Partner SpotX holds Q&A with zvelo Business Development Vice President, Cordell BaanHofman, on all things ad fraud related.
SpotX recently sat down with Cordell BaanHofman, our VP Business Development here at zvelo to discuss the current state of fraud in the industry, including brand safety challenges and ways combat them. They were curious about how zvelo combines artificial intelligence with human-supervised machine learning methodologies to deliver the most extensive content categorization, malicious site detection, botnet identification and ad fraud prevention data solutions available.
With over 10 years spent in the network security industry, we didn’t disappoint! Here’s the interview:
Q: What does zvelo consider a malicious site? Is there a difference between a malicious site and a site conducting fraud?
A malicious site is one that contains exploits such as viruses, spyware and bots that are downloaded onto a device (PC, laptop, tablet, phone, etc.).
When the web page is visited it performs some type of exploit during the session while the device is connected to the web page.
A fraudulent site is different in that the site is being maintained for the purpose of conducting fraud (phishing, scams, selling fake ads, etc.). The ultimate goal here is usually connected to financial gain. They attempt to do this through selling fake ads or tricking visitors into providing personal information, credit card and other data. In many instances, a fraudulent website also contains links to a malicious website where exploits, viruses, spyware, and bots are then downloaded onto a device.

There are also countless variations on the types of fraud, phishing sites and malicious exploits. For example, in the Ad Tech world, malware can take the form of exploits that are called (downloaded) once the ad unit (a.k.a.creative) fires on the page. The ad unit containing the exploit is delivered to a browser session and is then able to deploy malicious code to a browser or its device.
Additionally, malware takes the form of deployed bots onto a user’s computer that a hacker is able to deploy across ever-increasing numbers of PCs and other devices. These bots form what is called a “botnet” (network of bots) that is controlled by the hacker (called a “command and control” operator). A botnet can lie dormant for extended periods of time and can be put into action in a moment’s notice to perform their ultimate function. This can range from denial of service attacks (DDoS), creating a spam network, or generating fraudulent, Non Human traffic to web pages simulating human traffic and allowing the publisher (in reality, the hacker or their agents) to raise the CPM price for advertising on a page that defrauds the advertiser since the ads are not being viewed by actual humans.
Q: What can publishers do to ensure their inventory remains protected from malware and/or fraud?
There are several “best practices” that can be adopted by publishers. One of the most important is to perform page-level audits on inventory on an hourly, or real-time, basis. This audit should be performed at the page or file level since hackers often can deploy exploits at the page or file level deep within domains…in some cases even on sites of highly trusted brands. Hackers then use phishing and fraud (as well as email, text, tweets and other vectors) to direct visitors to the malicious pages.
It’s important that audits are conducted on an hourly or real-time basis as the shelf-life of new exploits is typically only a few hours. After that, many viruses, spyware, malware, bots will either morph (aka: polymorphic viruses)or self-destruct to avoid their detection. The virus (or a permutation of the virus) will then spread to a new page, traffic will be directed to this new URL for a few hours when the virus will again morph and/or self-destruct and the pattern continues repeating at a massive scale across the entire Web. Hackers use this approach to run virtually undetected by publishers and buyers who rarely, if ever, do any type of inventory audit and, those that do, typically only do so on a monthly or less frequent basis.

Finally, the audit should utilize static scanners (for viruses, spyware and malware), behavioral detectors (for a fraud, phishing and scam detection) and a wide range of other detection techniques to identify exploits and threats across all threat vectors (web, email, etc.).
Q: When manually reviewing a site, are there ways buyers can identify if it’s potentially malicious? Are there any common characteristics?
It is nearly impossible to determine if a website is malicious through a manual/visual inspection. In some cases, an alert visitor might spot a fraudulent site, for example, if you are directed to what appears to be a banking website, but there is some slight type or misspelling or the copyright mark is out of date. However, for malicious sites (malware, viruses, spyware, bots), these are not visible to the human observer. The challenge in detecting malicious websites changes on an hourly basis as the battle rages between “blackhats and whitehats”. Blackhat hackers devise new attacks and exploits that are used until they are detected with enough regularity, or frequency, by whitehats – at which time the blackhats change-up and devise new threats. It’s a cat and mouse game that never ends as the rewards for even a single successful exploit can be significant.
Q: There are many studies coming out around the amount of ad fraud occurring today. Are there similar trends you’re seeing with malicious domains?
Yes. The amount of malicious pages (not necessarily domains) is increasing at an ever impressive rate.
Further, with the availability of IPv6 addresses, the potential addressable malicious pages have now become nearly infinite.
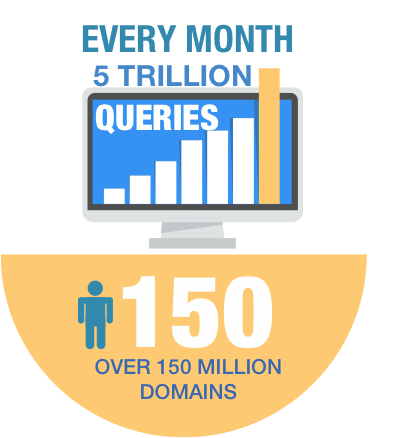
Q: How many new domains does zvelo see on a monthly basis? Of those, how many sites are considered not brand safe? How many are considered malicious?
zvelo processes over 5 trillion page-level URL requests per month, across over 150 million domains. zvelo experiences approximately 5-8% new URLs per month, which is consistent with the amount of new URLs that appear on the various Alexa and website ranking lists. zvelo’s data indicates that approximately 10-12% of the URLs are not brand safe (porn, adult, violence, etc.) and approximately 1-2% are malicious.





