A lot has been written recently about the impact that Generative AI will have on phishing. The premise is that the availability of Generative AI will allow malicious actors to create higher quality phishing emails with disastrous increases in successful phishing attacks. It is true — it will be easier for realistic looking emails, with fewer grammatical errors, to be produced by a higher percentage of phishers. While the integration of AI into phishing efforts suggests a grim outlook, it’s crucial to recognize that the ability to create convincing phishing emails isn’t solely the domain of advanced AI. Determined cybercriminals have always found ways to deceive their targets. However, this technological evolution prompts a vital question: Are phishing training programs adequately preparing users to recognize and fend off phishing attacks?
Pitfalls of Traditional Phishing Awareness Training
Phishing awareness training is a cornerstone of cybersecurity efforts, yet it often falls short due to an over-reliance on identifying phishing attempts based on outdated red flags. Traditional training methods have taught users to spot phishing emails by looking for poor grammar, the use of unsecured HTTP connections, unfamiliar email addresses, or unexpected email attachments. While these indicators can, and frequently do, point to phishing attempts, they are far from foolproof and create a very brittle approach. Cybercriminals are now using more sophisticated tactics, leveraging Generative AI to create emails that bypass these simple checks. This evolution underscores the need for a shift in how we approach phishing awareness training.
A Durable Approach to Phishing Awareness Training
To counteract the dynamic phishing threat landscape, we must adopt a more nuanced and technical approach to training. Users should be educated on the more subtle signs of phishing attempts, such as scrutinizing the actual sender of an email, rather than relying on the displayed “friendly name,” and understanding where a hyperlink really leads before clicking on it. This level of vigilance is crucial because these are elements that phishers find difficult to convincingly fake.
The internet is a complex, technical domain, and by not fully educating users on these nuances, we are doing them a disservice. Empowering users with this knowledge enables them to navigate the internet more safely and confidently.
SSL Certificates: One Key to Identifying Phishing Sites
One of the simplest yet most effective ways to bolster phishing awareness training is to educate users about SSL certificates. SSL certificates are crucial to verifying the authenticity of websites, and ensure that users are interacting with genuine entities. By understanding the different levels of SSL certification — Domain Level Validation, Organization Validation, and Extended Validation — users can make more informed decisions about the trustworthiness of websites.
Domain Level Validation SSL Certification. Domain Level Validation (DLV) SSL Certification represents the most basic and cost-effective level of validation available. Its primary appeal lies in its simplicity and speed, facilitating a swift transition from HTTP to HTTPS by merely requiring proof of domain control by an organization. However, in the current cybersecurity climate, marked by a significant increase in Business Email Compromise (BEC) and email account takeover attacks, this level of certification no longer serves as a reliable indicator of a website’s legitimacy.
Organization Validation SSL Certification. Organization Validation (OV) SSL Certificates involve a more rigorous manual vetting process that verifies critical details such as the organization’s name and address. Although obtaining an OV certificate is neither the quickest nor the least expensive option, the thoroughness of the vetting process renders these certificates significantly more reliable than their Domain Level counterparts. As a result, OV certificates are considered a more trustworthy indicator of a website’s authenticity, offering a stronger assurance against phishing risks.
Extended Validation SSL Certification. Extended validation SSL certifications are the most stringent, and by far the most reliable indicator of a non-phishing site. Extended validation will involve a complete background check on the organization to verify its existence, that it is legally registered as a business, and other key details about the organization. The drawback for most organizations is that this level of validation can be the slowest and most costly, albeit crucial for the most commonly phished brands like financial institutions and e-commerce sites.
Real World Example of a Legitimate Site vs a Phishing Site
Microsoft consistently ranks as a highly targeted brand for phishing attempts. Researchers at zvelo frequently encounter fake login pages designed to mimic Microsoft’s own, with differences that are not immediately apparent without a closer inspection of the technical specifics.
A significant hurdle involves educating users to move past traditional security indicators such as the padlock icon and the HTTPS protocol when determining the legitimacy of a site. In today’s landscape, these markers are no longer sufficient to guarantee a site’s safety. The relative ease with which a Domain Level SSL Certification can be acquired means that many phishing sites now present themselves with a veneer of security.
Complicating matters further, Microsoft, like other sizable entities, utilizes a variety of legitimate subdomains for different login portals, potentially confusing users at first glance. It’s crucial for users to become adept at scrutinizing the technical details of a site’s certificate to confirm its authenticity, rather than relying solely on the URL’s superficial appearance. This skill is essential for navigating the complexities of modern web security and ensuring one’s digital safety.
