Estimated Reading Time: 4 minutes
Earlier this week, Alphabet (Google) launched an interactive phishing quiz website aimed at educating users on the effectiveness of phishing and the specific dangerous elements within an email. Over the past couple of years, companies have looked to mitigate phishing attacks with a number of approaches including hardware-based authentication (e.g. Yubico) and a renewed approach security-oriented training and awareness.
But phishing attacks remain effective and can be difficult to spot and avoid, particularly on mobile devices. Last year, a report from Lookout revealed that 56% of mobile device users received and tapped on a phishing URL. This represents a significant gap in awareness and proper education over one of the top cybersecurity concerns—according to many cybersecurity experts.
The reason for the mobile security gap is largely due to simplified UI/UX choices conceal critical information like the hostname and full URL until clicked. But mobile phones and emails aren’t the only attack vectors and targets of phishing. And phishing attacks have growing increasingly sophisticated. Tools like Modlishka, a toolkit released earlier this month that was designed for penetration testing but has been found to be able to bypass two factor authentication (2FA), only stand to escalate the battle into 2019.
Phishing attacks continue to pose a significant security threat because they are effective—particularly targeted phishing attacks like spear phishing and whaling. They leverage social engineering to trick the user while taking advantage of the weakest link in the cybersecurity defense chain—human error.
They also remain lucrative. In a 2017 study from Keepnet, it was reported that the average successful spear phishing attack on a business could net the attacker up to $1.6 million (USD).
Targeted attacks aim to compromise business networks for enormous monetary gain—whether through ransomware, theft of valuable intellectual property. But even when unsuccessful, effects can be a financial burden. Costs of remediation and securing the network are increasingly expensive to businesses. In 2018, the IBM and Ponemon Institute “Cost of a Data Breach Report” estimated that the average global cost of a data breach now exceeds $3.8 million.
Phishing Education and Training: What To Look For
There are a number of ways users can be effectively phished on mobile, as well as other devices. And because many of these devices are always-on and always-connected, any lapse or misclick can have significant consequences.
So, users should always be “on guard” and aware of potentially malicious links and attacks in the form of:
- Personal or business emails
- Text Messaging & Other Messaging Services
- Advertisements (linked URLs) on websites and in apps
Voice phishing calls (fraudulent sales or support calls looking to acquire or verify personal information)
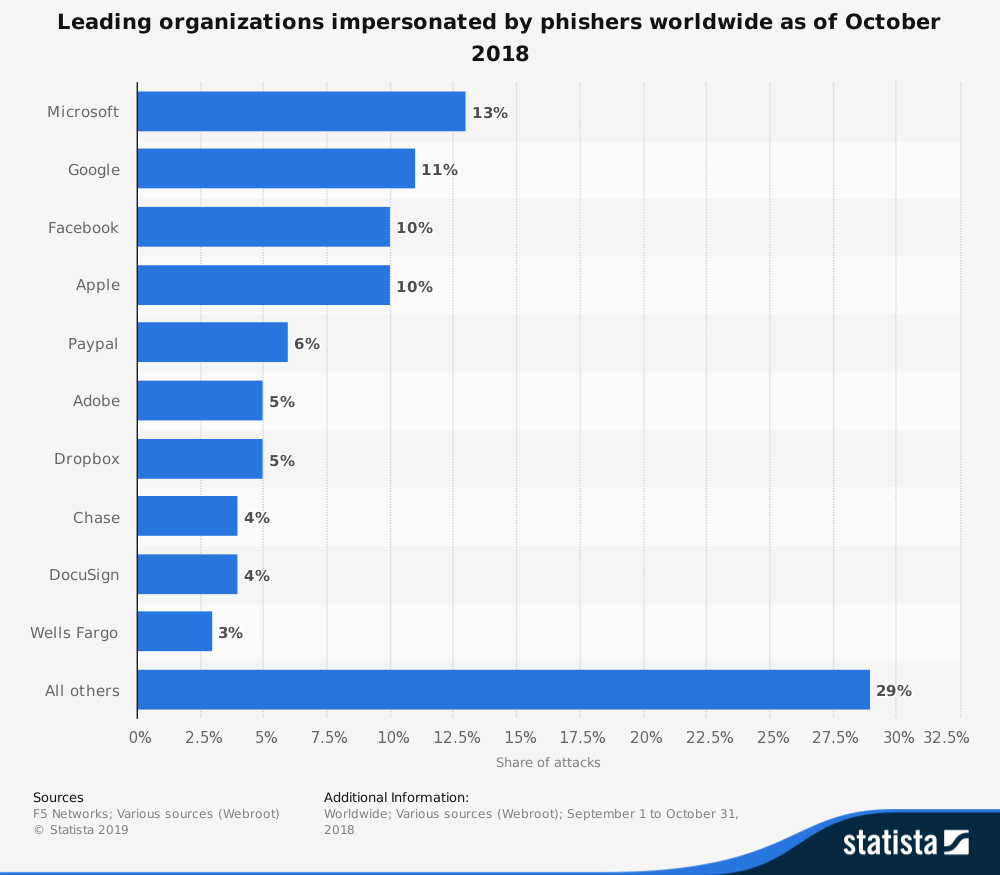
Always be wary of unsolicited emails and new contacts reaching out, as well as any unexpected attachments in emails—which could be harboring a malicious payload. According to Statista, the most impersonated brands include: Microsoft, Google, Facebook, Apple, Paypal, Adobe, Dropbox, Chase, and more.
If users are ever unsure, they should always scrutinize URLs for phishing indicators. Some attributes to look for that might indicate phishing include:
- URL contains a legitimate brand or company name but is not the official domain
- A legitimate company name is associated with an obscure top-level domain
- Any logos or branding on the page do not match the domain
- Top-level domain (e.g. .com, .org, .net) is hyphenated
- Resulting website includes large amount of ads/banners
Some additional steps that can be taken to spot phishing links include:
- Open the URL in a safe environment such as a sandbox to see where it takes you. Phishing URLs often redirect users many times.
- Look at whois.com registration data. Phishing URLs and domains often have a short lifetime and history.
- Translate the URL into unicode. Many phishing URLs leverage punycode and/or IDN homographs (replacing Latin characters with Cyrillic, Greek, or other letters to deceive potential victims)
Security Training & Awareness Just One Piece of the Puzzle
Ultimately, security awareness and continuous education—in addition to standard security policies in the workplace— will help businesses avoid falling victim to phishing scams in 2019. “Know before you go.” But it won’t completely mitigate risk. For that, businesses must maintain strong network security and will require next-generation defenses.
Advancements in AI-based phishing detection will help businesses to further level the playing field in 2019. By leveraging the latest advancements in machine learning and deep learning, image analysis, behavior anomaly detection, and neural networks
At zvelo, we are continuously experimenting and developing new ways of applying our AI-based categorization systems to identify phishing websites and pages, both faster and with higher accuracy.
For more information on forms of phishing attacks and other network security threats, check out our blog Network Security, Malicious Threats, and Common Computer Definitions. Some other important phishing and related definitions you should familiarize yourself with include:






