Over the last decade, Domain Generation Algorithms (DGAs) have become a popular tool for threat actors to deliver malware as it has become a difficult technique for defenders to counter attacks. As these DGAs become more sophisticated and increasingly difficult to detect, zvelo’s Cyber Threat Intelligence Team is recommending heightened awareness, as they anticipate this to be a prominent attack method behind what is sure to be a skyrocketing volume of attacks as the US heads into a Presidential election cycle.
What are Domain Generation Algorithms (DGAs)?
Traditionally, malware used to have hard-coded domain names or IP addresses to connect directly with the Command and Control (C&C or C2) server. In contrast, DGAs use algorithms to periodically generate a large number of domain names which function as rendezvous points for malware command and control servers (MITRE ATT&CK T1568.002). Because the attacker only needs to register one of the thousands of domains the DGA produces to provide the C2 service, all the other domains serve as a distraction to flood the DNS stream with requests for DGA domains — making it easy for the attackers to hide and protect the C&C server which will be used to carry out the attack.
Types of DGAs
As always, threat actors continue to increase their level of sophistication to stay one step ahead of being detected. The desire to evade detection has led attackers to develop a different variety of DGAs, several of which we highlight below.
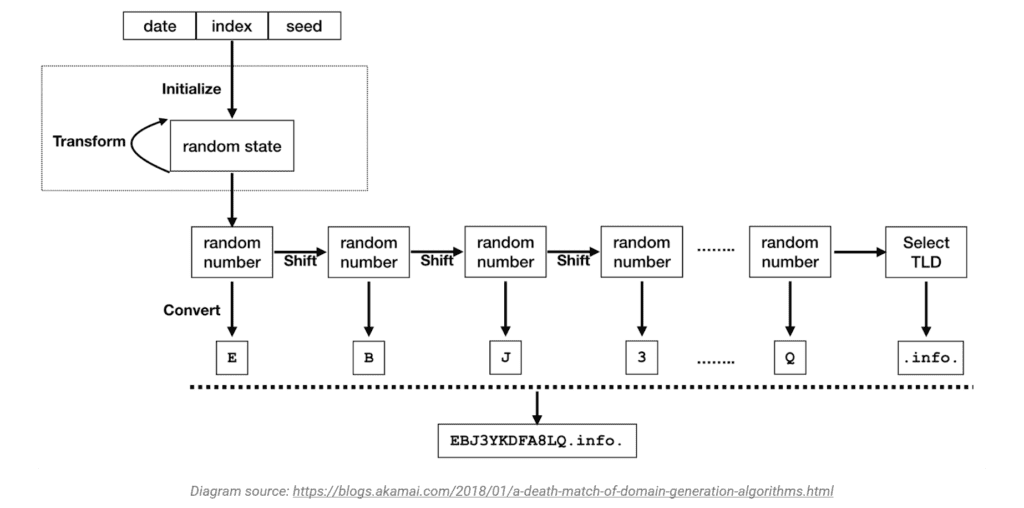
Pseudo-Random Generator (PRNG). The PRNG is the most common and general methodology for a DGA. The PRNG uses a deterministic random seed generator to create domain sequences which are predictable for both the attacker, and the malware. Frequently, PRNGs will use system date and time as the seed.
Character-Based DGAs. This type is the most simple and uses a random seed to select the alphabet or numbers to generate domain names. As these are the most primitive, they are also the easiest to detect. The image below represents what the character-based DGAs look like.
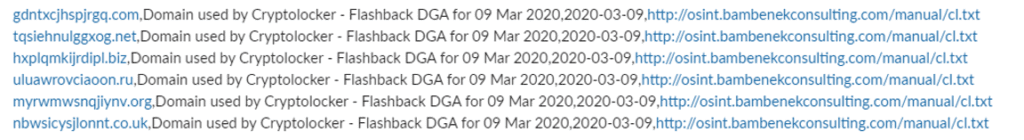
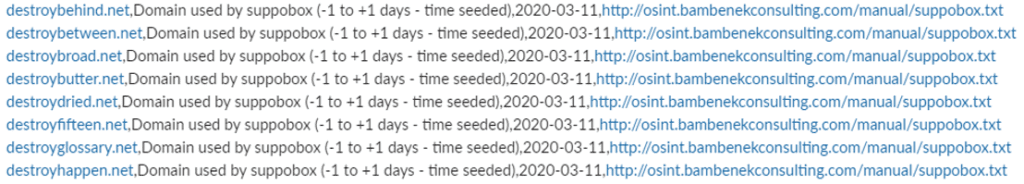
Dictionary-Based DGAs. This type uses dictionary based words and randomly combines them to generate domains with a random, non-human readable look — meaning, these domains are more challenging for AI/ML systems to detect as they may closely resemble legitimate domains. For example, the image below shows a sample of Dictionary-Based DGAs, used by the malware family Suppobox.
High-Collision DGAs. This type has strong collisions with other DGAs, as well as legitimate domain names. The high-collision DGA generates thousands of possible random domains which present as a core of 6-15 characters paired with common Top Level Domains (TLDs) like .net, .org, .info, etc. The structure of these DGAs increases the likelihood that they will collide with legitimate domains.
Malware Attack Prevention
DGAs fuel malware attacks, so the best defense is early and ongoing detection. From the threat intelligence and malicious detection perspective, ferreting out the DGAs is a continuous process which leverages advanced AI and Machine Learning techniques to train sophisticated algorithms that can detect patterns of DGA creation. However, as soon these patterns can be detected, the threat actors get back to work and retool their own algorithms to once again, evade detection.
As we approach the end of the summer, zvelo’s Cyber Threat Intelligence Team anticipates a new cycle of DGAs to launch a multitude of malware campaigns. And, expectedly, this will also escalate as the US enters into a potentially contentious election cycle. Cybersecurity always requires that users possess a heightened level of awareness. To that end, below are a few tips which can alert users to potential DGA-fueled malware attacks.
Know What to Look For
- Domains that appear as a random string of characters that do not make sense, or what appears to be a date and time.
- Suspicious links which redirect to legitimate sites like google. C2 servers may often require specific headers or requests to communicate a malicious payload. When those specific requests are not present, a user will be redirected to a site like google.
What Can Users Do?
- Report suspicious domains to your security team or IT department.
- Don’t open unexpected attachments, especially those from unknown sources.
- Don’t click on links from unexpected or unknown sources.
- Don’t enable macros on attached documents without confirming that you can do so safely from the sender and your IT department.
- Run security software that can help prevent malware attacks.