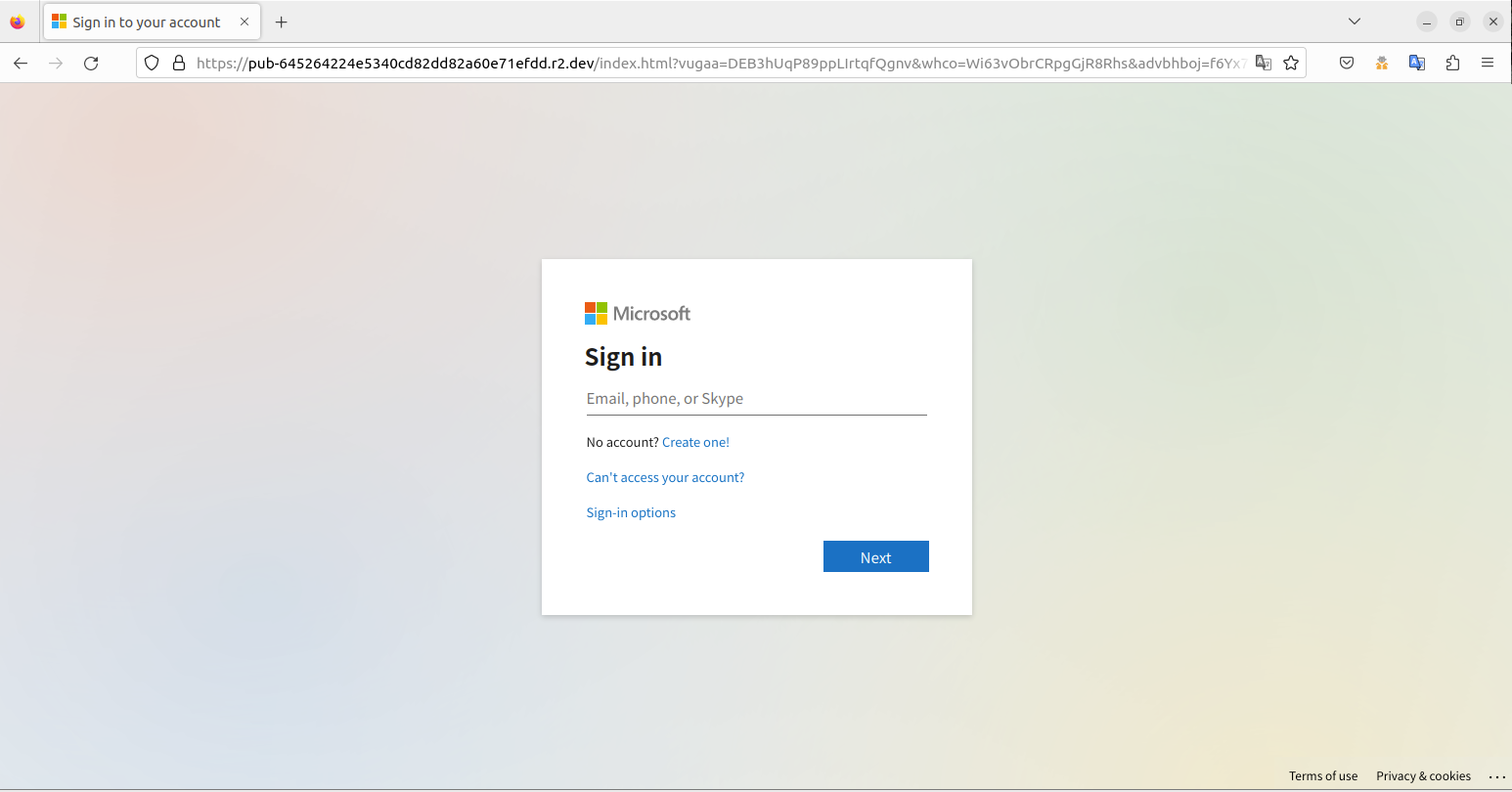
Phishing Login page
Legitimate Login Page
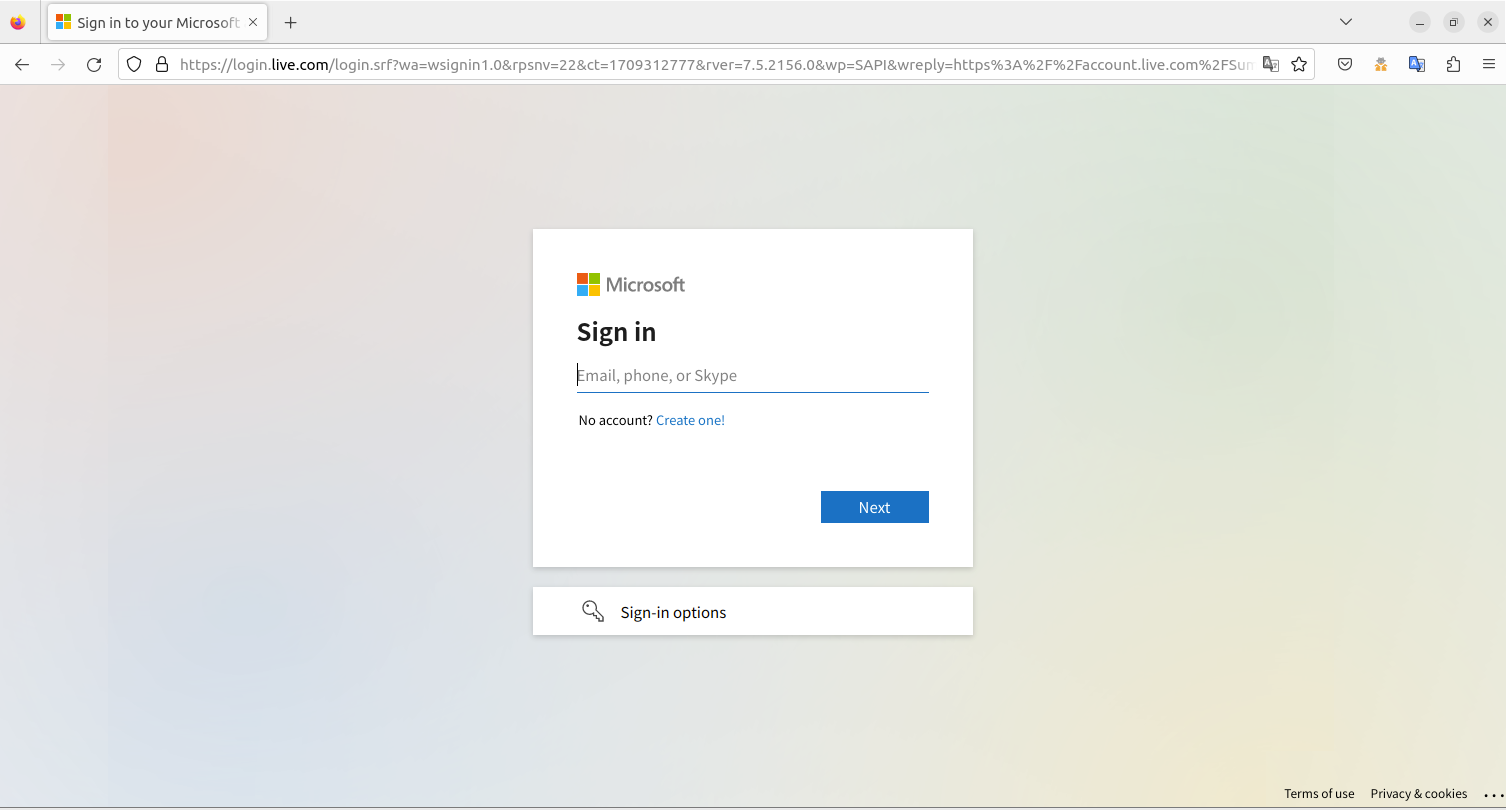
Users should be trained to distinguish between phishing and legitimate sites by scrutinizing their SSL certificates. Users can begin this process by simply clicking on the icon adjacent to the website’s URL address in their browser. Depending on your browser, this might be represented by a padlock icon or something resembling a filtering icon.
