Over the years, cybercriminals have deployed increasingly sophisticated scams to deceive users of payment processing systems—particularly small and medium sized business owners—into compromising their accounts by unknowingly divulging account credentials. These attacks are nothing new.
In 2018, the tactics haven’t changed much, but the level of sophistication has continued to rise. Cybercriminals understand that a little extra time and energy spent on copy and creative (images/design) produces significantly better results.
Here’s an example of a recent phishing campaign from Fall 2018 targeting Stripe users:
2018 Stripe Phishing Campaign
The initial point of contact is a generalized phishing email that identifies an outstanding account balance and a need for the user to verify their account and banking information. Knowing that many users, particularly on mobile devices, will take the easiest route to access their account—the perpetrators provide a “convenient” hyperlink that appears to point to https://dashboard.stripe.com/account/payouts.
The actual hyperlink destination is not owned by Stripe at all and forwards the user to a site located at a domain name that is produced by a domain generated algorithm (DGA).
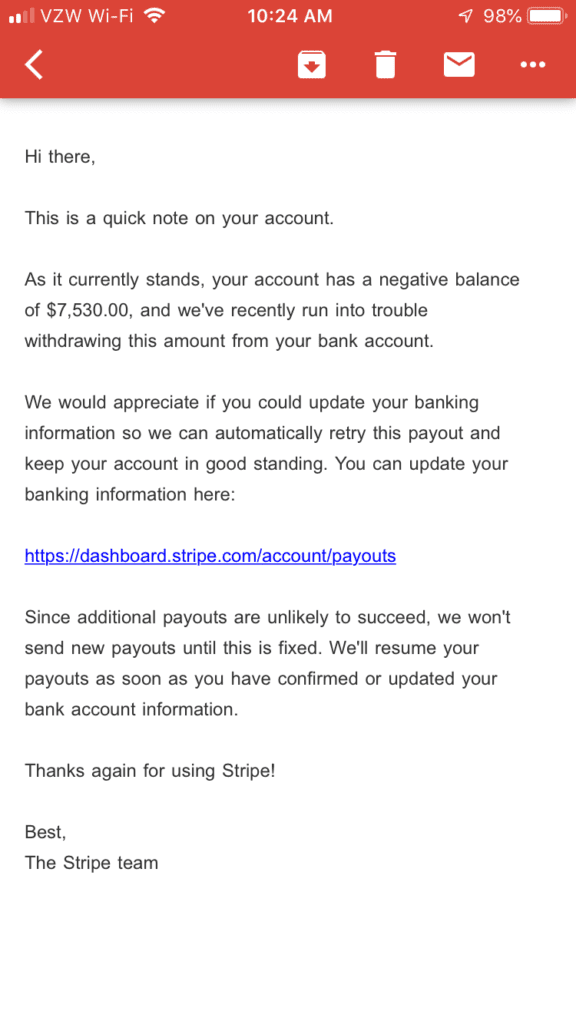
Stripe Phishing Scam – Mobile Email in Gmail App (iOS)
The email is well-written, to the point, and simply formatted—sent in plain text. This mimics a popular minimalistic style employed by many companies to handle transactional/account emails and notifications. This is a case where simplicity perfectly imitates professionalism and legitimacy—making work easier for bad actors.
If the user clicks on the hyperlink provided in the email—they are taken to a landing page designed to capture any username and password entered. The landing page also matches the minimal styling and simplicity of the original—and is designed to look exactly (nearly) like the legitimate Stripe login screen. The only differentiating factor is the boldness of the font for the “Welcome back!” greeting. See the image below…
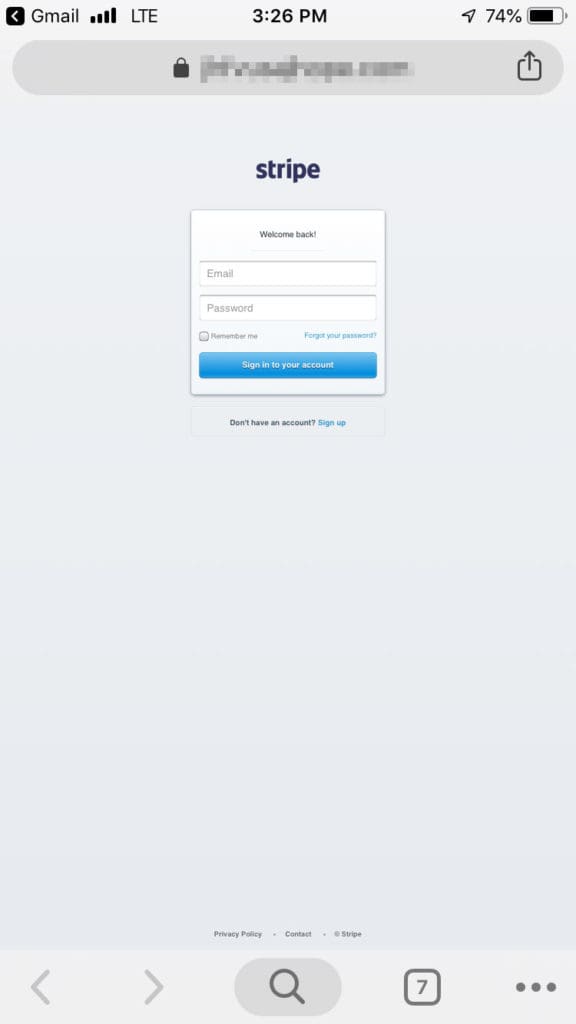
Stripe Phishing Campaign Scam – Landing Page on Mobile
Without inspecting and looking at the page’s source code—can you guess which of these two logins is the phishing scam?
