In this article, we present a trend analysis of global Cobalt Strike activity over the first quarter of 2022 in order to gain a better understanding of today’s threat landscape and how we can potentially defend against such threats.
Cobalt Strike is a legitimate, commercially available tool used by penetration testers to perform adversary simulations and red team operations. The product is designed to execute targeted attacks and emulate the post-exploitation actions of advanced threat actors. Unfortunately, this popular tool is being used by attackers of all skill levels ranging from the common criminal, to the advanced cybercrime gangs, and even nation sponsored attackers.
In the past, adversaries would use various means such as macro laden phishing attacks or other malware such as QBot and Emotet (which are dangerous in their own right) that would act as a loader in order to gain initial access. Once a foothold was established, Cobalt Strike would be deployed to maintain access and communication to attacker controlled infrastructure. This methodology has changed, and now Cobalt Strike is being actively used throughout all phases of the attack lifecycle.
Furthermore, deployment of Cobalt Strike as part of an attack significantly increases the severity of the attack. Once Cobalt Strike is executed on a system, attackers can broker the system as an initial access point to other threat actors including ransomware group affiliates as part of a larger ransomware-as-a-service operation. This means that during the course of a compromise, there could potentially be one or more adversary groups roaming around inside of a given network.
Cobalt Strike Threat Trend Analysis
Based on our available data over the first quarter of 2022 we observed, on average, 2000 Cobalt Strike server instances per month with more than 50% of the Command and Control (C2) servers throughout the quarter having originated from IP space in China as seen in figures 1 and 2.
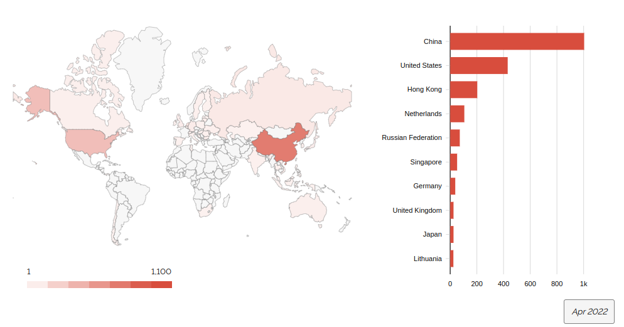
Figure 1: This image shows the distribution of Cobalt Strike servers by country for the month of April 2022.
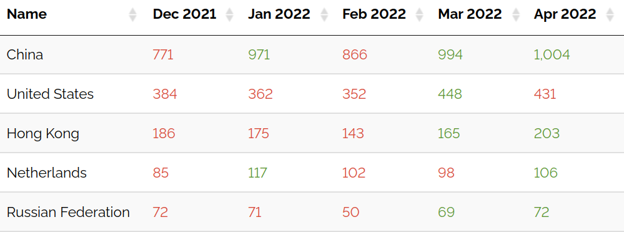
Figure 2: This table shows the distribution of Cobalt Strike servers by country.
To no one’s surprise, attackers are almost exclusively using cloud hosting providers such as Tencent Cloud Computing, and Amazon Web Services (AWS), as well as “bulletproof” hosting providers like Vultr as seen in figures 3 and 4. This provides attackers the ability to set up their attack infrastructure and tear everything down in a very quick, and cost effective manner. In some cases adversaries are able to use pre-defined templates to rapidly spin up cloud instances in a matter of minutes.
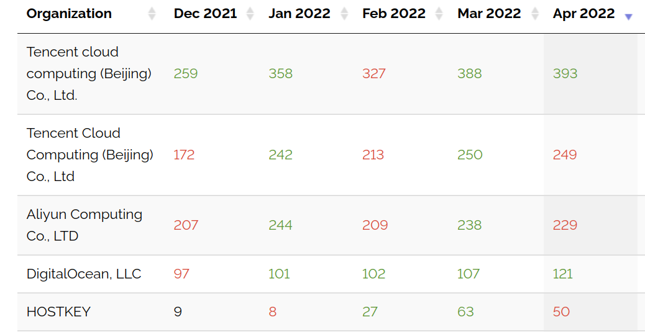
Figure 3: This table shows the top 5 organizations observed hosting Cobalt Strike servers.
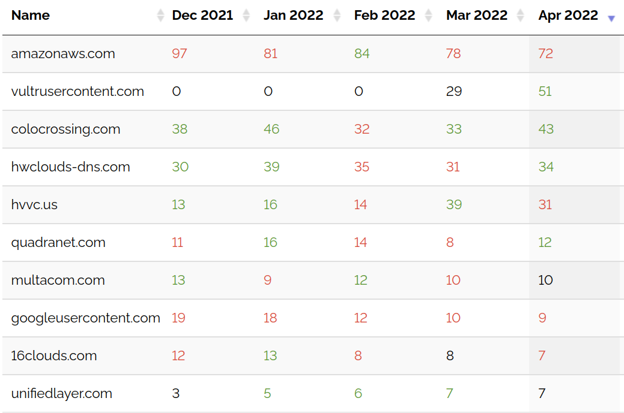
Figure 4: this table shows the the distribution of Cobalt Strike servers by domain
Coincidently, even though Cobalt Strike instances are still at an all time high, ransomware based attacks involving Cobalt Strike have gone down. “Since a significant number of criminal organizations operate out of the Russian Federation it is believed that ongoing economic sanctions over the invasion of Ukraine have made it harder for cyber criminals to organize and receive ransom payments. This makes it harder to move money around and in turn more difficult to buy infrastructure on the web,” said Rob Joyce, Director of Cybersecurity at the National Security Agency (NSA), while recently speaking at the National Cyber Security Centre’s (NCSC) Cyber UK event in Newport, Wales.
With that being said, even though there has been a reduction in ransomware attacks, it doesn’t mean the issue has suddenly disappeared. Long term effects from economic sanctions could lead to a pseudo power vacuum in the criminal space which will open the door for non Russian based criminal organizations to take over the criminal market.
Conclusion
Cobalt Strike is one of the most advanced and versatile adversary emulation frameworks on the market today, and continues to be the first choice for adversaries for the foreseeable future. Organizations must take great care and implement a defense in depth strategy to address both the technological and human aspects to prevent their organization from becoming victims of adversaries who are looking for their next ransomware victim.
Recommendations for Threat Protection
Since most attacks begin with phishing or other forms of social engineering, it is important to be aware and never provide sensitive or personal information through email, unknown websites, or over the phone. Remember, social engineering attacks are designed to take advantage of a user’s possible lapse in decision-making and are designed to appear legitimate. The best protection is a combination of awareness, education, and security controls.
- Don’t open attachments or links from unsolicited emails, even if the emails came from a recognized source. If the email is unexpected, be wary about opening the attachment and verify the sender intended on sending the email.
- Enterprises should educate and train their employees to be wary of any communication that requests personal or financial information. They should also instruct employees to report the threat to the company’s security operations team immediately.
- Reduce your attack surface by closing any ports, or protocols for which you do not have a valid business use.
- Conduct proactive threat hunting in your environment in order to identify the following:
- Any suspicious applications or protocols being used in a non standard way.
- Ensure your organization is not communicating with any country for which you do not have a business use case.
- Execution of suspicious scripts such as Base64 encoded PowerShell.
- Any registry key value larger than 1MB in size (may or may not be Base64 encoded).





