Threat: Bumblebee Malware
Threat Type: Malware Loader
Over the last couple of months, we have been sharing blog posts on the topic of social engineering with the intent to help raise awareness about the increasingly sneaky tactics attackers are using. One of the posts from January featured several basic social engineering attack examples. As a follow up to that post, we wanted to share a couple of additional recent examples showing how attackers are using the file sharing sites WeTransfer and Smash to distribute Bumblebee malware via sales Request For Proposals (RFPs).
Bumblebee Threat Overview and Attack Characteristics
Bumblebee is a stealthy malware loader that is not easily detected by antivirus vendors because it often can install itself in memory without touching the disk which then allows additional malware to be installed such as ransomware or Cobalt Strike. Bumblebee is distributed by phishing email campaigns recently observed masquerading as a Product Requirement Document (PRD) or a Request for Proposal (RFP). In September of 2021, Google Threat Analysis Group (TAG) began observing Bumblebee malware and identified EXOTIC LILY as the threat actor.
Financially motivated, EXOTIC LILY operates as an Initial Access Broker (IAB) and has been associated with data exfiltration and human-operated ransomware, including Conti and Diavol. EXOTIC LILY operates by spoofing legitimate companies and employees as a means of gaining trust of targeted organizations, using legitimate file-sharing services like Smash and WeTransfer to evade malicious detection tools and deliver their payload disguised as business requirements or proposals. The characteristics of the attacks that zvelo has seen in the last few weeks are consistent with the same tactics, techniques, and procedures (TTPs) that were originally observed by TAG.
Bumblebee Malware Delivery Examples
The threat actors begin by submitting a contact us form via a vendor or company’s website using a spoofed company and identity. The oddly worded message, plus a quick verification via LinkedIn showed that the legitimate Damcosoft company using a .com TLD vs the .net indicated by the email in the form submission, raised suspicions. In this case, the target was unable to verify whether or not the supposed employee who submitted the form actually existed or not.
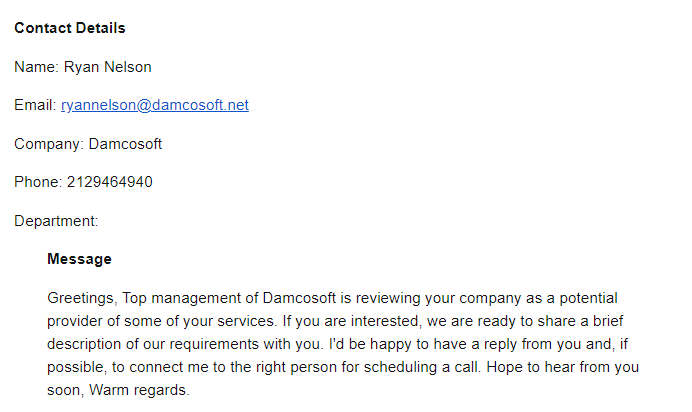
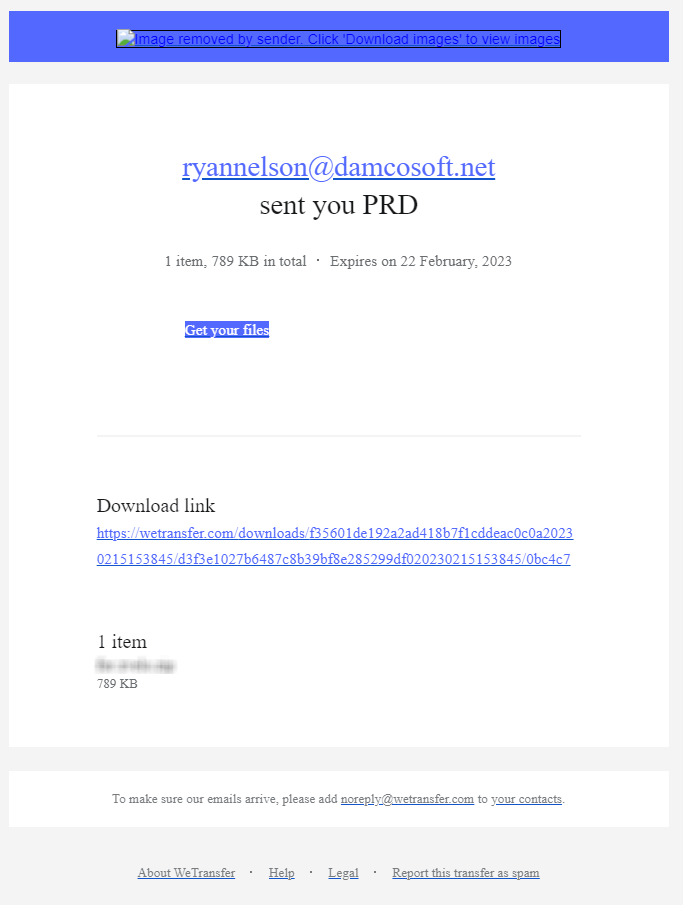
Most companies will use some type of autoresponder message to sales form enquiries, which the attacker then used to create a notification from WeTransfer that Ryan Nelson shared a product requirements document with a link to download the file and a password to download the document.
