Estimated Reading Time: 7 minutes
In part 1 and part 2 of this blog series, we’ve covered the various technologies behind next-generation 5G networks—as well as device growth trends, costs, and timelines associated with global rollouts. We’ve also addressed how 5G will accelerate a paradigm shift away from traditional network connections as mobile wireless networks become increasingly capable. The changing connection habits of consumers, employees, and devices will surely produce new security implications and challenges for network administrators and service providers alike.
With the convergence of 5G and IoT, we can expect the massive growth in connected devices to continue—even accelerate—leading to significantly more internet queries, connection points, and web traffic. This all points to a substantially larger threat surface—with new opportunities for hackers and bad actors to distribute malware, execute ransomware campaigns, distribute objectionable or dangerous content, and generally find new and clever ways to compromise networks and devices.
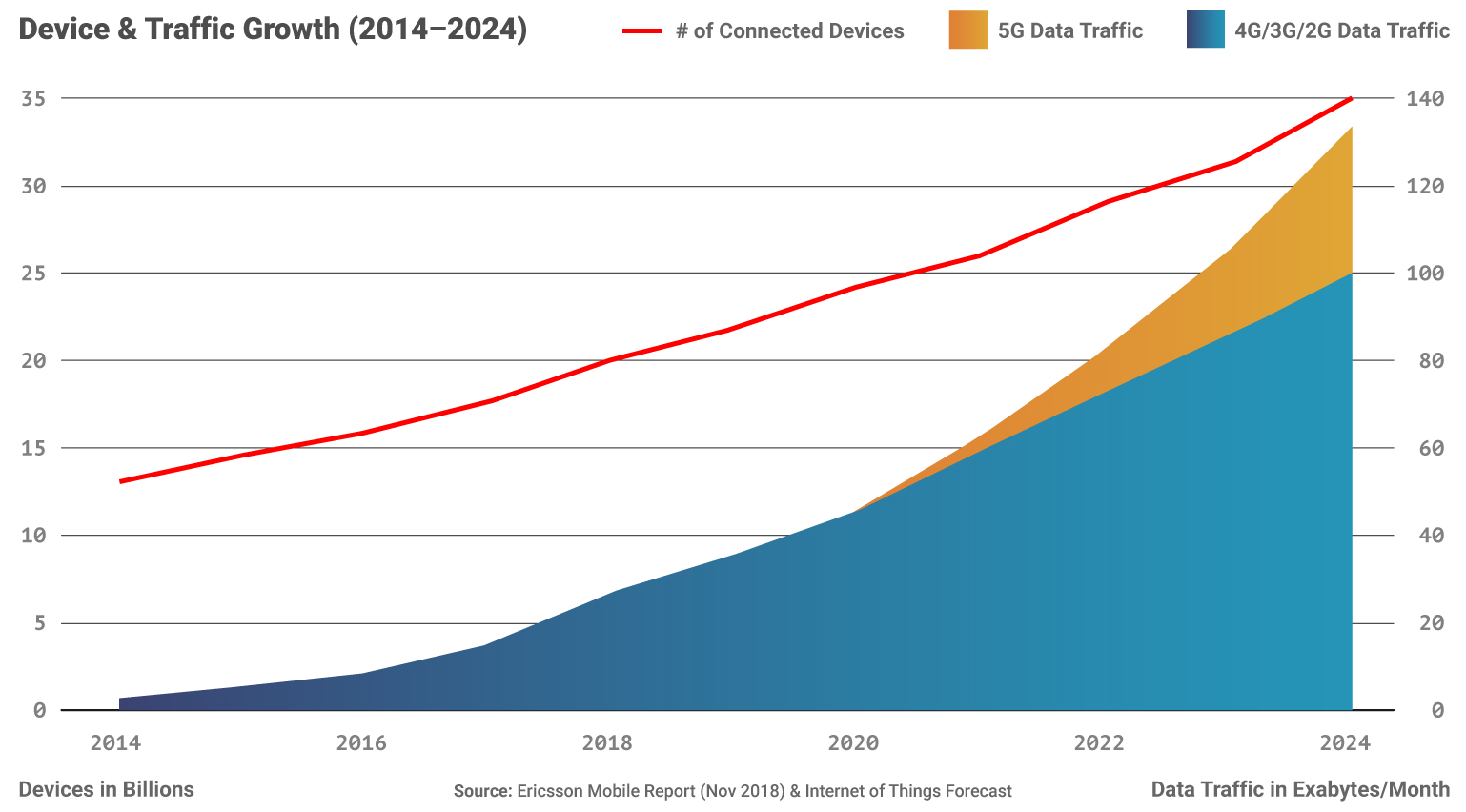
Source: Ericsson Mobile Report (Nov 2018) and Internet of Things Forecast
In this—our final installment in this 5G series—we’ll explore the growing impact malicious threats will have in the 5G era, as well as the most significant trends and technologies for security with these next-generation wireless networks.
