Cyber Threat Intelligence (CTI): Analysis, Dissemination, and Feedback
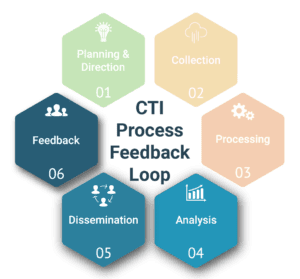
In our previous two blogs, we covered the first three parts of the CTI Process Feedback Loop: Planning & Direction, Collection, and Processing. To complete the CTI Process series and demonstrate how the full cycle supports zvelo’s ability to deliver deep insights to its clients, the post will focus on the final three parts of the CTI Process: Analysis, Dissemination, and Feedback. Additionally, this post illustrates how zvelo supports each of these stages in delivering actionable intelligence via industry standard solutions, such as APIs.
CTI: Analysis
Analysis is the stage of the CTI Process which directly follows Processing. As we have mentioned in previous posts, the roots of CTI are found in military intelligence, where we find the definition of analysis in Army Techniques Publication (ATP) 2-33.4: “Examine relevant information using reasoning and analytic techniques to reach a conclusion/determination.”
For Analysis in CTI the key word in that definition is relevant. Assuming the useful information derived from the raw data was collected based on Priority Cyber Intelligence Requirements (PCIR), Friendly Cyber Information Requirements (FCIR), and C-Suite Critical Cyber Information Requirements (C3IR) — which goes all the way back to Planning & Direction — relevant information should be in hand.
The goal of Analysis is to take the useful information from Processing and extract Intelligence, ready for dissemination. So what happens to all the additional information which doesn’t support PCIR, FCIR, or C3IR and, therefore, is deemed not relevant? Is it simply thrown away? In short, it can be tossed, however, a better strategy is to store that information for later analysis as time allows. When trying to discover a needle in the proverbial haystack, an analyst needs stacks of hay to search.
Analysis Methodologies
There are three basic types of analysis methodologies: Manual, fully-automated, and hybrid. Each are described here:
- Manual Analysis: A human analyst takes the information provided and uses software tools, combined with intuition and experience, to discover the nuggets which will be used to create intelligence products. This methodology is not only time consuming, but fraught with the biases that any human being brings to the table. It is rare to find this type of analysis as the sole methodology used by organizations today.
- Fully-Automated Analysis: Queue the machines…sort of. Fully-automated analysis takes advantage of a machine’s inherent ability to sift through vast amounts of information very quickly. Fully-Automated Analysis can be rules-based, meaning the machine applies pre-determined guidelines to produce usable intelligence. Alternatively, Fully-Automated Analysis can utilize Machine Learning (ML) and/or Artificial Intelligence (AI) algorithms to deliver actionable intelligence. It is important to note that both concepts take time to get right and may still include the biases of those who created the algorithms..
- Hybrid Analysis: Is a mix of automation and manual analysis techniques. In Hybrid Analysis, machines do the bulk of the work, while humans perform spot checks. When the machines cannot make a determination, it asks for “help” from a human analyst to do what people do best — focus on a single issue rather than an entire haystack. Most organizations today employ hybrid analysis.
zvelo’s Role in CTI Analysis
Throughout the course of a single day, zvelo analyzes several hundred million Uniform Resource Locators (URLs) using a Hybrid Analysis model.
Using human-supervised ML backed by advanced AI technologies, zvelo delivers actionable insights to its customers by classifying URLs across 500 distinct topic-based categories, as well as malicious, phishing and objectionable detections. For malicious and phishing URLs, zvelo conducts proprietary analysis and enrichment to produce an actionable CTI product (such as a feed). Feeds can be immediately ingested into customer products or network defense systems to break the cyber kill chain by disrupting a variety of MITRE ATT&CK techniques in their Cyber Operating Environment (COE).
zvelo maintains a multi-disciplinary team to conduct manual analysis when automated analysis is unable to provide an acceptable outcome. It is key to note that building CTI products for the sake of creating them provides little value — unless they answer questions posed by PCIR, FCIR, and/or C3IR. zvelo conducts CTI analysis enabling customers to focus on their core businesses.