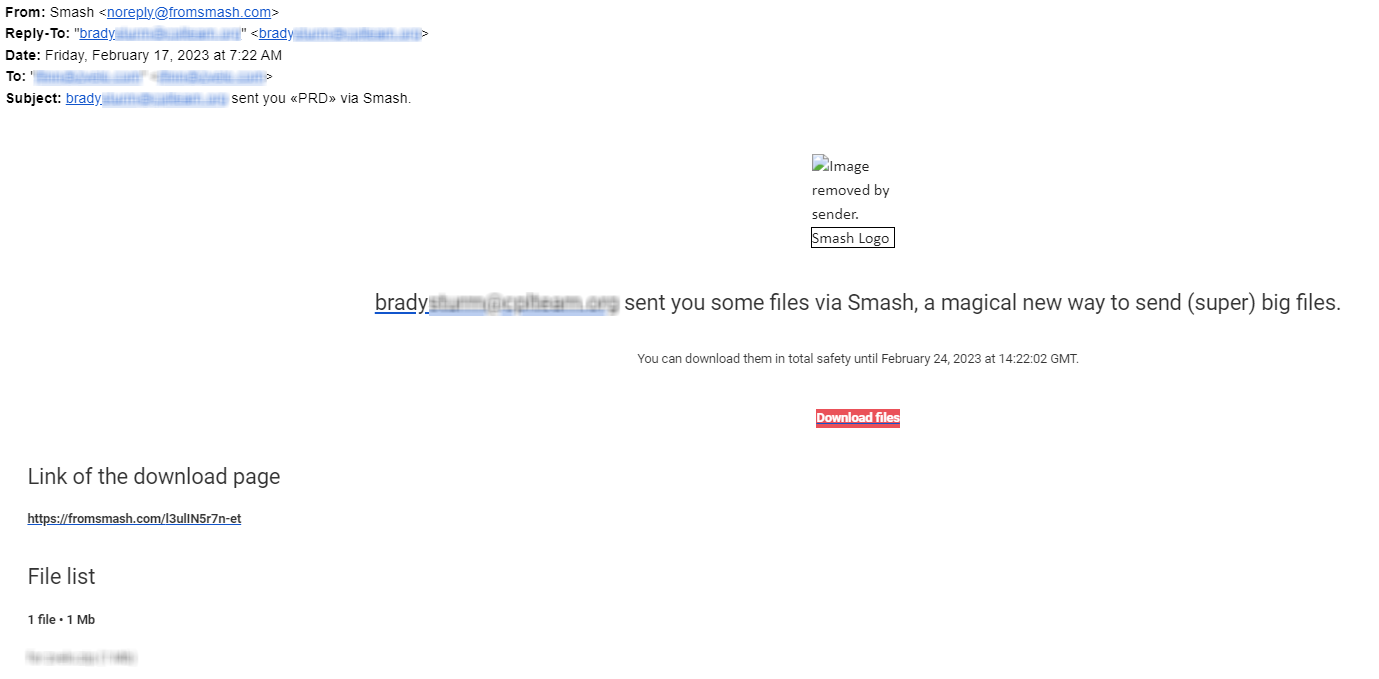
In a different example, a threat actor (possibly the same threat actor) attempted to engage the target via a LinkedIn connection request. In this case, the individual had spoofed the LinkedIn profile of an actual employee at an actual, legitimate business. After a couple of emails back and forth with the target, the threat actor sent the following email message and the password for the document shared on Smash.
