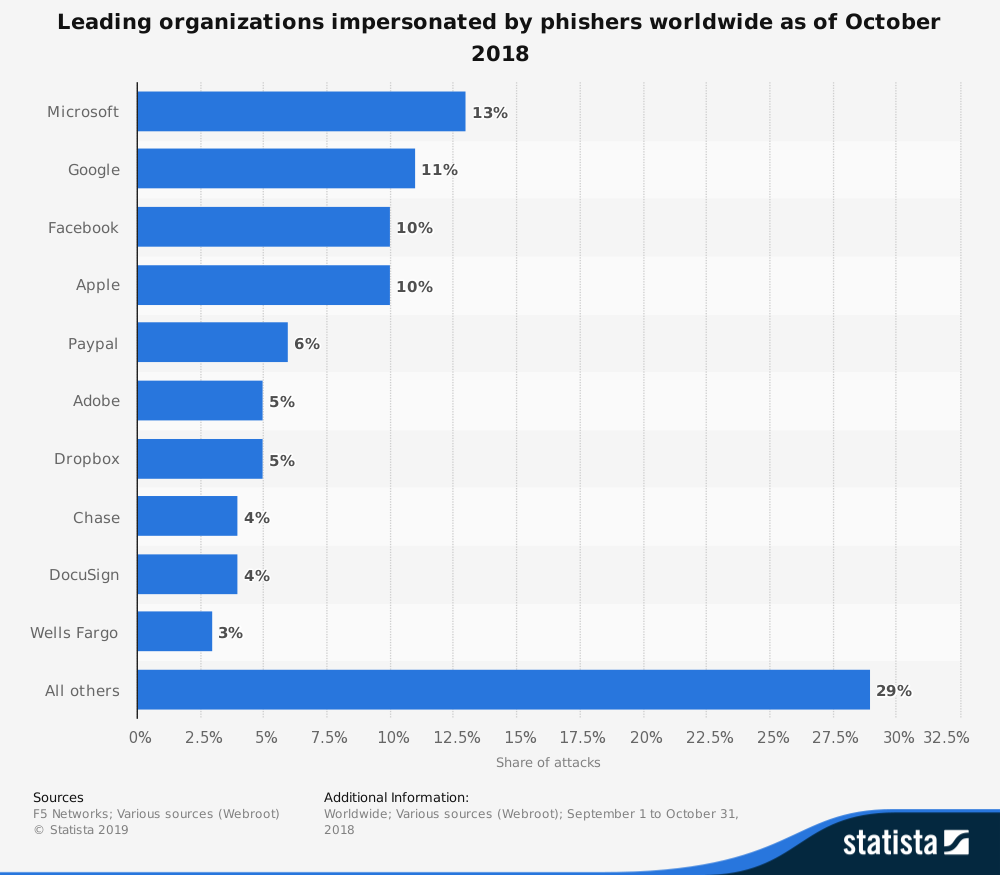
Source: Statista.com
Delivery Methods and What to Be Aware Of
As mentioned earlier, phishing generally begins with an email but can also be initiated via a phone call (Vishing), text message (SMiShing), or other means. Tactics like targeted phishing, spear phishing, and whaling are particularly effective—leveraging social engineering to prey on an individual’s or businesses inherent interests. They also typically involve a significant amount of research on a particular target or business. In many cases, the attackers will manufacturer a situation or state of urgency that members of an organization will look to resolve—often playing right into the attack. And by the time any intrusion or breach is discovered, it’s often far too late, leaving significant brand damage, a large bill for remediation efforts, and in many cases private customer data.
Phishing attacks are also increasingly difficult to spot. Using a variety of tactics including IDNs, homographs, URL shorteners, and typo-squatting to deceive their users. In several of our recent blog articles we’ve explored the significant security challenges that phishing presents, as well as ways to improve awareness and resiliency against attacks. Understanding the complete anatomy of a full path URL including the basics of how protocol, top level domains, subdomains, and parameters work is often the best way to improve general users defenses against phishing.
- Phishing Poised as Most Significant Security Challenge in 2019
- What is an IDN Homograph Attack?
- 9 Tips to Improve Mobile Security Protection Against Phishing
Here are just a few examples of phishing campaigns in previous years:
- 2018 Stripe Phishing Campaign
- 2018 Mobile Phishing Scams Target Apple IDs
- 2018 Phishing Website Examples Detected by zvelo
Looking To AI-Based Solutions For “Zero-Minute” Detection and Prevention
Detecting and protecting against phishing attacks comes with a number of challenges. Phishing URLs and campaigns have “short shelf lives” and operate on a timescale that’s doesn’t allow for human verification or intervention processes. So cybersecurity companies, like zvelo look to advanced machine learning and other AI-based methods for automatically detecting phishing sites as they come online.
In the early years of cybersecurity, detecting and preventing phishing has relied on a “sacrificial lamb” approach. This means that the first (or early group) of victims are overlooked. They are compromised and there’s no way to stop that—but once that has happened the site/URL can be properly verified and flagged as phishing, thereby protecting any future victims. But in recent years, with advancements in AI and ML-based techniques, computers armed with sophisticated models can continuously monitor and scan conspicuous websites for signals of phishing.
- The Secret Behind zvelo’s Leading Website Categorization Technology
- Applying Machine Learning to Web Content Categorization
Some such signals that models look for include:
- Analyzing the URL to see if it contains high profile brand names that aren’t the official domains
- HTML content includes high profile company names with an obscure top-level domain
- Analyzing for scripts and frameworks associated with known phishing tools
- Looking for punycode or IDN homographs that may be used to deceive users
- Logos and branding on the page do not match domains
- Resulting sites include large amounts of ads or banners
- And many more..
For more, check out our blog “How to Spot and Protect Against Phishing Websites” or “9 Tips to Improve Your Organization’s Security Against Mobile Phishing Attacks.”
What’s Next For Phishing Detection on the Horizon
Artificial Intelligence and ML models will change phishing detection in 2019, improving it for the better. As models become more sophisticated and settle into more mainstream cybersecurity solutions, these systems will become more accurate in identifying phishing campaigns targeting high-profile brands and industries, as well as those phishing sites associated with known toolkits and frameworks.
It will become increasingly important that social platforms, email providers, and other services incorporate systems and functionality to identify phishing threats as attackers look to develop more sophisticated methods to evade detection. The key will be early identification—stopping phishing sites and infrastructure from the majority of web users and routing the problem.
Stay tuned for new phishing announcements from zvelo in 2019. If you’re concerned about phishing and malicious threats online—learn more about our phishing and malicious detection capabilities or subscribe to our newsletter and security updates for the latest news.





