If you have been around the cybersecurity business in the past 5-10 years, Cyber Threat Intelligence (CTI) has probably become part of your vocabulary. CTI is somewhat challenging to define, as its meaning within the Cyber Intelligence community varies by role, as well as by the value it delivers. To some, it is simply a feed of information about current threats. To others, it may be the latest report detailing the actions of an Advanced Persistent Threat (APT). Regardless of its varied meanings, CTI can be a ‘firehose’ of information that — if not properly curated — delivers little value. So, what is CTI really? To establish a baseline understanding, zvelo defines CTI as a process feedback loop, adapted from military doctrine, to deliver actionable intelligence to a decision maker. CTI as a process is shown in the figure below:
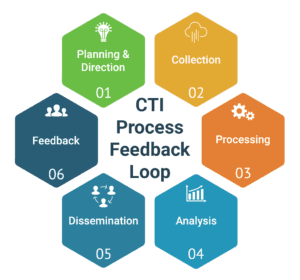
The key words to focus on here are actionable and decision. Intelligence that is not actionable is nothing more than noise. Related, intelligence that does not support the needs of a decision maker has little to no value. This leads to the question — How do you procure or produce actionable intelligence? Ultimately, it comes down to well defined requirements.
As CTI is rooted in military doctrine, we will share some terms which may, or may not, be familiar. Seasoned Military Intelligence personnel will tell you there are three types of requirements which must be defined to understand an Operating Environment (OE):
- Priority Intelligence Requirements (PIR): What you need to know to complete the mission. Specifically, what do you need to know about the enemy.
- Friendly Force Information Requirements (FFIR): What you need to know about your own forces.
- Commander’s Critical Information Requirements (CCIR): Key information needed to support decision making.
PIRs, FFIRs, and CCIRs are tracked from initiation to completion, supporting decision points. Answers to PIRs are termed Essential Elements of Information (EEI). In military operations, these lists of intelligence requirements are considered living documents, as ever-changing as the OE. As requirements are answered, the Military Commander adds the next intelligence question to the list. If the answer to a requirement is not satisfactory, the Military Commander provides feedback to the Intelligence Team, and the cycle continues.
In general, CTI is used by organizations to enhance their defensive posture by understanding threats in relation to their Cyber Operating Environment (COE). With that in mind, we’ll adjust the military-based definitions from above to better describe an organization’s requirements for CTI:
- Priority Cyber Intelligence Requirements (PCIR): What are the potential Cyber Threats to your organization? Be sure to include Malicious Cyber Actors’ (MCAs) intent to cause harm.
- Friendly Cyber Information Requirements (FCIR): What do you need to know about your organization’s COE? From a Defense-in-Depth (DID) perspective — Perimeter, Networks, Endpoints, and Data — including related vulnerabilities.
- C-Suite Critical Cyber Information Requirements (C3IR): What is the key information executive leadership must have to make decisions? For example, if you have a system with a critical vulnerability, is there a threat with intent to exploit it? And how will you know if, or when, a breach actually occurs?
It is important to establish your organization’s PCIR, FCIR, and C3IR before you even consider either procuring CTI sources/feeds, or building your own. Know your organization’s COE, and establish the executive leadership’s priorities to avoid the old adage, ‘if everything is a priority, then nothing is a priority’. Organizations looking to utilize CTI successfully, should make a risk-based determination of their Cyber Intelligence needs first, and then look for the feeds or sources which provide the most value. Unfortunately, many organizations buy one, two, or even more CTI feeds or sources without a clear understanding of what makes their COE an appealing target for MCAs. This results in blindspots in coverage, data overload, integration issues and worse — MCAs hanging out, undetected in their environment for 200+ days (per IBM, the global average for breach detection in 2019 was 206 days).
Here is the secret to CTI. Each organization has a unique set of needs and priorities. While many organizations have the same or similar technology stack, the way each organization leverages that technology stack is significantly different. Every organization’s COE is truly organic, and integrating CTI should be too. Also, keep in mind that CTI needs are vastly different across industry verticals. For example, the Finance sector has distinct requirements which don’t necessarily apply to the Energy sector — at least from a Cyber Threat perspective. After establishing a solid understanding of their requirements, every organization should, at minimum, ingest at least one general, and one industry-specific CTI feed/source.
Actionable Steps to Successfully Implement CTI
- Look at CTI as a cyclical process (as shown), not a solution-centric problem. Leverage the feedback loop regularly to ensure your CTI feeds/sources/products are providing actionable intelligence to support decision makers.
- Work with your organization’s executive leadership to establish PCIR, FCIR, and C3IR within the context of your COE. When you establish requirements and priorities, it will help you identify the best CTI feeds or sources to improve your overall Cyber Defense.
- Consider procuring multiple feeds or work with a partner that already does. Analysis by the zvelo Cybersecurity Team has established that there is limited overlap between the variety of existing and growing sources/feeds.
Links to additional articles on how zveloCTI supports the entire process feedback loop for our partners across the areas of web content categorization, malicious detection, and phishing may be found below. And, as always, please let us know if, or how, we can assist with your organizations threat intelligence or needs.
Part 2 – zveloCTI: Collection and Processing