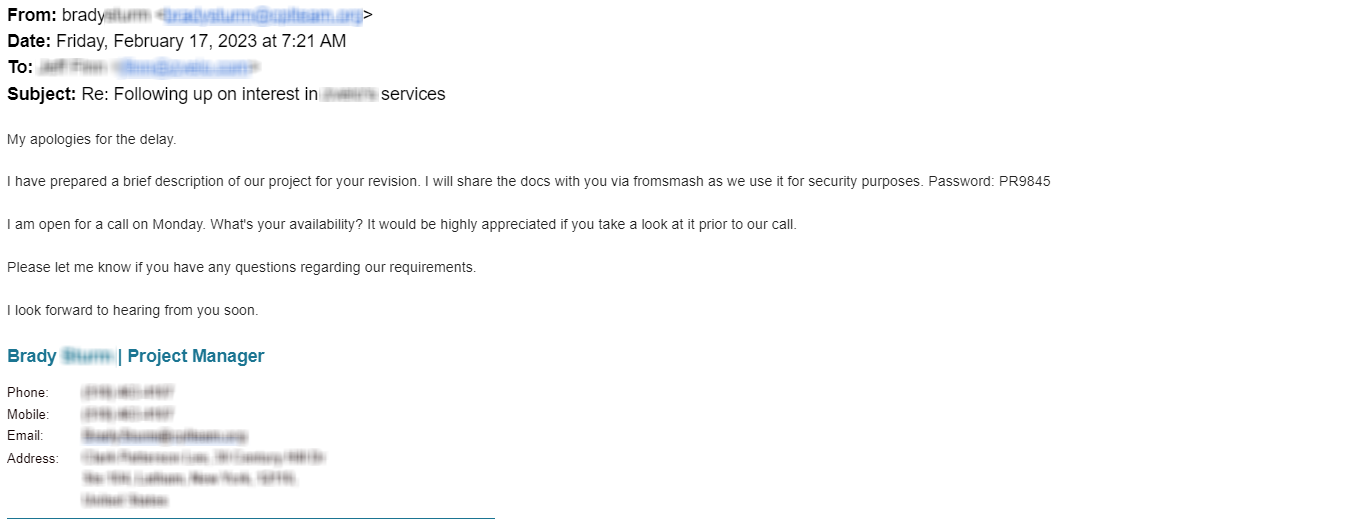
Immediately followed by the RFP shared via Smash.
Protection Against Bumblebee Malware
Because the threat actor uses shared storage sites to deliver the bumblebee malware, and the malicious links are most likely personalized for each attack target, attempting to block the URLs at the domain level is not always practical. Especially in cases where the domain is from OneDrive, Google Docs, or other commonly used and whitelisted sites.
The best protection against these types of social engineering attacks is to remain vigilant and proceed with extreme caution any time you see something that is out of the ordinary. For example, when the wording of an inbound message seems odd or if the request doesn’t quite fit with what is typical for your organization, be immediately suspicious. Educating employees with routine training and updates is critical to reducing the organization’s risk because employees are both the first line of defense, as well as the easiest target to compromise.
Cyber Hygiene Best Practices
In addition to training and awareness, creating good cyber hygiene habits can be a very effective social engineering countermeasure. zvelo’s Cybersecurity Team recommends the following high impact, cyber hygiene practices to make your organization a hardened target:
- Organizations need to implement multi-factor authentication (MFA) to make it more difficult for an attacker to use credentials obtained through social engineering.
- Enforce password management policies that require complex and hard to guess passwords. Additionally, users with both admin and regular accounts must be required to set a unique password for both.
- Make sure all of your software and operating systems are up-to-date. This will help to ensure that any vulnerabilities are patched and your device is secure.
- Ensure ports, protocols, and services that do not have business users are turned off. Those that do, need to be updated from legacy services (e.g. Turn off SMB v2).
- Establish least privilege access and ensure proper separation of permissions by conducting an audit on groups in your organization. Limit permissions to only those who need them and have a specific purpose. (e.g. Someone on the Engineering team doesn’t need access to the HR files.)
- Divide Responsibilities: Implement a separation of duties for critical processes, such as wire transfers, between multiple parties so that even if one employee is tricked, the action cannot be completed without engaging the other party or parties.