Cyber Threat Intelligence (CTI) is actionable Intelligence data pertaining to an organization’s information systems, networks, or digital assets that is intended to inform Cybersecurity and Threat Intelligence teams about potential risks and existing or emerging threats. As cybercriminals continue to grow more sophisticated in their attack tactics, gathering and leveraging cyber threat intelligence is a critical element to protecting your infrastructure and assets against cyber attacks and building a proactive, rather than reactive, cyber defense strategy. This blog post shares a comprehensive overview of cyber threat intelligence to provide a solid understanding of what cyber threat intelligence is and how it can most effectively be used to protect your organization against cyber threats and deliver maximum value. In addition to covering the basics of what it is, who uses, and how, we detail the different types of threat intelligence available, the cyber threat intelligence process lifecycle, primary use cases, and threat feed evaluation guidelines.
Types of Cyber Threat Intelligence
Cyber threat intelligence can be segmented into four main types: Strategic, Operational, Tactical, and Technical.
Strategic Cyber Threat Intelligence
Strategic threat intelligence is generally non-technical in nature and focused on high-level threats and risks to an organization. Strategic intelligence provides crucial insights about which threat actors might be behind an attack, as well as their primary motivations. Additionally, strategic threat intelligence should include some level of human analysis to better understand the threats within the context of threat trends, foreign policy issues or global events like the pandemic that could potentially impact an organization’s risk posture. This type of threat intelligence is used by executive leadership to help guide long-term planning and business decisions around cybersecurity, as well as infrastructure, budgeting, staffing, and more.
Operational Cyber Threat Intelligence
Operational cyber threat intelligence focuses on the technical details of a threat to identify the attacker tactics, techniques, and procedures (TTPs). TTPs shed light on how a particular threat actor operates and the environments they operate within and can offer insight on things like motive, timing, or methods for executing an attack. Operational threat intelligence can be used to help identify security and remediate security incidents, understand the extent of breaches, conduct proactive threat hunting, and support a range of other defensive actions.
Tactical Cyber Threat Intelligence
Tactical cyber threat intelligence focuses on attacker TTPs to help security teams understand the attack vectors so they can address system vulnerabilities and improve their defense against the identified threats. Because tactical intelligence is technical in nature and primarily identifies Indicators of Compromise (IOCs), it can be easily automated and ingested into security platforms to support day-to-day operations. The IOCs can be used to triage and validate alerts, support rules for firewalls or intrusion detection/prevention systems, endpoint detection & response systems, and other similar capabilities. Although tactical threat intel is readily available through a number of open-source threat intelligence (OSINT) and commercial threat feeds, it’s critical to note that IOCs tend to have a very short lifespan so security teams will need to be extra judicious when it comes to evaluating OSINT vs commercial threat intelligence feeds.
Technical Cyber Threat Intelligence
Technical cyber threat intelligence focuses on tools, artifacts, or other warning signals that can indicate the onset of a potential attack. These signals can include social engineering, spear phishing, or other IOCs that fall under the reconnaissance or weaponization and delivery stages of the cyber kill chain. Threat teams can then use those signals and IOCs to further investigate and take action as necessary. Technical and tactical threat intelligence are very similar but a simple comparison would be that the tactical intel details the specific malware used in an attack vs the technical intel that provides specifics on the implementation of that malware. Much like tactical intelligence, technical cyber threat intelligence has an extremely limited lifespan so timing and accuracy is crucial in using it for cyber defense.
Who Uses Threat Intelligence
Now that we’ve defined what each of the different levels cover, let’s move on and cover the types of users, why, and how each of the cyber threat intelligence levels can be used based on some of the most common use case scenarios that cyber defenders encounter.
Strategic Users
In most organizations, strategic threat intelligence users are individuals in the “C-Suite” — the Chief Executive Officer, Chief Financial Officer, Chief Information Officer, and so on depending on structure. In other words, these personnel are the high-level executives, leaders, and management of an organization. Strategic users consume cyber threat intelligence data to gain an understanding of top-level trends and threats to the organization. They may or may not have a technical background, and they utilize cyber threat intelligence to support their needs when making risk-based decisions regarding staffing, technologies, cybersecurity requirements, and ultimately budgets. Without the threat intelligence information, strategic users may lack information critical to procuring the necessary resources to secure their organization.