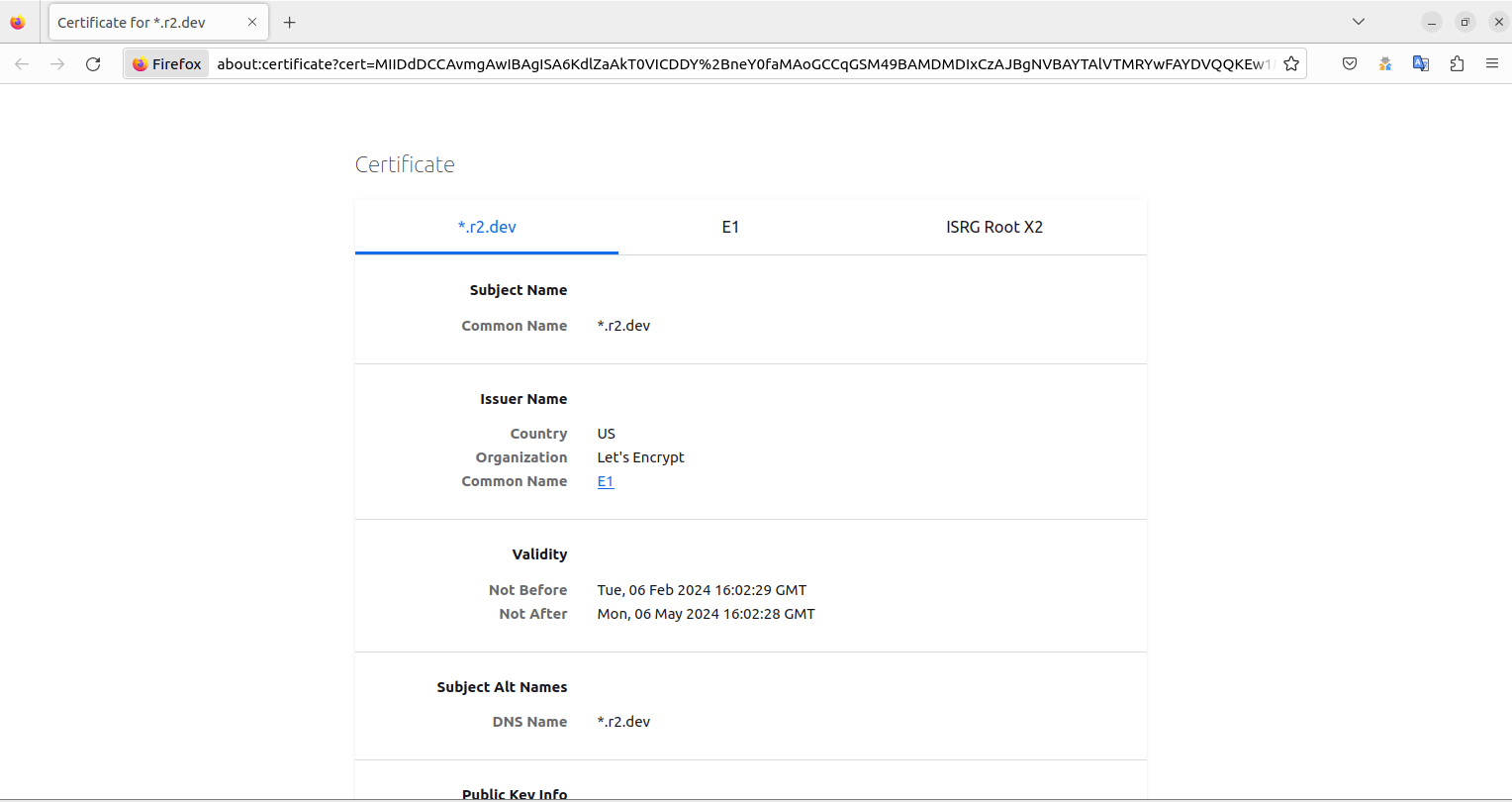
This action unveils the site’s SSL certificate details, allowing for a direct comparison between the credentials of phishing attempts and authentic sites. For instance, the SSL certificate of a phishing site might list ownership under “*.r2.dev” and show it’s secured with the most basic, less secure Domain Level Validation, typically issued by entities like Let’s Encrypt. This immediate verification step can significantly raise a user’s confidence in identifying a site as a phishing attempt rather than a legitimate login page.