5G Will Increase the Significance of Malicious Threats
In Part I, we discussed how ultra low-latency communication will create new opportunities for a wide range of industrial and IoT applications, as well as AR/VR powered experiences and services. 5G will fuel advances in autonomous vehicles, utilities, agriculture, medical devices, and a wide range of other industries and applications. Many of these also pose significant and widespread security and public safety risks.
As 5G networks become a pivotal delivery technology for our increasingly digitally-dependent lives—security is going to become increasingly important. The lack of it will become increasingly expensive. Hijacked or compromised autonomous vehicles are an obvious risk to human life. Medical device tampering could cause pacemaker’s or other critical implants and devices to malfunction and putting lives in danger. These examples are frightening, but pale in comparison to what security vulnerabilities in utilities or agricultural systems might cause. If our utility or food production capabilities are attacked, bad actors—or nation states—could cause mass power outages or potentially prevent millions (or more) from having access to electricity, clean water, or enough food.
On the networks themselves, compromised Radio Access Network (RAN) devices would allow for larger Distributed Denial of Service (DDoS) attacks. For consumer devices, 5G will provide faster connections for the existing web threats of the 4G era.
Unfortunately, existing malicious threats and network security gaps from the 4G era won’t just conveniently disappear into the past. It will require years, maybe even decades, to fully rollout national 5G networks. During this period of limbo, service providers will continue to support the 4G standard (as well as 3G and older standards) in order to maintain services for its existing customers on older devices and technologies—particularly in rural and remote locations. New 5G infrastructure must remain compatible—or at least operate in parallel with older technology—to meet the data needs of new services and devices supporting a growing user base. This has the potential to create a never-ending litany of security vulnerabilities.
With higher speeds, millisecond latencies, and an increase in connected devices—bad actors will seize new opportunities to unleash malware, ransomware, phishing campaigns, and DDoS attacks.
Securing 5G Networks
The importance of rock solid network security is at an all time high at the very time the definition and boundaries that define traditional networks are being increasingly blurred. Carriers, ISPs, and businesses will need to put greater emphasis on securing data and systems (in addition to networks access points) and protecting critical infrastructure from threats—particularly “zero-minute” threats which will have the ability to reach more devices at a faster rate than ever.
With a growing cybersecurity skills gap, what can we do to secure our 5G networks, as well as the supporting 4G infrastructure and the myriad of devices that will live on for years to come?
Cloud and Edge-Based Security
Businesses will increasingly rely on cloud and edge-based systems and security offerings to keep their users, devices, and data safe. Next-generation technologies in the cloud will be capable of analyzing web traffic for malware, performing deep packet inspection (DPI), and more thanks to increases in computing power, advances in AI/ML, as well as faster speeds and lower latency from 5G. With ultra-low latency and larger bandwidth, decentralized computing models will be more viable and require a new approach to security.
The leaders in the “Security As a Service” market over the next five years will be those companies that can provide the highest levels of protection for enterprises and carriers. They will accomplish this by incorporating AI-based threat intelligence, firewalls, and anomaly detection, as well as intelligent web filtering solutions in to their offerings.
