Leveraging Brand Vulnerability Assessment to Reduce Your Risk of a Cyber Attack
Having a strong online presence is a requirement of doing business these days. Unfortunately, that requirement makes you a target of threat actors. The bigger the brand and more expansive the digital presence — the bigger the target. Skilled “attackers” spend 80% of their time doing recon — searching for vulnerabilities and weaknesses in your site which may allow them access to exploit your Brand. Do you know how you look to attackers? Do you know the extent of your digital exposures and where your risk is greatest? You could…if you underwent a Brand Vulnerability Assessment. This post shares some basic information about Brand Vulnerability Assessment including what it is and why it’s used, how zvelo’s Cyber Threat Team approaches the assessment, and an example showing what you might uncover with a BVA.
What is a Brand Vulnerability Assessment and Why is it Used?
Simply put, a Brand Vulnerability Assessment (BVA) helps you understand the threat posture towards your brand. It involves performing a comprehensive review of your brand’s online presence to understand the extent of your digital exposures and then identify the greatest risks and vulnerabilities to your brand. Engaging a service to provide you with a Brand Vulnerability Assessment can be used to:
- Set up monitoring to mitigate and manage the exposures which leave your brand most at risk of an attack. Gaining a comprehensive understanding of your weaknesses allows you to take steps necessary to manage those vulnerabilities to reduce your risk of being attacked.
- Quickly identify and contain potential Phishing or Malicious threats to your brand before they escalate. While the goal is to avoid being attacked, in the event this does occur, leveraging a BVA and continuous monitoring allows you to identify potential and emerging threats in the early stages and put a stop to those threats before they have a lasting and potentially devastating impact on your brand.
- Understand potential liabilities, threat risks and exposures that accompany a particular brand. This can be incredibly useful for organizations in the mergers and acquisitions (M&A) process, as well as for advertising, marketing, or PR agencies looking to acquire top brands as clients.
zvelo’s Approach to Assessing Brand Vulnerabilities
zvelo’s approach to a Brand Vulnerability Assessment shares similar tactics used for External Threat Hunting — an additional Professional Services offering which we will blog about in the near future. Threat Hunting is defined as proactive activities to find vulnerabilities and potentially identify attackers in your network. Our Cyber Threat Intelligence experts leverage a wide range of internal proprietary methods, tools, as well as numerous open sources commonly used for External Threat Hunting to get a comprehensive understanding of how an attacker would view a brand’s internet presence. Basically, zvelo’s ‘good guys’ use the same Tactics, Techniques, and Procedures (TTP) as threat actors would, but instead of exploiting your weaknesses, we tell you how to fix them.
Example Use Case Scenario: Identify Typosquatting and Potential Phishing Attempt
One common starting point in performing a brand vulnerability assessment is to conduct threat hunting for phishing domains that are similar to a specified brand, organization, or the product and service offerings. Threat hunters use this tactic to identify potential instances of typosquatting. Typosquatting is a highly prevalent tactic used in phishing scams where the attacker stands up a website that is one letter or character off from what it should be. Using zvelo.com as an example, an attacker might stand up a website using zelo.com.
Typosquatting is intended to trick users into submitting credentials or downloading software which can enable an attacker to gain access to an individual’s account, or worse, entry into an organization’s network. Once an attacker gains access, they may use that to conduct research into the victim company and identify that the company uses Microsoft products for email, SharePoint, etc., and send a phishing email to an entire organization of users to penetrate the network more deeply in search of a higher payout.
To demonstrate what this could look like, we’ll use our own zvelo brand. In the screenshot below, our team went in search of websites that could potentially be typosquatting against our main website zvelo.com.
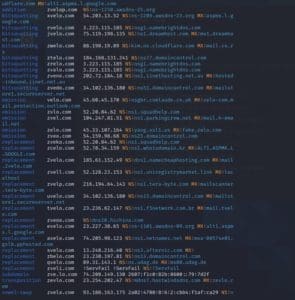
This screenshot shows numerous registered websites similar to zvelo.com, but instead using different techniques such as replacement, or omission typos to trick users. As you’ll see in the image, the variations include zveo.com, zveko.com, 2velo.com, etc.
Fortunately, in our case, we have the internal resources on hand to monitor these instances and take immediate action if/when necessary. After analyzing the above websites, our threat researchers found that some are parked, meaning they are not currently being used, while some are legitimate companies, and others are simply no longer active. The good news is that the results from this exercise confirmed there are no active phishing attacks against zvelo at this time — ‘at this time‘ being a key phrase!
The threat landscape evolves quickly and the adversarial TTPs may change from day to day. An inactive website which may have been a potential example of typosquatting against zvelo.com yesterday, may become active again at any point in time. If you have an online presence, the key is remembering, you are always a target. On the plus side, attackers like easy targets so by taking a proactive approach, like undergoing a brand vulnerability assessment, may be just the kind of resistance you need to prevent attacks from happening.