Operational Users
Operational cyber threat intelligence users in an organization include a wide variety of personnel including, but not limited to: Incident responders and teams, network defenders, host analysts, malware analysts, forensic analysts, and more. Large institutions commonly employ all of these work roles, while smaller organizations tend to have fewer capabilities and may, or may not, contract for them. Operational users consume cyber threat intelligence for technical context, with a focus on the IOCs themselves, related linkages, and whether or not they might be found in the environments they are responsible for securing. Context is critical for operational users because every environment is unique in how they use various technology stacks.
Tactical Users
Any organization with security personnel can benefit from tactical threat intelligence. From the largest organizations with dedicated SOCs, to the smallest who only have a few cyber defenders or may have outsourced to Managed Security Service Providers (MSSP), reliable threat intelligence is essential in today’s ever increasing threat landscape. Tactical users are on the frontlines of an organization’s cyber defenses and leverage IOCs, content, and context to directly prevent adversarial attacks on their organizations.
Technical Users
Technical Cyber Threat Intelligence users are primarily SOC personnel, incident response teams who use the data in response to a suspected incident. The threat details are fed into an organization’s defense systems and platforms like IPS, firewalls, Endpoint Detection and Response (EDR), and so on. Technical threat intel users focus on leveraging this data to enhance their detection capabilities to improve their ability to identify attacks at the earliest possible stage to mitigate any potential damage.
Who Are the Other Users?
Organizing all those who use cyber threat intelligence into bins of Strategic, Operational, Tactical, and Technical helps codify its consumption from a cyber-focused perspective. However, it is important to consider the broader use of threat intelligence across today’s technology enabled organizations. Outside of security departments, there are numerous other business units that can benefit including legal, auditing, risk management, and other functional units. The level of support will depend on the organization’s mission, requirements, and exposures. Every organization will be different and there will not be a cookie cutter solution.
Stakeholders should also be considered as users as they are members of an organization who can directly influence resources when it comes to cybersecurity. Stakeholders can be end users, management, the C-Suite, or others who can help identify the organization’s threat intelligence needs and potentially, which feeds to procure. Ultimately, stakeholders significantly impact an organization’s overall threat intelligence program.
Finally, and increasingly important today, are third-parties who may be internal, or external, and essential to an organization’s success. Third-parties can be contractors who are part of day-to-day operations, or suppliers who deliver technologies that make modern businesses work — like cloud service providers. Cyber threat intelligence can help organizations with multiple aspects of third-party management which may include understanding their exposures, assessing linkages between their brands and supporting third-party capabilities, and addressing IOCs which may impact third-party systems directly connected to internal infrastructure.
Common Use Cases
There are endless use cases for demonstrating the need and value of cyber threat intelligence. The use cases shared below offer a broad range of ways organizations can use cyber threat intelligence.
Blocking or Filtering
One of the more simple use cases for cyber threat intelligence is to use malicious detections or phishing detections to block or filter malicious URLs or IPs and protect end users. In this use case, a threat feed supplies the phishing or malicious URLs and IPs so that a security tool or platform can then block web traffic both to and from those URLs.
Brand Exposure Intelligence
Brand exposure intelligence is a common use case which may include cybersquatting (also known as domain or subdomain squatting), domain or subdomain hijacking, phishing campaigns, and exploited web-pages/parts. Assessing exposures in each of these areas can help an organization identify how its brand is being co-opted by attackers to exploit their customers.
Threat Hunting
Threat hunting is a frequent cyber threat intelligence use case. Threat Hunting pulls from multiple sources, including cyber threat intelligence, to leverage all available IOCs that are applicable to an environment and proactively look for evidence of threat actor activities. Threat Hunting starts with a hypothesis, usually based on the hunter’s intuition or one or two pieces of data, and then leverages cyber threat intelligence to investigate further, either confirming it or moving on to the next concern.
Triage
The most straightforward cyber threat intelligence use case is triage. Regardless of whether the user is in an SOC, MSSP, or an organization with only a couple of cyber defenders, cyber threat intelligence can help quickly identify whether or not there is cause for concern. In a triage case, tactical users first check their local cyber threat intelligence store, or call the APIs of their cyber threat intelligence sources. If there is an IOC match, they move forward with their incident handling process. If there is no match, they move onto the next alert. Utilizing cyber threat intelligence in a “verify, then trust” construct can significantly reduce the amount of time analysts at the tactical level must spend to differentiate between good and bad.
