by Eric Watkins, Senior Malicious Detection Researcher at zvelo
Ransomware and malware attacks are not going to go away anytime soon, rather they are becoming increasingly more common. Last month we wrote about the malware ransomware campaign, WannaCry and now we’ll discuss yesterday’s ransomware campaign Petya which exploits another one of the many vulnerabilities released as part of the NSA toolset.
What is Petya?
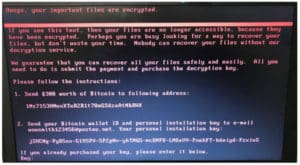
The Petya malware ransomware screen
Petya is a ransomware campaign that has been updated to take advantage of an exploit named EternalBlue (named this by the NSA as part of their toolset). This exploit takes advantage of a vulnerability in the Server Message Block (SMB) protocol. Back on Tuesday, March 14, 2017, Microsoft issued security bulletin MS17-010 to patch EternalBlue. (Note: this campaign is currently only targeting Microsoft Windows systems.)
How does Petya work?
First it infects the computer’s master boot record and the forces a reboot. Then at startup, the Master File Table of the NTFS file system is encrypted, and the end user is shown a message demanding a payment made in Bitcoin. While this campaign has spread to other machines across the world it appears that the initial campaign was targeted at companies within the Ukraine. At one point, Petya even impacted the nuclear monitoring system around the Chernobyl site. Although the initial attack was targeted at a specific state or local, as demonstrated, malware can break away from its initial targets and spread to both other countries and other companies.
Why not just pay the ransom requested in Bitcoin?
While it might seem like “the easy way out” to simply pay the ransom and get your files back, sometimes, in actuality, does not work that easily. Some well-intended administrators in Germany shut down the e-mail account associated with the ransomware, so that even if someone obtained Bitcoin and send it to the requested account, the campaign admin can’t respond with the unlock code. Our suggestion is to never pay a malware ransom and instead rely on your patching procedures and validated backup scheme.
Suggested Best Practices for Malware Attack Mitigation
Since the patch for this vulnerability has been out since March 14 and source of the issue is systems that were not adequately updated, we can reiterate the same suggestions we prepared with WannaCry to mitigate ransomware campaigns (just updated for here for Petya).
- Patch all of your systems on an automated basis.
Check that your systems have been configured to download and install patches as soon as they are released. Although this is the default for Windows 10 systems, be sure to confirm automated updates on XP, Windows 7 and Windows 8.1, and Apple Mac systems.
A robust patching system should make a malware campaign based on known vulnerabilities like Petya a non-issue for your organization. Ensure that the MS17-010 patch has been applied.
- Backup your systems.
If you have a tested working backup scheme, combating ransomware can be easy. You simply restore to a known good, working system from an earlier point in time after fully patching to avoid re-infection. A backup is the cheapest and easiest “insurance” you can buy for your critical systems, but requires some work on your behalf to implement and validate.
If you become infected with Petya, a solid backup schema will allow you to restore service without paying a ransom.
- Ensure that the rest of the software installed on your system is up to date.
While Windows Update takes care of the operating system when correctly enabled, other critical software needs to be updated as well. Include in your list to update: your internet browser and any plugins needed to use the web such as Firefox, Chrome, Acrobat Reader and Adobe Flash, etc. Also, it is a very good idea uninstall things you aren’t actually using so that you don’t have to be sure that they are updated.
While Petya is focused on a Microsoft Operating System vulnerability, there is no guarantee that the next popular malware outbreak won’t target one of these popular programs.
- Block SMB inbound/outbound on your firewall at the Internet edge.
Unfortunately, this is a more complex remedy in which you may need to consult with your firewall administrator prior to implementing. However it is very worth the effort since many types of ransomware are spread via the Windows SMB service, this action can keep infected systems from spreading this specific vulnerability to other unpatched systems.
The US-CERT organization has even recommended you disable this protocol system wide.
So, twice in two months we’ve talked about malware and it’s our sincere hope that your organization has already implemented these industry best practices around securing your systems and backing up your critical data. The persistence of these campaigns in attacking known vulnerabilities speaks to the success with which they are finding organizations that are still vulnerable and the weight and care we should all be putting into preparing ourselves for these attacks.