CTI: Dissemination
After analysis is complete and the CTI products have been created, the next step is to disseminate those CTI products to consumers. Dissemination is the delivery of CTI products according to the format and timelines specified by the user. The explanation here is simple — if the customer updates their system with new CTI products every 24 hours, then delivery must support that requirement. If the customer is providing near ‘real-time’ protection to their users, then delivery must support that construct.
Related to delivery timeliness is product format. For example, CTI feeds are typically delivered in one of three formats:
- Structured Threat Information Expression (STIX™). STIX™ is divided into Domain Objects which organizes the data into manageable parts (https://oasis-open.github.io/cti-documentation/stix/intro.html).
- Malware Information Sharing Platform (MISP). MISP is an Open Standard for Threat Information Sharing which provides an attribute and categories/types construct for organization data (https://www.misp-project.org/).
- Custom Schemas. Custom schemas defined by the organization providing CTI products for consumption. This means that the organization receiving products using a custom schema may have to transform them prior to use in their environment.
Dissemination Methodologies
In the ever changing world of cybersecurity vulnerabilities, vectors, and threats, CTI products must be delivered in a timely manner. A variety of dissemination options make expedient delivery possible:
- Flat file downloads: CSV, JSON, spreadsheet, text files are made available to the customer.
- API: Programmatic access to products allowing customer access to pull the data they want based on types, time ranges, and other parameters.
- Feeds: Automatically pushes products to customers in an agreed upon format.
Accessing any of these dissemination methods should be done via the appropriate secure authentication capabilities.
zvelo’s Role in CTI Dissemination
zvelo’s current CTI roadmap includes all three of the dissemination methodologies presented. zvelo’s goal is to deliver the right CTI products, in the desired format, and within the timeline desired by our customers.
CTI: Feedback
The final piece of the CTI Process is Feedback. In practical terms, feedback is a dialogue between the intelligence producer and the intelligence consumer, or customer. Feedback should be collaborative. Producers must be willing to listen to feedback and the customer must be willing to offer it. Feedback should also be push and pull. In other words, the customer should push feedback to the producer and the producer should proactively reach out to the customer to pull feedback.
Feedback can also be viewed as helping the CTI producer to assess the value of the products delivered. This assessment is typically viewed in two bins:
- Measure of Performance (MOP): Quantitative metrics on how much/how many CTI products were produced and delivered.
- Measure of Effectiveness (MOE): Qualitative assessment of how well the CTI products produced and delivered fulfilled organization PCIR, FCIR, and/or C3IR.
Analyzing both MOP and MOE feedback can help the CTI producer tune their pipeline to ensure the most actionable intelligence is delivered.
zvelo and CTI Feedback
First and foremost, zvelo is a collaborative organization that regularly reviews feedback from our customers. For example, zvelo maintains 24/7 coverage of our web content categorization efforts to quickly review and correct any classification errors. zvelo’s CTI products include methods for both interactive and offline feedback from customers. We measure both MOP and MOE for CTI products and drive that information back into the CTI Requirements & Planning process thus completing the loop. This ensures that zvelo continuously refines Collection to stay ahead of Malicious Cyber Actors (MCAs).
Where zvelo Fits…
zvelo supports the entire CTI cycle starting with Planning & Direction which is driven by our partners (external) and deep subject matter expertise (internal). zvelo collects billions of data points across the ProActiveWeb, ActiveWeb, and InActiveWeb, in addition to integrating multiple proprietary data sources so your organization benefits from having a single source for intelligence data. zvelo then processes the raw data into information bins for Analysis in Web Content Categorization, Suspicious Domain Intelligence, Malicious Detections, and Phishing Detections. The zvelo multi-disciplinary Team processes all this information, prepares it for Analysis, and develops CTI products for Dissemination in the desired schema, format, and timeline. zvelo then solicits Feedback to continually improve our products to best protect the web. If you want to learn more about zvelo and its expanding CTI offerings, please contact us!