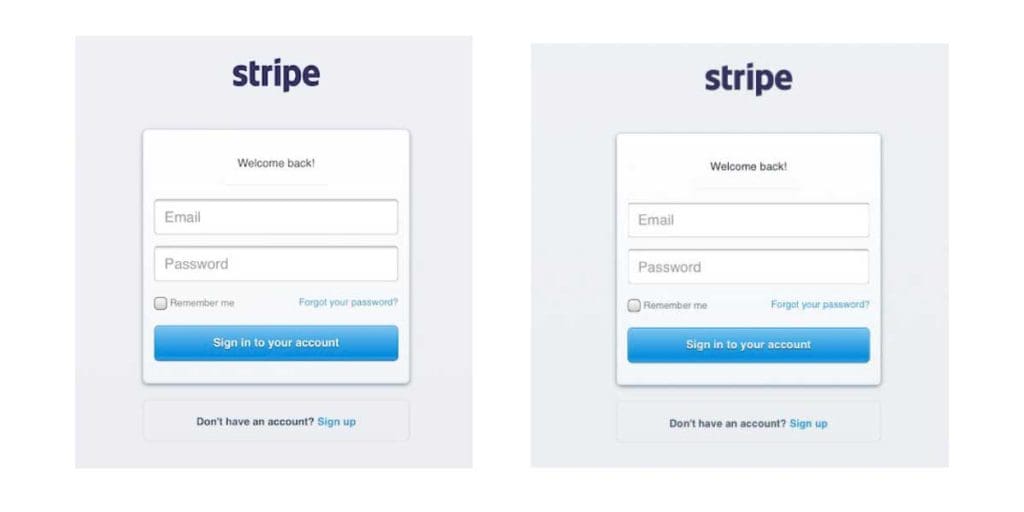
2018 Stripe Phishing Scam – Mobile Login Challenge
If you think you’re up to the challenge—take the poll at the bottom left of your desktop browser window.
We’ll revisit this blog and show the poll results in a few weeks!
This example hopefully reinforces the importance of always verifying the URL of the page—especially before entering sensitive account credentials, credit card information, or other personal information.
Identifying Phishing Emails and Links
As we continue along towards the end of 2018 and the holiday season—we should all be wary and expect to see an increase in a variety of scams. Again, here are some tips a quick reminder for protecting yourself online:
- Always scrutinize emails from unknown sources
- Check the true destination of a hyperlink before you click on it
- Double-check the Full Path URL to make sure you are at the proper (legitimate) destination
- ACTUALLY… If you receive an unsolicited notification—don’t use the hyperlink at all. Take the safe route and go directly to your account from a trusted device and network
- Ensure traffic is encrypted (padlock in browser) before entering credentials
- Verify the safety and status of the page using the zveloLIVE tool at: https://tools.zvelo.com
One of the best ways we can all help contribute a safer internet is through crowd-sourced identification and protections. By reporting malicious sites like phishing, you can help prevent cybercriminals from scamming and victimizing other users. zvelo leverages a crowd-sourced identification model to provide award-winning identification, coverage, and accuracy of malicious sites across the ActiveWeb.
To learn more about our ActiveWeb categorization strategy—check out our blog: Secret to the Market’s Most Accurate and Comprehensive Web Categorization Service.
Malicious Site Shelf Life and Reporting Scams
As most malicious campaigns and sources—phishing landing pages and campaigns may have short “shelf lives”. The example outlined above was only “active” for a short period—and has already been taken down or relocated. Cybercriminals do this to avoid detection and maximize resources. Since many of these phishing campaigns are targeted at SMBs and sole proprietor’s who are quick to resolve account problems—cybercriminals can count on the majority of successful phishes to occur in the first 24 to 48 hours.
If you believe you’ve found a phishing or fraudulent page as a result of a targeted phishing email (or otherwise)—please report the link. Here are a couple of the primary :
- Stripe: https://support.stripe.com/questions/suspicious-email-from-someone-claiming-to-be-stripe
- PayPal: Forward the suspicious email or website information to [email protected]
- Shopify: https://help.shopify.com/en/manual/your-account/account-security/phishing
Malicious Website Detection Threat Protection For Your Users and Networks
With over a decade of experience in identifying malicious sources and maintaining website categorizations for hundreds of millions of users—zvelo understands the challenges of keeping up with the “short shelf lives” of malicious websites. To tackle this, zvelo’s Malicious Detection systems utilize a number of processes and methodologies including crowd-sourced identification and a “malicious revisitation” process—whereby our systems revisit and reanalyze known malicious sources on a regular basis. URL categorization and safety-status updates are distributed in real-time to zveloDB™ databases for partners worldwide.
Learn more about zvelo’s Cyber Threat Intelligence capabilities and the zveloDB URL Database for OEM partners.