Incident Response
Incident response often follows triage as it is frequently the next step in the process. By leveraging cyber threat intelligence, security teams are quickly able to make more informed decisions about potential incidents, prioritize them based on risk or severity, and follow up accordingly. For maximum efficiency in this use case, it’s critical for the threat intelligence to be highly accurate to avoid having incident response teams waste time chasing false positives.
Threat Prioritization
Threat prioritization leverages cyber threat intelligence to better understand an organization’s attack surface so that security teams can identify the vulnerabilities and assets most likely to be exploited by attackers and then adapt their defense strategies to reduce their risk.
Enriching Security Tools and Platforms
Cyber threat intelligence is also commonly used to enrich and automate security solutions like SASE, SIEM, SOAR, and so on. By enriching these tools, security teams can have greater context around the nature of certain threats to help improve the overall effectiveness and efficiency of their threat protection platforms.
Sources of Cyber Threat Intelligence
Open-Source Intelligence (OSINT)
Open-Source Threat Intelligence legally gathers information from a variety of free and/or publicly available sources – websites, blogs, online communities, books, public speeches, conferences, images, etc. As a broad source of intelligence that leverages the brain trust of the greater threat intelligence community, open-source threat intel is one of the most widely leveraged types of threat intelligence.
Closed-Source Intelligence (CSINT)
Closed-Source Threat Intelligence is basically the opposite of OSINT and comes from private, commercial, or government sources that are not freely available to the general public. Examples of CSINT include proprietary business information, law enforcement data, educational records, banking records, or medical records. Depending on the type of data, CSINT may be licensed for use in internal threat detection solutions or for commercial applications.
Human Intelligence (HUMINT)
Human Intelligence is derived from human sources and gathered through means of any sort of interpersonal contact which can include everything from a friendly conversation to an interrogation. HUMINT is commonly provided by covert agents and/or spies who may work to acquire photographs, documents, and other material as information.
Technical Intelligence (TECHINT)
Technical intelligence is derived from the collection, processing, analysis, and exploitation of data and information related to the technical or scientific abilities of an adversary. TECHINT is primarily used for developing countermeasures to neutralize an adversary’s technological advantages. TECHINT may include details about things like foreign scientific and technical characteristics, capabilities, and limitations of foreign military systems, weapons, weapon systems, and materiel.
Threat Intelligence Lifecycle
In this section we explore the different phases of the cyber threat intelligence lifecycle: Planning and Direction, Collection, Processing, Analysis, Dissemination, and Feedback.
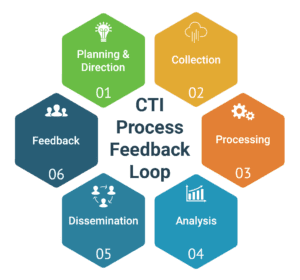
Planning and Direction
Cyber threat intelligence begins with planning and direction to establish basic needs, requirements, priorities, goals and desired outcomes. Once the involved stakeholders agree upon the needs and priorities, they should begin to identify sources and methods for collecting threat intelligence. During this phase, it’s critical to make a risk-based determination of needs first, and then identify threat feeds and sources that are best suited to those needs. A failure to truly understand the organization’s operating environment and its potential appeal to attackers prior to acquiring one or more threat intelligence feeds can often result in blind spots in coverage, data overload, integration issues, or attackers lingering undetected in their environment for 200+ days (per IBM, the global average for breach detection in 2019 was 206 days).
Collection
After defining the requirements in the planning and direction phase, the next step is collection. The collection phase is where raw threat intelligence is gathered from any number of different sources which may include third-party data in addition to self-sourced or proprietary data. Ideally, organizations should collect both third-party and self-sourced data as it can help to minimize gaps in coverage and maximize their effectiveness. Every organization should, at minimum, ingest at least one general, and one industry-specific cyber threat intelligence feed/source.
Processing
The next phase is processing where all of the raw threat data gets cleaned, normalized, and formatted so that it can be properly analyzed. The processing phase of the cyber threat intelligence lifecycle can include file decryption, translating details from foreign sources, using data enrichment to add contextual relevance to the threat data, and most importantly, data validation. Data validation is the most important step in the processing phase. Just because (pick an input, internal source, third-party feed, crowdsourced, etc.) one source claims something is malicious/phishing/evil, it may or may not be accurate. The old saying “trust but verify!” is particularly true when it comes to cyber threat intelligence processing.
