zvelo Cyber Threat Intelligence Alert on Log4j: What You Need to Know
Threat Name: Log4j
Threat Type: IOC, Botnet, Critical Vulnerability
On Friday, December 9, 2021 Common Vulnerability Scoring System (CVSS) score 10.0 (critical) vulnerability for the open source Apache Log4j (https://logging.apache.org/log4j/2.x/) utility was released by researchers. Listed as Common Vulnerabilities (CVE) 2021-44228 (https://nvd.nist.gov/vuln/detail/CVE-2021-44228), this vulnerability was quickly weaponized and is being used in the wild to exploit exposed systems. For clarity, the Log4j library functions as a logging package for java-based web applications supporting variable and Application programming Interface (API) tracing. According to a variety of sources the primary vulnerable version of Log4j is version 2.x with 1.x affected to a lesser extent.
With this in mind, the exploits created for CVE 2021-44228 take advantage of the integration of the Log4j library into applications by injecting a Java Naming and Directory Interface (JNDI) lookup class with an included Lightweight Directory Access Protocol (LDAP) query command into exposed webservers. If an LDAP response is returned, the webserver is vulnerable to further exploitation. As this vulnerability can be exploited without the need to authenticate to the victim system and its reliability is high, the CVSS 10.0 score is warranted. This is shown in the following simplified graphic:
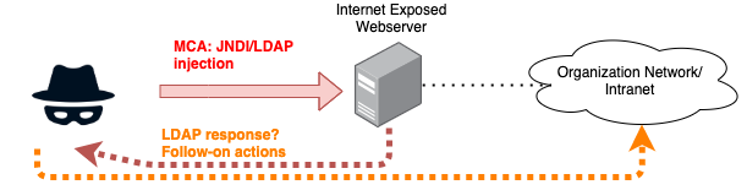
Almost immediately after CVE 2021-44228 was published a number of botnets including Muhstik and Mirai added JNDI/LDAP sequences to their scanning attack kit bag. Mirai is an Internet of Things (IoT) botnet that has been operating since October 2016. Muhstik is another IoT botnet that came on to the scene in 2018 targeting routers and related networking gear. As of Tuesday, December 14, 2021, the Muhstik botnet was observed delivering the “new” Khonsari ransomware into primarily Windows-based organizations that have linux-based servers in the environment. This type of sprawling expansion of Malicious Cyber Actors (MCA) use of a known vulnerability like the Log4j is not unheard of, and organizations can expect continued attempts to leverage variations for some time to come.
zvelo’s Detection & Coverage
With zvelo’s extensive dataset, current customers are protected from related attacks, specifically:
- Botnets leveraging the vulnerability in scanning and automated attacks: zvelo’s malicious detection engine ensured that IP-based URLs (individual IP address and full-path), along with any-related text-based URLs, were part of Malicious Detailed Data Feed (MDDF) almost immediately. In fact, many of the botnet-related IP addresses were already in MDDF and flowed to zveloDB several months ago.
- Existing callback sites and command and control (C2) nodes: once MCAs exploit a Log4j vulnerable system, they will look to establish connectivity via their existing malicious infrastructure. MDDF holds thousands of these related URLs spanning domains, full-paths, and IP addresses.
zvelo’s Cybersecurity Team is constantly monitoring the latest Cyber Threat Intelligence (CTI) from sources around the world to validate that these current threats are part of our growing dataset. Please contact zvelo for more information on what to do if you have been impacted by the Log4j, or if you have questions about how to best protect your organization from similar threats in the future.
For updated information, see the Log4j Vulnerability Update.