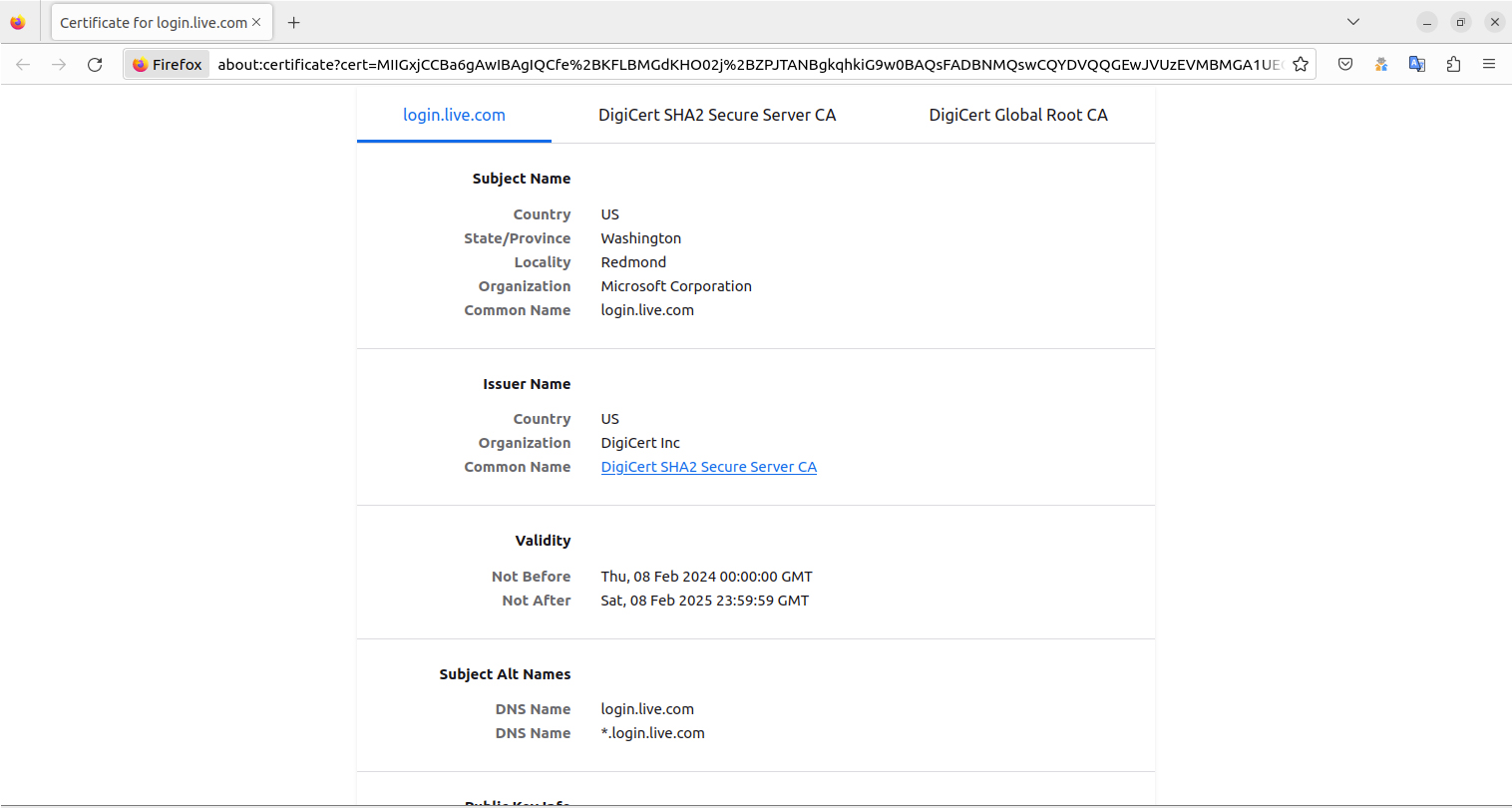
Conversely, examining the SSL certificate of a genuine Microsoft login page offers reassurance through detailed verification. The certificate would disclose Microsoft as the registered domain owner and highlight encryption and authentication secured by DigiCert, renowned for its robust validation measures. This level of detail in SSL certification underscores the critical differences between phishing and legitimate sites, providing users with the tools needed to navigate online spaces safely.
Best Practices for Avoiding Phishing Attempts
While recognizing the importance of technical vigilance, it’s also vital to adopt general best practices for avoiding phishing attempts.
- Don’t click on links in email is often the cardinal rule, but maybe isn’t realistic in a real work environment.
- Encourage the use of password managers to prevent users from inadvertently entering credentials into phishing sites, as these tools will not autofill login forms on unrecognized sites.
- Train users to verify the certificate being presented to make sure they are where they are supposed to be.
- Deploy security solutions that don’t rely on poor grammar as their primary signal to filter email and web traffic to reduce the likelihood of users encountering phishing sites in the first place.
As phishing tactics become more sophisticated, our approaches to awareness training must evolve accordingly. By focusing on the technical aspects of phishing detection and empowering users with the knowledge to scrutinize the emails AND sites they encounter, we can build a more resilient defense against these threats. Ultimately, the goal is to foster an environment where users are not only aware of the dangers of phishing but are also equipped with the tools and knowledge to protect themselves effectively.