AI-based Threat Intelligence and Anomaly Detection
AI-based threat intelligence and anomaly detection systems will be more important than ever to help identify and prevent damage caused by cyber threats—especially “zero-minute” threats. Malware, ransomware, and phishing campaigns are already executed with blinding speed and at scales that make it impossible for human expert-dependent analysis to address. Further exacerbating the issue is the shortage of information security and threat intelligence engineers and experts. There simply aren’t enough people with these skills to keep pace with the accelerating threats, risks, and alerts. Distributed security architectures and crowd-sourced models, along with continued advancements in AI, will empower security experts to develop and leverage new tools and approaches to stay ahead of bad actors and threats.
Intelligent DNS and Full-Path URL Filtering For Humans AND Connected Devices
With the increased performance and speeds of 5G, as well as the growing number of connected devices—premium, high-accuracy web filtering solutions will be more important than ever for network security. Safe internet browsing and experiences will be critical not only for humans—but for the growing number of “always-on” and “always-connected” IoT devices. Unfortunately, IoT and other devices that aren’t continuously used and monitored by human operators will become prime targets for hackers and bad actors—who will look to compromise and leverage the device’s computer power and internet connectivity for use in a botnet, DDoS attack, or to spread viruses or malware. These are concerns not only for device owners, but for all internet users and businesses of all sizes, worldwide. In a 5G world, threats and exploits will spread orders of magnitude faster, leading to larger data breaches and an increase in costs associated with damages from security incidents.
Web filtering of the future will need to be able to analyze and determine acceptable behaviors for humans, as well as “autonomous” connected devices—all based on context and use. Because of the nature of malicious content online—web filtering technologies MUST be able to analyze and provide accurate feedback at the full-path, post, or article level to ensure the individual web page is safe. In addition, because of the low latency provided by next-generation networks, leading web filtering solutions MUST be able to provide ultra-fast categorizations and results so as not to reduce network performance. Some latency will be an acceptable trade-off for much higher security. But anything longer than a few milliseconds will likely be a showstopper.
The web filtering leaders of the 5G era will also rely heavily on AI-based systems to categorize web content, deliver highly accurate results, and determine when a device’s browsing behavior is outside of acceptable parameters. The leading web filtering solutions will likely use a crowd-sourced method for identifying, analyzing, and aggregating results in order to provide the highest levels of protection.
Final Thoughts on 5G Networks
As 5G rolls out there’s a lot to be excited about, both for consumers and enterprises. Over the course of this series on 5G we’ve discussed how new services and technologies with added convenience—and subscription models—are sure to follow. Self-driving vehicles, smart city infrastructure, automation, manufacturing practices will all likely see huge leaps forward thanks to constant and instantaneous communication and a growing army of sensors providing real-time feedback. As 5G becomes the new standard, 4G technologies will become cheaper and more accessible for a number of countries and smaller markets around the world—providing new opportunities and connections for hundreds of millions more. 4G connections won’t be going anywhere any time soon—and will continue to play a critical role in mobile service—particularly in developing countries and outside of urban, high-population areas.
But with more devices, connections, and traffic there are also much higher stakes for security. Higher speeds and lower latency will highlight the ability of bad actors and cyber threats to spread rapidly, compromising more devices with malware and botnets, executing phishing attacks against greater numbers, and likely increasing the number of data breaches and other security incidents.
The network security community already faces an enormous skills shortage—and widespread security threats continue to cause billions of dollars in damage and remediation efforts. By 2023, the cyber security market is estimated to grow to $248.26 billion (USD)—a 10.2% CAGR (2018–2023). While we can put increased focus and importance on security going forward, in order to close the widening gap, we will rely heavily on AI-based solutions, premium web filtering technologies, and other crowd-sourced methods to help secure our networks and technologies.
The bottom line is, we should expect a multiplying effect on internet traffic. And as commerce and our daily lives become increasingly reliant on digital services—security simply cannot be an afterthought.





