Earlier this month WannaCry was named the world’s biggest cyberattack which hit at over 150 countries and infected over 300,000 machines across hospitals, universities, manufacturers, government agencies and other important centers. This nasty ransomware encrypted files on a victim’s hard drive and then popped up a warning screen that looks like this:
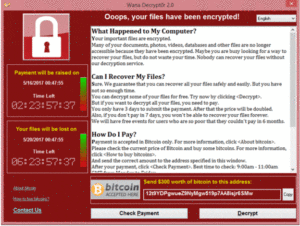
Users were prompted to provide bitcoin in exchange to decrypt their files – standard operational procedure with ransomware campaigns. Shortly after the WannaCry campaign was launched, a security researcher had located a way to largely shut the spread of it down with a kill switch, but this effort was too late to save an estimated 57,000 computers. Since locating that kill switch, there have been variants of WannaCry spotted in the wild, without a kill switch.
The WannaCry campaign wasn’t mounted on a zero-day vulnerability — or one that’s unknown to the information security community at large — but instead took advantage of some of the NSA developed vulnerabilities that were recently released by the “The Shadow Brokers” hacker group. Simply by following industry standard best practices around operating system patch management, this vulnerability would have been patched well before it would have been exploited. In other words, mission-critical operations, such as at hospitals and government agencies could have easily avoided WannaCry by simply patching their OS.
“The security of an operating system is largely controlled by its ability to stay updated. Since, hackers gain unauthorized access through an unpatched system, I cannot emphasize enough — systems should always be patched to avoid easily avoidable vulnerabilities.”
The majority of the machines that appear to have been impacted were unpatched Windows 7 machines and XP hosts. XP hosts were largely impacted due to the fact that Microsoft has discontinued automated patches for this unsupported operating system. In the wake of WannaCry, Microsoft took the unusual action of releasing a standalone patch for XP that users must download and run manually, because the Windows Update no longer functions for XP systems. Windows 7 hosts which were correctly patched avoided this issue altogether when the patch for this vulnerability came out a few weeks ago, and in fact, Windows 10 hosts weren’t impacted by this vulnerability at all.
So which systems got caught here and which got a pass? Windows XP and Windows 7 users who were, for whatever reason, holding off on patches were vulnerable. Although there may be operational justifications for not taking the step to patch their OS with enterprise systems — in light of WannaCry these risky practices are now being strongly challenged with an eye toward change. The security of an operating system is largely controlled by its ability to stay updated. Since, hackers gain unauthorized access through an unpatched system, I cannot emphasize enough — systems should always be patched to avoid easily avoidable vulnerabilities.
Lessons learned from WannaCry?
Here are my top 4 suggested best practices or takeaways to guard against ransomware attacks:
- Patch all of your systems on an automated basis. Check that your systems have been configured to download and install patches as soon as they are released. Although this is the default for Windows 10 systems, be sure to confirm automated updates on XP, Windows 7 and Windows 8.1, and Apple Mac systems. (Yes, even Macs can get malware too.)

- Backup your systems. If you have a tested working backup scheme, combating ransomware can be easy. You simply restore to a known good, working system from an earlier point in time after fully patching to avoid re-infection. A backup is the cheapest and easiest “insurance” you can buy for your critical systems, but requires some work on your behalf to implement and validate.
- Ensure that the rest of the software installed on your system is up to date. While Windows Update takes care of the operating system when correctly enabled, other critical software needs to be updated as well. Include in your list to update: your internet browser and any plugins needed to use the web – like, Firefox, Chrome, Acrobat Reader and Adobe Flash, etc. Also, it is a very good idea uninstall things you aren’t actually using so that you don’t have to be sure that they are updated.
- Block SMB inbound/outbound on your firewall at the Internet edge. Unfortunately, this is a more complex remedy in which you may need to consult with your firewall administrator prior to implementing. However it is very worth the effort since many types of ransomware are spread via the Windows SMB service, this action can keep infected systems from spreading this specific vulnerability to other unpatched systems.
In this blog entry, I’ve provided you with some easy to implement best practices that you can use to fight ransomware, including WannaCry.
Although, some of these tips are merely readdressing the basics, after attacks such as WannaCry, we know some large organizations and individuals have not practiced them as closely as they should have. Again, I highly suggest you adopt a “always patch” mentality, especially on business critical systems. Any impact caused by the rare Microsoft patch that causes a small issue, is far outweighed by potential data loss issues caused by vulnerabilities exploited by ransomware such as WannaCry. Patch NOW!