Analysis
After the raw data has been processed and validated, it progresses on to the analysis phase of the threat intelligence lifecycle. During this phase, security teams thoroughly analyze the data to look for patterns and correlations that may help them with threat actor profiling and attribution. The main goal of the analysis phase is to answer the questions defined in the planning stage and then define action items and recommendations for stakeholders.
Dissemination
After analysis is complete and the actionable cyber threat intelligence has been generated, the next step is to package and disseminate that data to consumers. Dissemination is the delivery of cyber threat intelligence data according to the format and timelines specified by the user. The explanation here is simple — if the customer updates their system with new cyber threat intelligence products every 24 hours, then delivery must support that requirement. If the customer is providing near ‘real-time’ protection to their users, then delivery must support that construct.
Feedback
The final piece of the cyber threat intelligence lifecycle is Feedback. In practical terms, feedback is a dialogue between the intelligence producer and the intelligence consumer, or customer. Feedback should be collaborative. Producers must be willing to listen to feedback and the customer must be willing to offer it. Feedback should also be push and pull. In other words, the customer should push feedback to the producer and the producer should proactively reach out to the customer to pull feedback.
Evaluating Threat Feeds
When it comes to evaluating cyber threat intelligence feeds, below are a number of guidelines to keep in mind and weigh against the outcome you are trying to achieve. For vendors that are simply looking for a basic blocking approach, some of the criteria below will be less crucial. Vendors who choose to pursue a maximum protection model that will support both threat detection and response are advised to critically evaluate the key areas below as these will make or break your solution.
- Threat Detection Speed. How quickly are new and emerging threats detected — hours, days, longer? While the average time to detect can be tricky to pinpoint, it can be evaluated by measuring one threat feed provider against another. It goes without saying, the fastest time to detect is crucial to threat protection.
- Accuracy. While the fastest time to detect may be a leading priority, it should not be considered independently of accuracy. A lack of accuracy, or high false positive rate can ultimately work against you.
- Coverage. Your visibility into the threat landscape, and ability to protect users and endpoints, depends on having extensive coverage of the ActiveWeb and global clickstream traffic.
- Curation vs Aggregation. Data curation itself is another fuzzy definition. There are threat feed providers claiming to curate threat feeds, but what they are really doing is aggregating a selection of raw threat feeds, as opposed to actually curating threat data that comes from those feeds to have maximum coverage with the lowest possible amount of false positives.
- Content Classification. A premium domain database will also have excellent coverage for all forms of objectionable and other content, providing the vendor with the opportunity to offer content-based filtering to supplement the phishing and malicious threat protection.
- Real-Time Detection/Update Capability. What constitutes ‘real-time’ in terms of technology applications can vary from minutes to hours. It’s important to understand how each threat feed provider defines real-time detections, as well as real-time updates (the time between which a threat is detected and the time that threat propagates to deployments).
- URL Level for Blocking. It’s important to have the ability to filter and block URLs at various levels depending on the implementation — domains, subdomains, IPs and full-path. In some cases, blocking at the domain and subdomain is perfectly fine. Other times, full-path URL blocking is necessary to protect against threats more deeply embedded in commonly whitelisted sites like google docs, Dropbox, etc.
The value of cyber threat intelligence can be difficult to assess as it is highly subjective and very much dependent upon who is using it and the specific purposes for which it is being used. In some cases, the value may be found in significant cost savings from not having to manage the infrastructure and human resources required to collect and process massive volumes of data. For others, the value of curated threat intelligence may be found in operational efficiencies by streamlining the number of threat intelligence sources and reducing the workload for normalizing and standardizing the raw data for processing. And many other organizations that lack the internal resources to perform the threat analysis will discover value through the direct performance results, reduced cyber risk and improved threat posture. Whatever the case, it’s important to understand the type of threat intelligence you need to find the best fit to drive your desired results.
Additional Recommended Reading:
From Raw to Refined: 5 Reasons To Get Curated Threat Intel
In-House Cyber Threat Intelligence Begs a Multi-Million Dollar Question
Premium Threat Intel: A Vital Cybercrime Investment
OSINT vs Commercial Threat Intelligence
6 Steps to Driving Quantifiable Value From Cyber Threat Intelligence (CTI)





